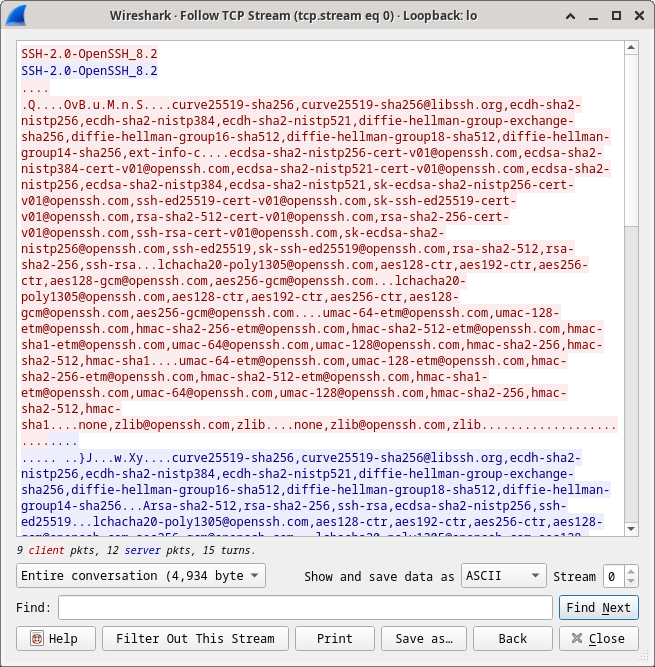
21.2.12 Lab – Examining Telnet and SSH in Wireshark (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Examine a Telnet Session with Wireshark Part 2: Examine an SSH Session with Wireshark Background / Scenario In this lab, you will configure a router to accept SSH connectivity and use Wireshark to capture and view Telnet and SSH sessions. This will demonstrate the importance of encryption with SSH. Required Resources CyberOps Workstation virtual machine Instructions Part 1: Examining a Telnet Session with Wireshark You will use Wireshark to…
Author: CCNA Security
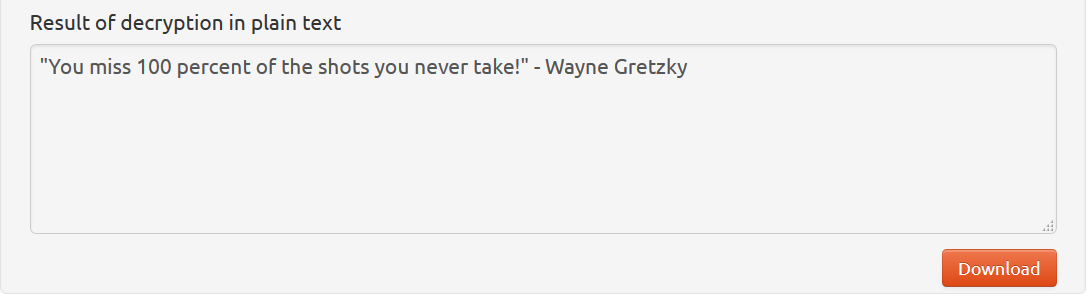
21.2.11 Lab – Encrypting and Decrypting Data Using a Hacker Tool (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Create and Encrypt Files Part 2: Recover Encrypted Zip File Passwords Background / Scenario What if you work for a large corporation that had a corporate policy regarding removable media? Specifically, it states that only encrypted zipped documents can be copied to portable USB flash drives. In this scenario, the Chief Financial Officer (CFO) is out-of-town on business and has contacted you in a panic with an…
21.2.10 Lab – Encrypting and Decrypting Data Using OpenSSL (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Encrypting Messages with OpenSSL Part 2: Decrypting Messages with OpenSSL Background / Scenario OpenSSL is an open source project that provides a robust, commercial-grade, and full-featured toolkit for the Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols. It is also a general-purpose cryptography library. In this lab, you will use OpenSSL to encrypt and decrypt text messages. Note: While OpenSSL is the de facto cryptography library today,…
21.1.6 Lab – Hashing Things Out (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Hashing a Text File with OpenSSL Part 2: Verifying Hashes Background / Scenario Hash functions are mathematical algorithms designed to take data as input and generate a fixed-size, unique string of characters, also known as the hash. Designed to be fast, hash functions are very hard to reverse; it is very hard to recover the data that created any given hash, based on the hash alone. Another important property of hash function…
21.0.3 Class Activity – Creating Codes (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives In this lab, you will create and encrypt messages using online tools. Part 1: Search for an online encoding and decoding tool. Part 2: Encrypt a message and email it to your lab partner. Part 3: Decrypt the ciphertext. Background / Scenario Secret codes have been used for thousands of years. Ancient Greeks and Spartans used a scytale (rhymes with Italy) to encode messages. Romans used a Caesar cipher to encrypt messages. A few…
17.2.7 Lab – Reading Server Logs (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Reading Log Files with Cat, More, Less, and Tail Part 2: Log Files and Syslog Part 3: Log Files and Journalctl Background / Scenario Log files are an important tool for troubleshooting and monitoring. Different application generates different log files, each one containing its own set of fields and information. While the field structure may change between log files, the tools used to read them are mostly the same. In this lab,…
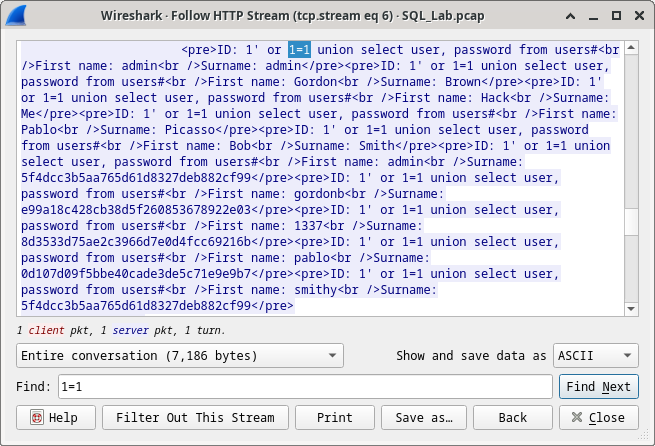
17.2.6 Lab – Attacking a mySQL Database (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives In this lab, you will view a PCAP file from a previous attack against a SQL database. Part 1: Open Wireshark and load the PCAP file. Part 2: View the SQL Injection Attack. Part 3: The SQL Injection Attack continues… Part 4: The SQL Injection Attack provides system information. Part 5: The SQL Injection Attack and Table Information Part 6: The SQL Injection Attack Concludes. Background / Scenario SQL injection attacks allow malicious…
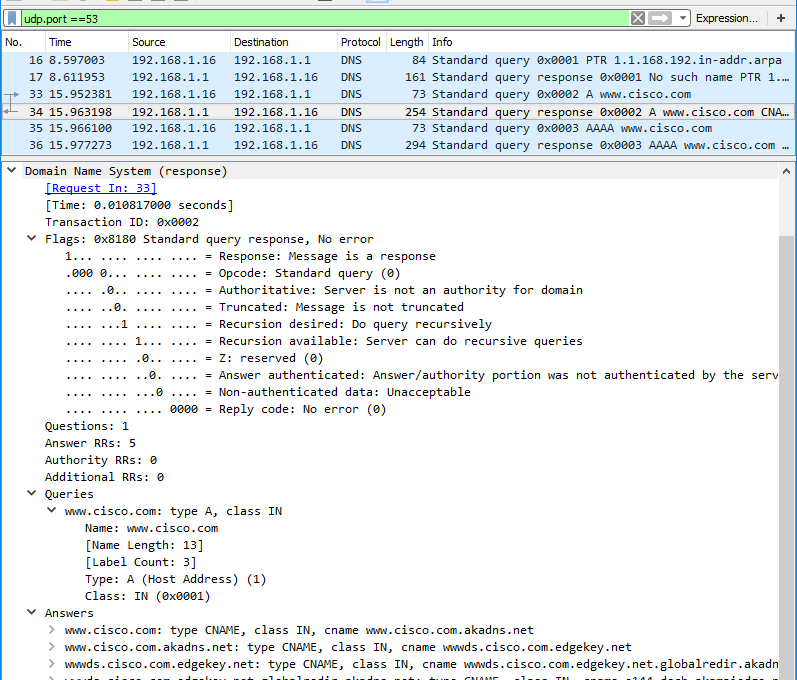
17.1.7 Lab – Exploring DNS Traffic (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Capture DNS Traffic Part 2: Explore DNS Query Traffic Part 3: Explore DNS Response Traffic Background / Scenario Wireshark is an open source packet capture and analysis tool. Wireshark gives a detailed breakdown of the network protocol stack. Wireshark allows you to filter traffic for network troubleshooting, investigate security issues, and analyze network protocols. Because Wireshark allows you to view the packet details, it can be used as a reconnaissance tool for…
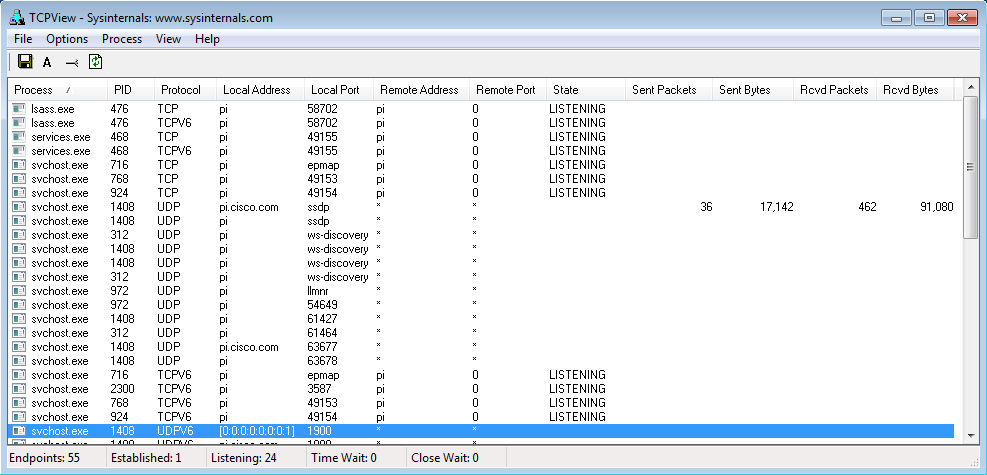
15.0.3 Class Activity – What’s Going On (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Identify the processes running on a computer, the protocol they are using, and their local and remote port addresses. Part 1: Download and install the TCPView software. Part 2: Answer the following questions. Part 3: Use a browser and observe the TCPView window. Background / Scenario For a hacker to establish a connection to a remote computer, a port must be listening on that device. This may be due to infection by malware,…