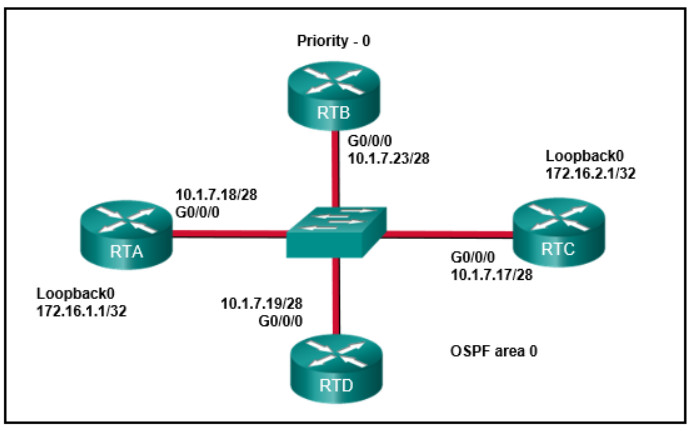
CCNPv8 ENCOR (Version 8.0) – OSPF Exam Answers Chapters 8 – 10: OSPF Exam Answers 1. What is the function of the OSPF LSR packet? It is used to confirm the receipt of LSUs. It is used to check the database synchronization between routers. It is used by the receiving routers to request more information about any entry in the LSDB. It is used to establish and maintain adjacency with other OSPF routers. Hint/Explanation: LSR packets are used by OSPF routers to request link-state database information from a neighbor. 2. What are two characteristics of OSPF areas? (Choose two.) All…
Author: CCNA Security
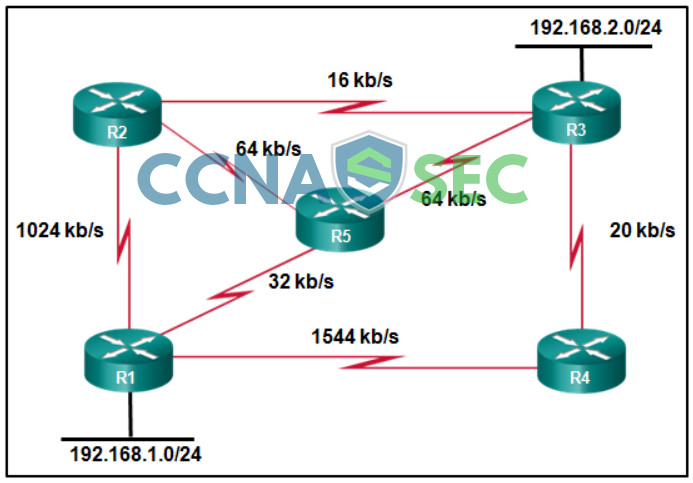
CCNPv8 ENCOR (Version 8.0) – Routing Essentials and EIGRP Exam Answers Chapters 6 – 7: Routing Essentials and EIGRP Exam Answers 1. Which type of routing protocol uses LSAs and TLVs to support extended features? distance vector link-state path vector hybrid Hint/Explanation: Link-state routing protocols include capabilities such as LSAs for OSPF and TLVs (type/length/value) for IS-IS that allow them to support extended features. 2. What are two characteristics of link-state routing protocols? (Choose two.) They periodically send full routing table updates to directly connected neighbors. They use path attributes to determine the best loop-free path. They can load balance…
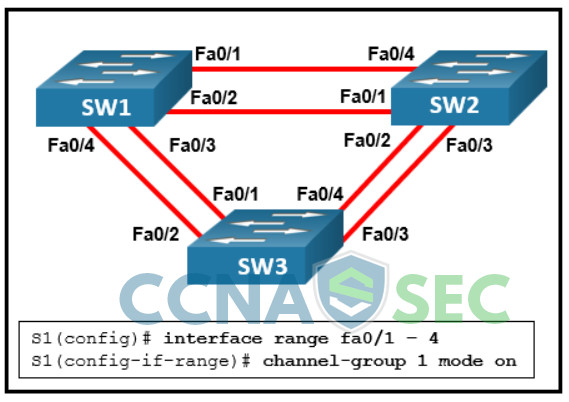
CCNPv8 ENCOR (Version 8.0) – L2 Redundancy Exam Answers Chapters 1 – 5: L2 Redundancy Exam Answers 1. What is the goal of Layer 3 switching? to process packets at Layer 2 switching speeds while utilizing the scalability of routing to provide a better path to the Internet without using routing protocols to integrate all of the networking functions into one device to implement the routing process by using routed protocols Hint/Explanation: Switches that perform Layer 3 switching process packets at Layer 2 hardware speeds while providing the scalability of routing. 2. Which two statements are true about routed ports…
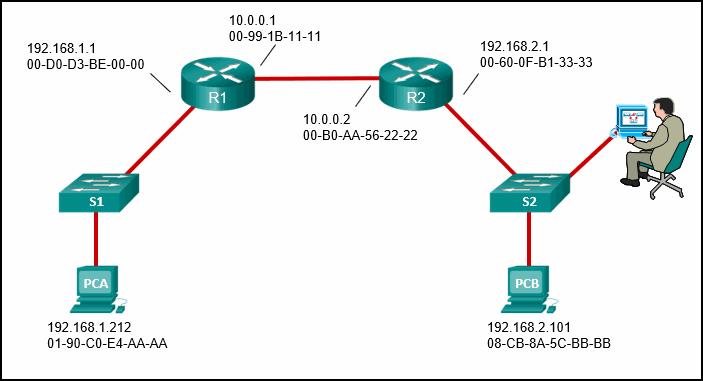
More Questions: Network Security ( Version 1) – Network Security 1.0 Final Exam 1. In the video that describes the anatomy of an attack, a threat actor was able to gain access through a network device, download data, and destroy it. Which flaw allowed the threat actor to do this? a flat network with no subnets or VLANs improper physical security to gain access to the building lack of a strong password policy open ports on the firewall Hint/Explanation: The company had a flat network with no subnets. The threat actor was able to access and destroy all kinds of…
More Questions: Modules 1 – 4: Securing Networks Group Exam Answers 1. Which two statements describe access attacks? (Choose two.) Password attacks can be implemented by the use of brute-force attack methods, Trojan horses, or packet sniffers. Trust exploitation attacks often involve the use of a laptop to act as a rogue access point to capture and copy all network traffic in a public location, such as a wireless hotspot. Buffer overflow attacks write data beyond the allocated buffer memory to overwrite valid data or to exploit systems to execute malicious code. To detect listening services, port scanning attacks scan…
CyberOps Associates v1.0 – Skills Assessment Introduction You have been hired as a junior security analyst. As part of your training, you were tasked to determine any malicious activity associated with the Pushdo trojan. You will have access to the internet to learn more about the events. You can use websites, such as VirusTotal, to upload and verify threat existence. The tasks below are designed to provide some guidance through the analysis process. You will practice and be assessed on the following skills: Evaluate event alerts using Squil and Kibana. Use Google search as a tool to obtain intelligence on…
CyberOps Associate (Version 1.0) – CyberOps Associate 1.0 Final Exam Answers 1. The definition of computer security incidents and related terms element is in which part of the incident response plan? policy plan procedure 2. The strategy and goals element is in which part of the incident response plan? plan procedure policy 3. The organizational structure and definition of roles, responsibilities, and levels of authority element is in which part of the incident response plan? policy plan procedure 4. The prioritization and severity ratings of incidents element is in which part of the incident response plan? policy plan procedure 5.…
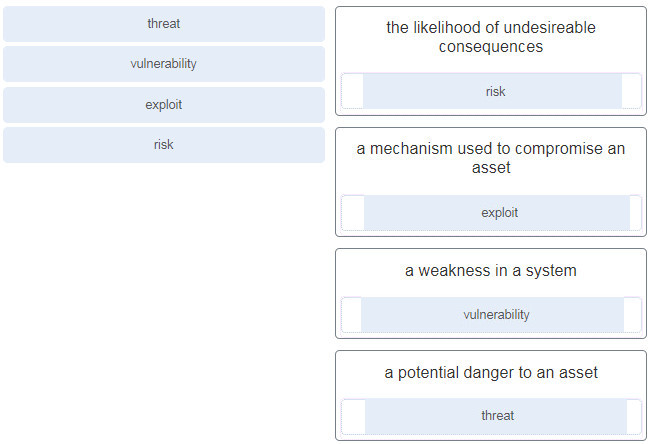
CyberOps Associate (Version 1.0) – CyberOps Associate 1.0 Practice Final exam Answers 1. When real-time reporting of security events from multiple sources is being received, which function in SIEM provides capturing and processing of data in a common format? log collection normalization aggregation compliance 2. What is the value of file hashes to network security investigations? They ensure data availability. They assure nonrepudiation. They offer confidentiality. They can serve as malware signatures. 3. Which technology is an open source SIEM system? StealthWatch ELK Splunk Wireshark 4. Match the security concept to the description. 5. What are the two important components…
28.4.13 Lab – Incident Handling (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Apply your knowledge of security incident handling procedures to formulate questions about given incident scenarios. Background / Scenario Computer security incident response has become a vital part of any organization. The process for handling a security incident can be complicated and involve many different groups. An organization must have standards for responding to incidents in the form of policies, procedures, and checklists. To properly respond to a security incident, the security analyst must be trained…