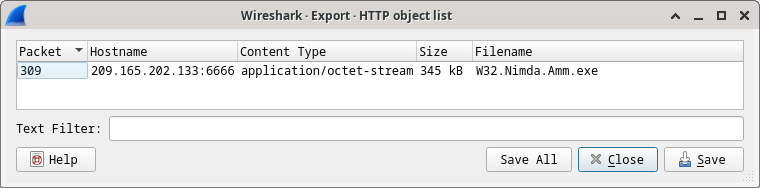
27.2.16 Lab – Investigating an Attack on a Windows Host (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives In this lab you will: Part 1: Investigate the Attack with Sguil Part 2: Use Kibana to Investigate Alerts This lab is based on an exercise from the website malware-traffic-analysis.net which is an excellent resource for learning how to analyze network and host attacks. Thanks to [email protected] for permission to use materials from his site. Note: This lab requires a host computer that can access the internet. Background / Scenario…
Author: CCNA Security
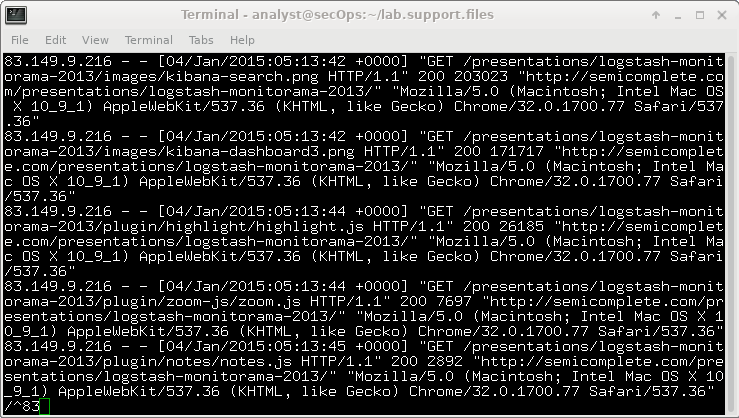
27.2.15 Lab – Investigating a Malware Exploit (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives In this lab you will: Part 1: Use Kibana to Learn About a Malware Exploit Part 2: Investigate the Exploit with Sguil Part 3: Use Wireshark to Investigate an Attack Part 4: Examine Exploit Artifacts This lab is based on an exercise from the website malware-traffic-analysis.net which is an excellent resource for learning how to analyze network and host attacks. Thanks to [email protected] for permission to use materials from his site. Note: This…
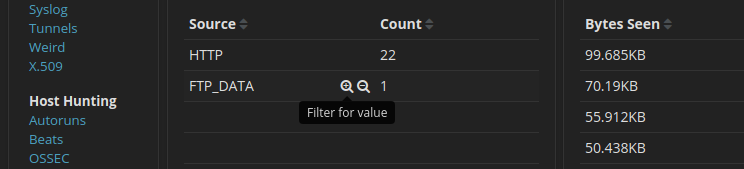
27.2.14 Lab – Isolate Compromised Host Using 5-Tuple (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives In this lab, you will review logs that were gathered during the exploitation of a documented vulnerability to determine the compromised hosts and file. Part 1: Review Alerts in Sguil Part 2: Pivot to Wireshark Part 3: Pivot to Kibana Background / Scenario The 5-tuple is used by IT administrators to identify requirements for creating an operational and secure network environment. The components of the 5-tuple include a source IP address and…
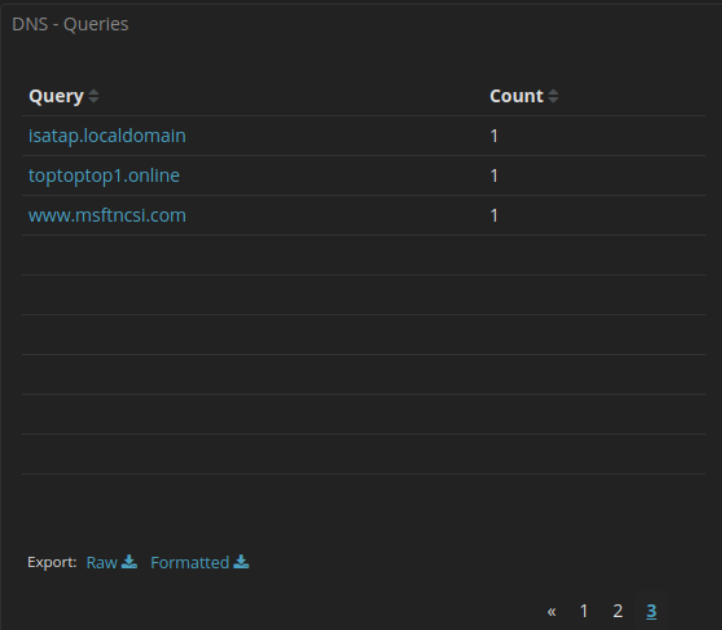
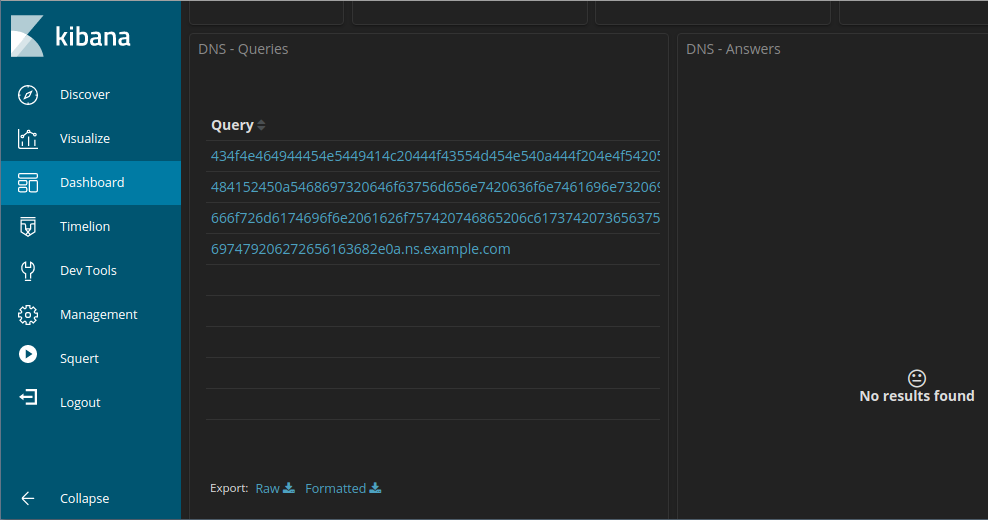
27.2.12 Lab – Interpret HTTP and DNS Data to Isolate Threat Actor (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives In this lab, you will review logs of an exploitation of documented HTTP and DNS vulnerabilities. Part 1: Investigate an SQL Injection Attack Part 2: Investigate DNS Data Exfiltration Background / Scenario MySQL is a popular database used by numerous web applications. Unfortunately, SQL injection is a common web hacking technique. It is a code injection technique where an attacker executes malicious SQL statements to control a web…
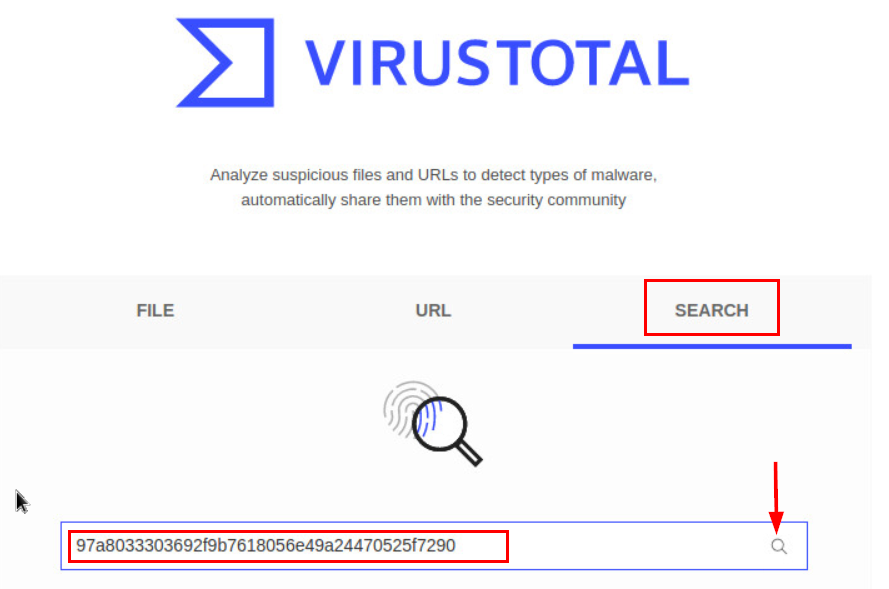
27.2.10 Lab – Extract an Executable from a PCAP (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Analyze Pre-Captured Logs and Traffic Captures Part 2: Extract Downloaded Files from PCAP Background / Scenario Looking at logs is very important, but it is also important to understand how network transactions happen at the packet level. In this lab, you will analyze the traffic in a previously captured pcap file and extract an executable from the file. Required Resources CyberOps Workstation virtual machine Instructions Part 1: Analyze Pre-Captured…
27.2.9 Lab – Regular Expression Tutorial (Instructor Version) Objectives In this lab, you will learn how to use regular expressions to search for desired strings of information. Part 1: Compete the regexone.com tutorial. Part 2: Describe the provided regular expression pattern. Part 3: Verify your answers. Background / Scenario A regular expression (regex) is a pattern of symbols that describes data to be matched in a query or other operation. Regular expressions are constructed similarly to arithmetic expressions, by using various operators to combine smaller expressions. There are two major standards of regular expression, POSIX and Perl. In this lab,…
27.1.5 Lab – Convert Data into a Universal Format (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Normalize Timestamps in a Log File Part 2: Normalize Timestamps in an Apache Log File Part 3: Log File Preparation in Security Onion Virtual Machine Background / Scenario This lab will prepare you to learn where log files are located and how to manipulate and view log files. Log entries are generated by network devices, operating systems, applications, and various types of programmable devices. A file containing a time-sequenced…
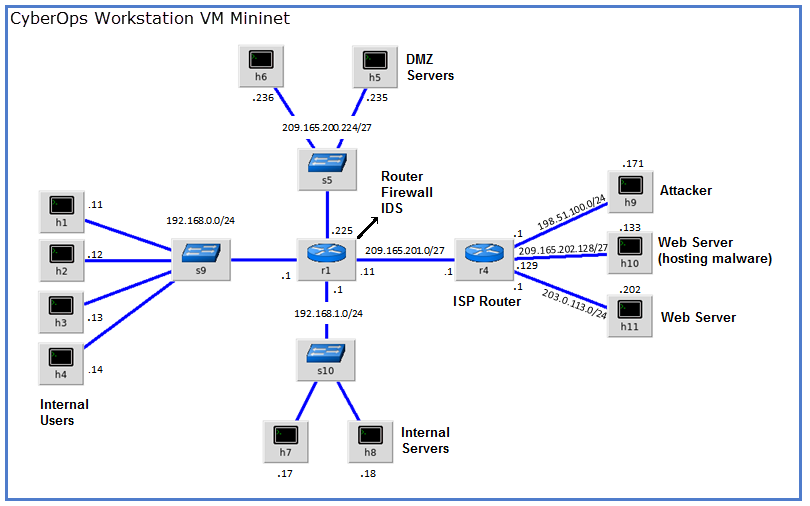
26.1.7 Lab – Snort and Firewall Rules (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Objectives Part 1: Preparing the Virtual Environment Part 2: Firewall and IDS Logs Part 3: Terminate and Clear Mininet Process Background / Scenario In a secure production network, network alerts are generated by various types of devices such as security appliances, firewalls, IPS devices, routers, switches, servers, and more. The problem is that not all alerts are created equally. For example, alerts generated by a server and alerts generated by a firewall will…
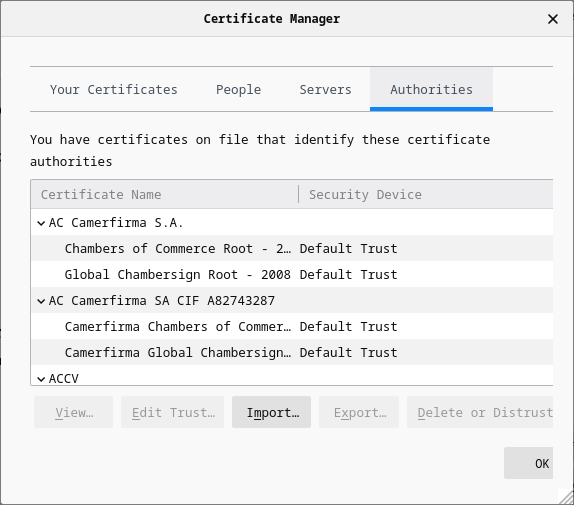
21.4.7 Lab – Certificate Authority Stores (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Certificates Trusted by Your Browser Part 2: Checking for Man-In-Middle Background / Scenario As the web evolved, so did the need for security. HTTPS (where the ‘S’ stands for security) along with the concept of a Certificate Authority was introduced by Netscape back in 1994 and is still used today. In this lab, you will: List all the certificates trusted by your browser (completed on your computer) Use hashes to detect if…