Objectives
Identify the processes running on a computer, the protocol they are using, and their local and remote port addresses.
Background / Scenario
For a hacker to establish a connection to a remote computer, a port must be listening on that device. This may be due to infection by malware, or a vulnerability in a legitimate piece of software. A utility, such as TCPView, can be used to detect open ports, monitor them in real-time, and close active ports and processes using them.
Required Resources
- PC with Internet access
- TCPView software
Step 1: Download and install the TCPView software.
a. Click on the link below to reach the download page for TCPView.
http://technet.microsoft.com/en-us/sysinternals/tcpview.aspx
b. Create a folder on the desktop named “TCPView”.
c. Extract the contents of the zip to this new folder.
d. Double-click the Tcpview Application to start it.
e. Finally, Agree to the software license terms.
Step 2: Answer the following questions.
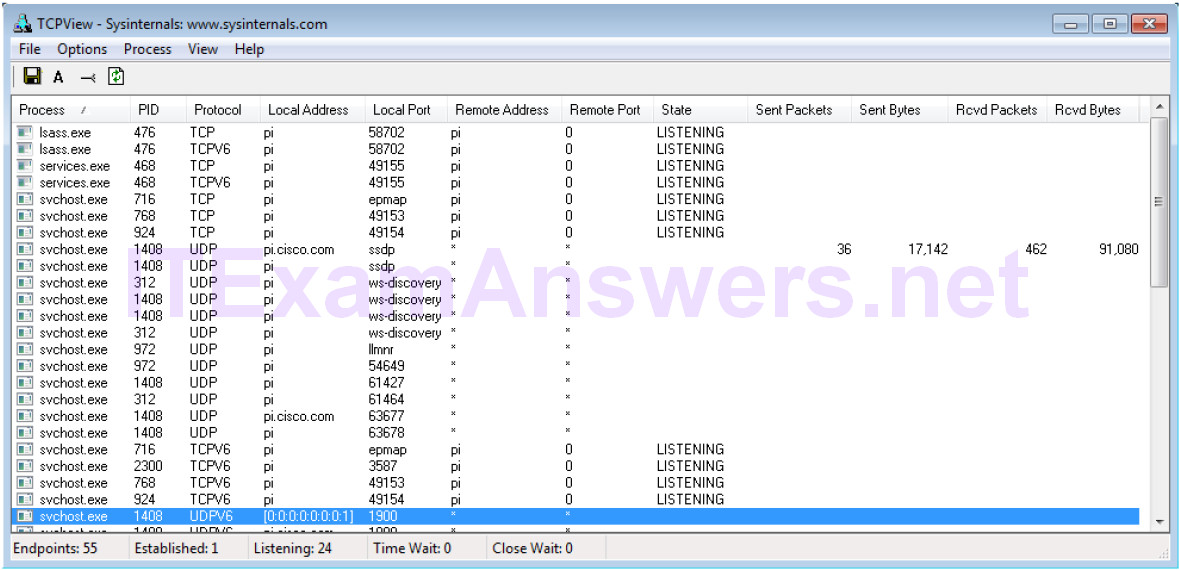
a. How many Endpoints are listed?
Answers may vary, 55.
b. How many are Listening?
Answers may vary, 24
c. How many Endpoints are Established?
Answers may vary, 1
Step 3: Use a browser and observe the TCPView window.
a. Open the Options menu and click “Always on Top”.
Note: Use the Help section of the program to help you answer the following questions.
b. Open any browser.
What happens in the TCPView window?
Answers may vary, multiple browser processes open and turn green across the screen, then some may turn to yellow, red, or white.
c. Browse to cisco.com.
What happens in the TCPView window?
Answers may vary, more browser processes open as green across the screen, then some may turn to yellow, red, or white.
d. Close the browser.
What happens in the TCPView window?
Answers may vary, after some time, multiple browser processes turn red as they close.
What do you think the colors mean?
Answers may vary, green lines indicate starting processes, yellow lines indicate processes that are waiting to open or close, red lines indicate processes that are closing, and white lines indicate processes that are running.
Note: To close a process directly, right-click the process and choose End Process. Using this method can cause a program or the operating system to become unstable. Only end processes that you know are safe to end. This method can be used to stop malware from communicating.
