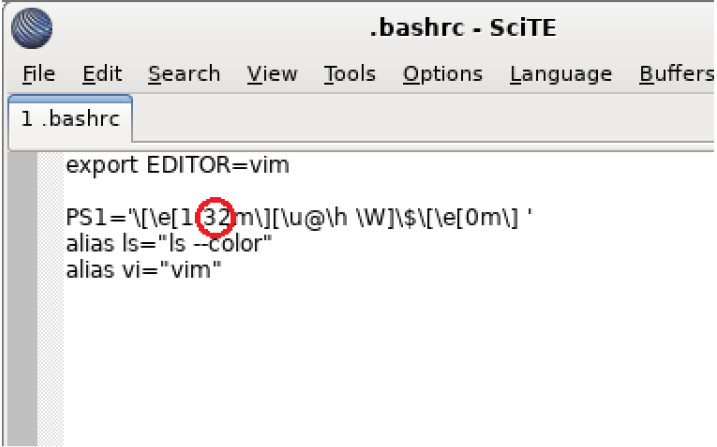
Introduction In this lab, you will get familiar with Linux command line text editors and configuration files. Required Resources CyberOps Workstation Virtual Machine Part 1: Graphical Text Editors Before you can work with text files in Linux, you must get familiar with text editors. Text editors are one of the oldest categories of applications created for computers. Linux, like many other operating systems, has many different text editors, with various features and functions. Some text editors include graphical interfaces, while others are only usable via the command line. Each text editor includes a feature set designed to support a specific…
Author: CCNA Security
Introduction In this lab, you will use administrative tools to monitor and manage Windows system resources. Recommended Equipment A Windows PC with Internet access Part 1: Starting and Stopping the Routing and Remote Access service You will explore what happens when a service is stopped and then started. In this part, you will use routing and remote access service as the example service. This service allows the local device to become a router or a remote access server. a. Click Start > Search and select Control Panel > Click Network and Sharing Center. Note: If your Control Panel is set…
Introduction In this lab, you will explore Task Manager and manage processes from within Task Manager. Part 1: Working in the Processes tab Part 2: Working in the Services tab Part 3: Working in the Performance tab Background / Scenario The Task Manager is a system monitor program that provides information about the processes and programs running on a computer. It also allows the termination of processes and programs and modification of process priority. Required Resources A Windows PC with Internet access Part 1: Working in the Processes tab a. Open a command prompt and a web browser. Microsoft Edge…
Objectives The objective of the lab is to explore some of the functions of PowerShell. Background / Scenario PowerShell is a powerful automation tool. It is both a command console and a scripting language. In this lab, you will use the console to execute some of the commands that are available in both the command prompt and PowerShell. PowerShell also has functions that can create scripts to automate tasks and work together with the Windows Operating System. Required Resources 1 Windows PC with PowerShell installed and Internet access Step 1: Access PowerShell console. a. Click Start. Search and select powershell.…
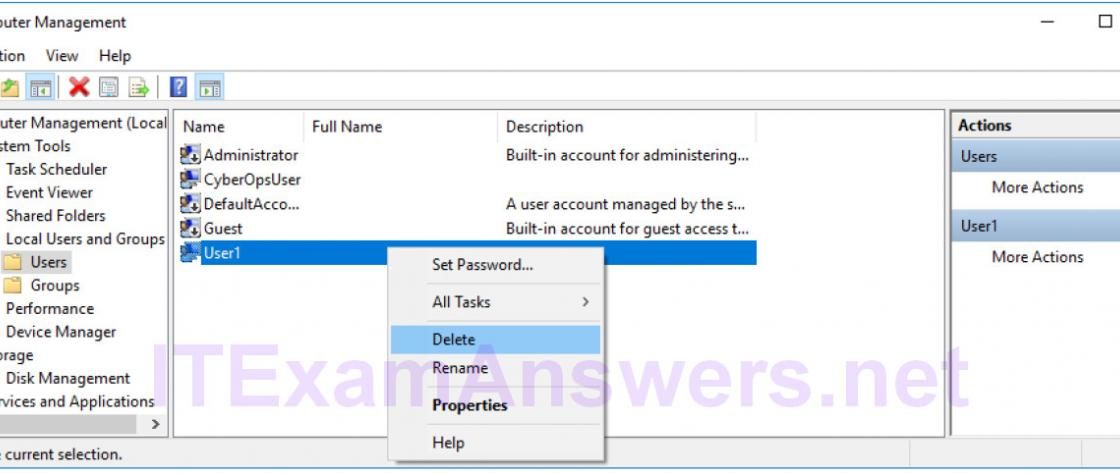
Introduction In this lab, you will create and modify user accounts in Windows. Part 1: Creating a New Local User Account Part 2: Reviewing User Account Properties Part 3: Modifying Local User Accounts Required Resources A Windows PC Part 1: Creating a New Local User Account Step 1: Open the User Account Tool. a. Log on to the computer with an Administrator account. The account CyberOpsUser is used in this example. b. Click Start > search Control Panel. Select User Accounts in the Small icons view. To change the view, select Small icons in the View by drop down list.…
Objectives In this lab, you will explore the processes, threads, and handles using Process Explorer in the SysInternals Suite. You will also use the Windows Registry to change a setting. Part 1: Exploring Processes Part 2: Exploring Threads and Handles Part 3: Exploring Windows Registry Required Resources 1 Windows PC with Internet access Part 1: Exploring Processes In this part, you will explore processes. Processes are programs or applications in execution. You will explore the processes using Process Explorer in the Windows SysInternals Suite. You will also start and observe a new process. Step 1: Download Windows SysInternals Suite. a.…
Objectives Research and analyze what it takes to become a network defender Background / Scenario In our technology-centric world, as the world gets more connected, it also gets less safe. Cybersecurity is one of the fastest growing and in-demand professions. Individuals in this field perform a wide variety of jobs including but not limited to consultation, investigation and program management services to mitigate risks through both internal and external sources. Cybersecurity professionals are required to evaluate, design and implement security plans, conduct in-depth fraud investigation and perform security research and risk assessment and propose solutions to potential security breaches. Individuals…
Objectives Research and analyze cyber security incidents Background / Scenario In 2016, it was estimated that businesses lost $400 million dollars annually to cyber criminals. Governments, businesses, and individual users are increasingly the targets of cyberattacks and cybersecurity incidents are becoming more common. In this lab, you will create three hypothetical cyber attackers, each with an organization, an attack, and a method for an organization to prevent or mitigate the attack. Note: You can use the web browser in virtual machine installed in a previous lab to research security issues. By using the virtual machine, you may prevent malware from…
Objectives Research and analyze IoT application vulnerabilities Background / Scenario The Internet of Things (IoT) consists of digitally connected devices that are connecting every aspect of our lives, including our homes, offices, cars, and even our bodies to the Internet. With the accelerating adoption of IPv6 and the near universal deployment of Wi-Fi networks, the IoT is growing at an exponential pace. Industry experts estimate that by 2020, the number of active IoT devices will approach 50 billion. IoT devices are particularly vulnerable to security threats because security has not always been considered in IoT product design. Also, IoT devices…