CyberOps Associate (Version 1.0) – Modules 3 – 4: Operating System Overview Group Exam 1. When a user makes changes to the settings of a Windows system, where are these changes stored? win.ini Control Panel boot.ini Registry 2. Which user account should be used only to perform system management and not as the account for regular use? guest power user standard user administrator 3. What is the purpose of entering the netsh command on a Windows PC? to configure networking parameters for the PC to change the computer name for the PC to create user accounts to test the hardware…
Author: CCNA Security
CyberOps Associate (Version 1.0) – Modules 1 – 2: Threat Actors and Defenders Group Exam Answers 1. Which personnel in a SOC is assigned the task of verifying whether an alert triggered by monitoring software represents a true security incident? Tier 1 personnel Tier 2 personnel Tier 3 personnel SOC Manager 2. After a security incident is verified in a SOC, an incident responder reviews the incident but cannot identify the source of the incident and form an effective mitigation procedure. To whom should the incident ticket be escalated? the SOC manager to ask for other personnel to be assigned…
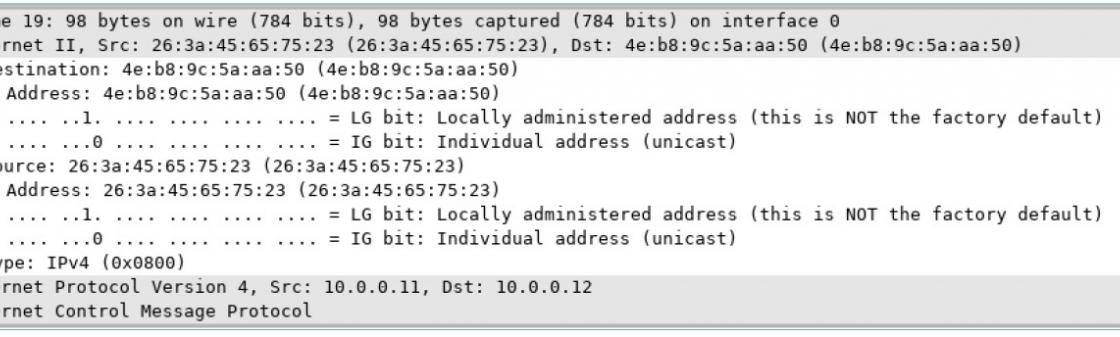
Mininet Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with each other, data flows down the Open Systems Interconnection (OSI) layers and is encapsulated into a Layer 2 frame. The frame composition is dependent on the media access type. For example, if the upper layer protocols are TCP and IP and the media access is Ethernet, then the Layer 2 frame encapsulation will be Ethernet II. This is typical for a LAN environment. When learning about Layer…
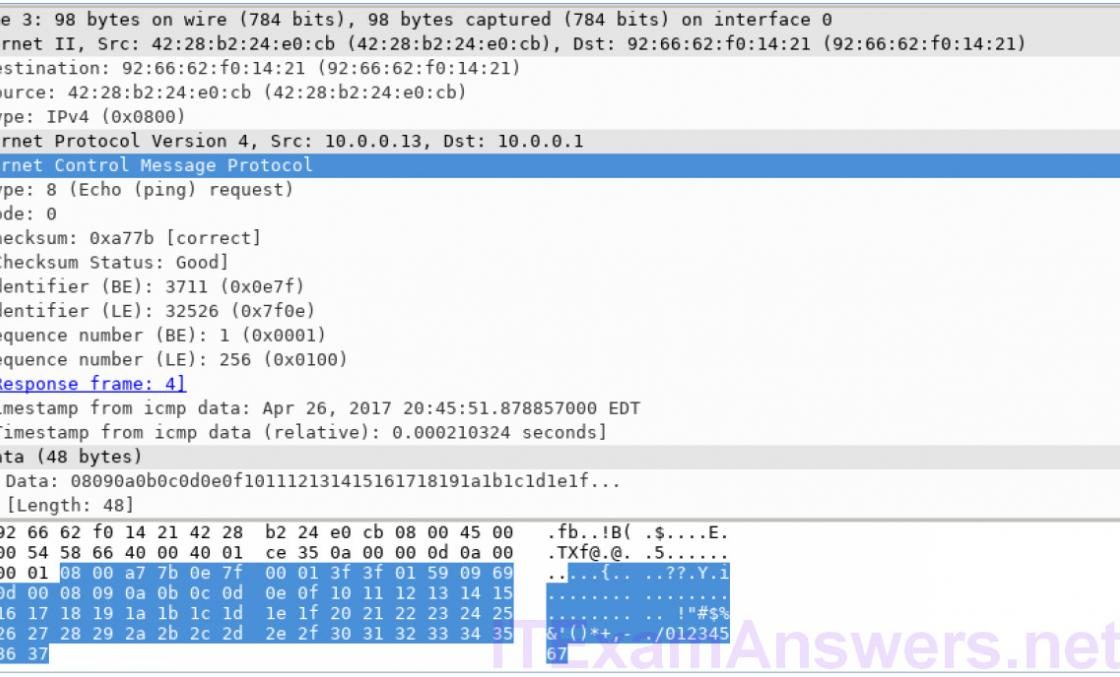
Mininet Topology Objectives Part 1: Install and Verify the Mininet Topology Part 2: Capture and Analyze ICMP Data in Wireshark Background / Scenario The CyberOps VM includes a Python script that, when you run it, will set up and configure the devices shown in the figure above. You will then have access to four hosts, a switch, and a router inside your one VM. This will allow you to simulate a variety of network protocols and services without having to configure a physical network of devices. For example, in this lab you will use the ping command between two hosts…
Objectives Part 1: Verifying Network Connectivity Using Ping Part 2: Tracing a Route to a Remote Server Using Traceroute Part 3: Trace a Route to a Remote Server Using Web-Based Traceroute Tool Background Tracing a route will list each routing device that a packet crosses as it traverses the network from source to destination. Route tracing is typically executed at the command line as: tracert <destination network name or end device address> (Microsoft Windows systems) or traceroute <destination network name or end device address> (Unix and similar systems) The traceroute (or tracert) tool is often used for network troubleshooting. By…
Objectives In this lab, you will use familiarize yourself with Linux filesystems. Required Resources CyberOps Workstation VM Part 1: Exploring Filesystems in Linux The Linux filesystem is one of its most popular features. While Linux supports many different types of filesystems, this lab focuses on the ext family, one the most common filesystems found on Linux. Step 1: Access the command line. Launch the CyberOps Workstation VM and open a terminal window. Step 2: Display the filesystems currently mounted. Filesystems must be mounted before they can be accessed and used. In computing, mounting a filesystem means to make it accessible…
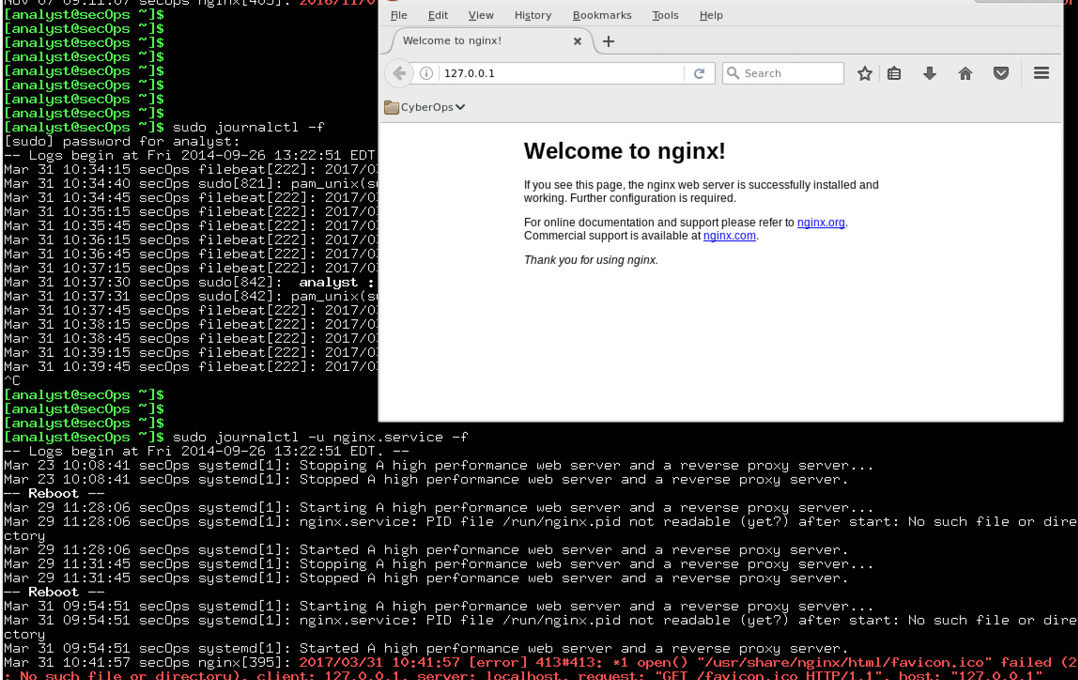
Introduction In this lab, you will get familiar with locating and manipulating Linux log files. Required Resources CyberOps Workstation Virtual Machine Part 1: Log File Overview Log files (also spelled logfiles), are files used by computers to log events. Software programs, background processes, services, or transactions between services, including the operating system itself, may generate such events. Log files are dependent on the application that generates them. It is up to the application developer to conform to log file convention. Software documentation should include information on its log files. Step 1: Web server log file example Because log files are…
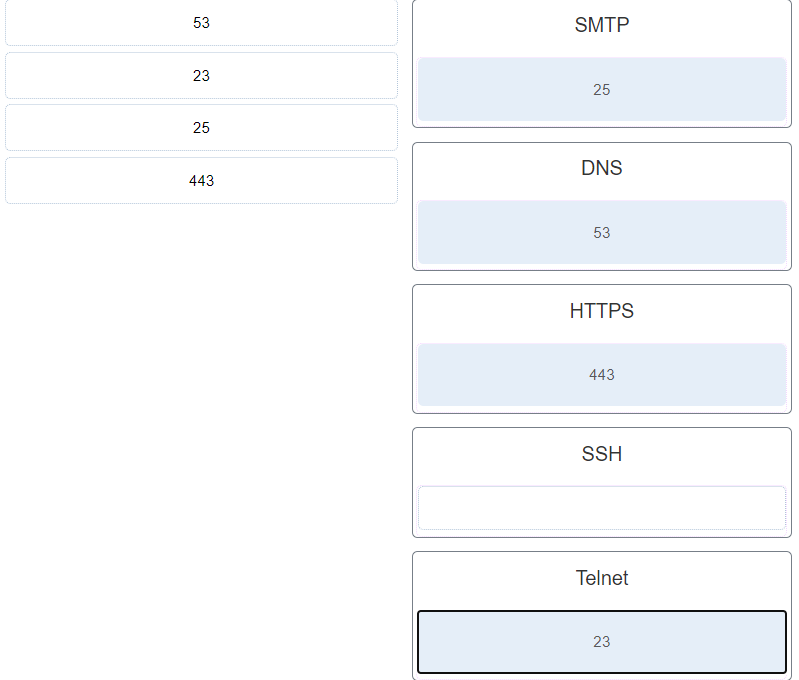
Introduction In this lab, you will use the Linux command line to identify servers running on a given computer. Recommended Equipment CyberOps Workstation Virtual Machine Part 1: Servers Servers are essentially programs written to provide specific information upon request. Clients, which are also programs, reach out to the server, place the request and wait for the server response. Many different client-server communication technologies can be used, with the most common being IP networks. This lab focuses on IP network-based servers and clients. Step 1: Access the command line. a. Log on to the CyberOps Workstation VM as the analyst, using…
Introduction In this lab, you will use the Linux command line to manage files and folders, and perform some basic administrative tasks. Recommended Equipment CyberOps Workstation Virtual Machine Part 1: Shell Basics The shell is the term used to refer to the command interpreter in Linux. Also known as Terminal, Command Line and Command Prompt, the shell is very powerful way to interact with a Linux computer. Step 1: Access the Command Line a. Log on to the CyberOps Workstation VM as the analyst using the password cyberops. The account analyst is used as the example user account throughout this…