14.2.8 Lab – Social Engineering (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Research and identify social engineering attacks Background / Scenario Social engineering is an attack with the goal of getting a victim to enter personal or sensitive information, this type of attack can be performed by an attacker utilizing a keylogger, phishing email, or an in-person method. This lab requires the research of social engineering and the identification of ways to recognize and prevent it. Required Resources PC or mobile device with internet access Instructions Using…
Author: CCNA Security
14.1.11 Lab – Anatomy of Malware (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Research and analyze malware. Background / Scenario Malware, or malicious software, refers to a variety of malicious software programs that can be used to cause harm to computer systems, steal data, and bypass security measures. Malware can also attack critical infrastructure, disable emergency services, cause assembly lines to make defective products, disable electric generators, and disrupt transportation services. Security experts estimate that more than one million new malware threats are released each day. McAfee…
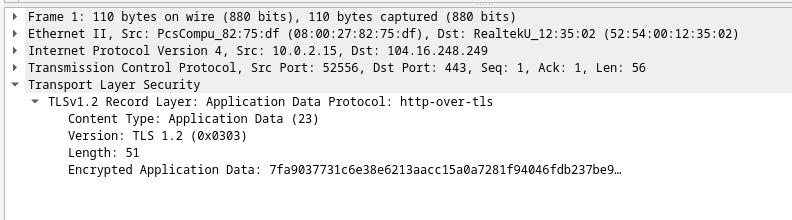
10.6.7 Lab – Using Wireshark to Examine HTTP and HTTPS Traffic (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Capture and view HTTP traffic Part 2: Capture and view HTTPS traffic Background / Scenario HyperText Transfer Protocol (HTTP) is an application layer protocol that presents data via a web browser. With HTTP, there is no safeguard for the exchanged data between two communicating devices. With HTTPS, encryption is used via a mathematical algorithm. This algorithm hides the true meaning of the data that is being exchanged.…
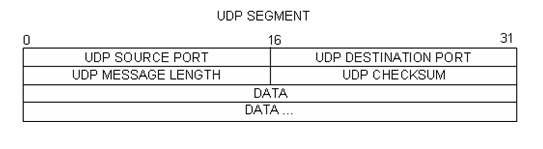
10.4.3 Lab – Using Wireshark to Examine TCP and UDP Captures (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology – Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of the CyberOps Workstation VM with internet access. Mininet Topology – Part 2 (TFTP) Objectives Part 1: Identify TCP Header Fields and Operation Using a Wireshark FTP Session Capture Part 2: Identify UDP Header Fields and Operation Using a Wireshark TFTP Session Capture Background / Scenario Two protocols in the TCP/IP…
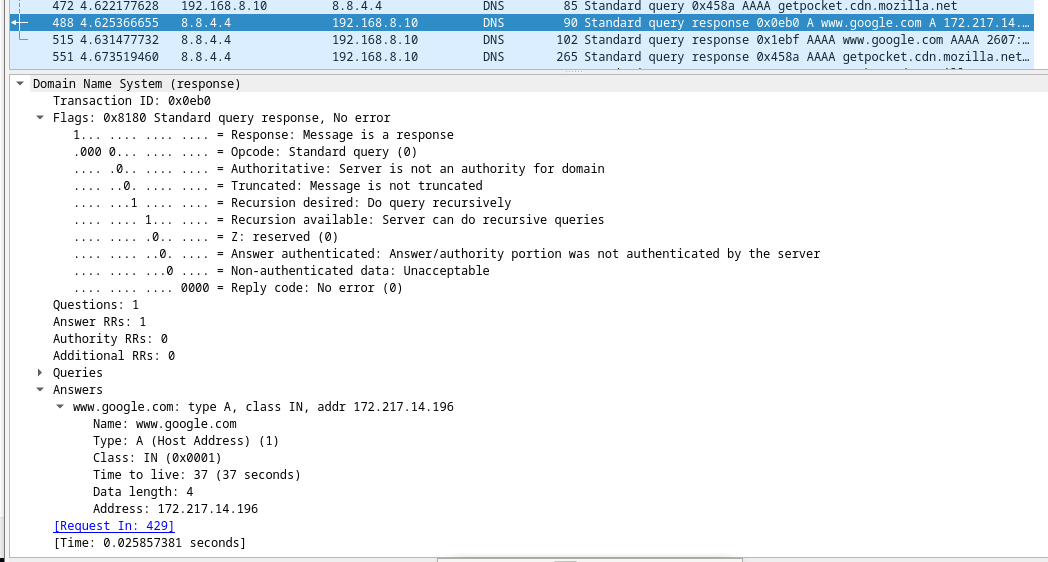
10.2.7 Lab – Using Wireshark to Examine a UDP DNS Capture (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Objectives Part 1: Record a PC’s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario When you use the internet, you use the Domain Name System (DNS). DNS is a distributed network of servers that translates user-friendly domain names like www.google.com to an IP address. When you type a website URL into your browser,…
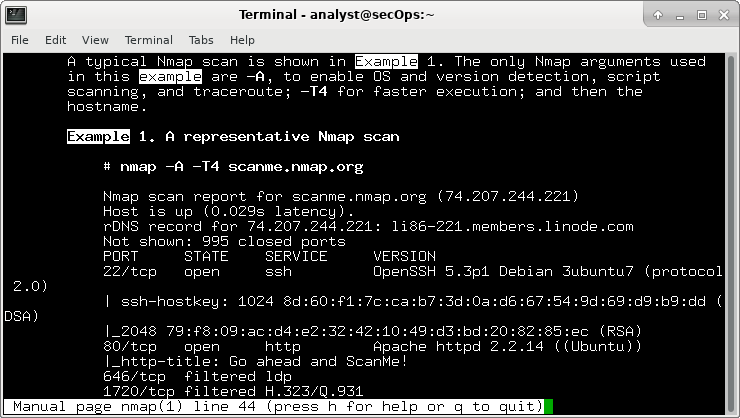
9.3.8 Lab – Exploring Nmap (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Objectives Part 1: Exploring Nmap Part 2: Scanning for Open Ports Background / Scenario Port scanning is usually part of a reconnaissance attack. There are a variety of port scanning methods that can be used. We will explore how to use the Nmap utility. Nmap is a powerful network utility that is used for network discovery and security auditing. Required Resources CyberOps Workstation virtual machine Internet access Instructions Part 1: Exploring Nmap In this part,…
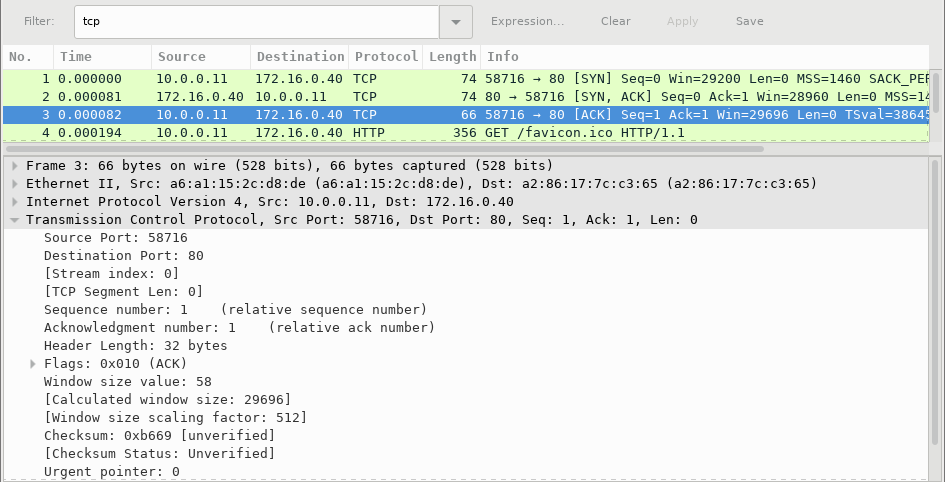
9.2.6 Lab – Using Wireshark to Observe the TCP 3-Way Handshake (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Mininet Topology Objectives Part 1: Prepare the Hosts to Capture the Traffic Part 2: Analyze the Packets using Wireshark Part 3: View the Packets using tcpdump Background / Scenario In this lab, you will use Wireshark to capture and examine packets generated between the PC browser using the HyperText Transfer Protocol (HTTP) and a web server, such as www.google.com. When an application, such as HTTP or File Transfer Protocol (FTP)…
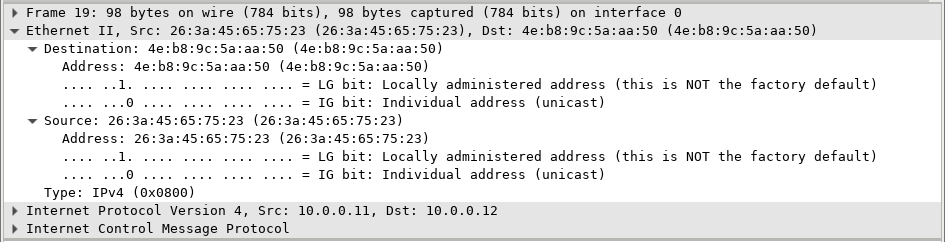
8.2.8 Lab – Using Wireshark to Examine Ethernet Frames (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Mininet Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with each other, data flows down the Open Systems Interconnection (OSI) layers and is encapsulated into a Layer 2 frame. The frame composition is dependent on the media access type. For example, if the upper layer protocols are TCP and…
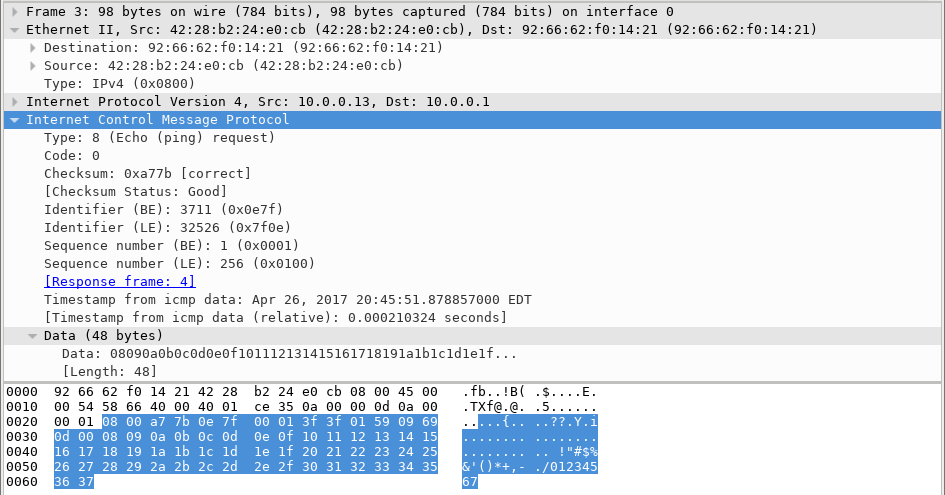
5.3.7 Lab – Introduction to Wireshark (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Mininet Topology Objectives Part 1: Install and Verify the Mininet Topology Part 2: Capture and Analyze ICMP Data in Wireshark Background / Scenario The CyberOps VM includes a Python script that, when you run it, will set up and configure the devices shown in the figure above. You will then have access to four hosts, a switch, and a router inside your one VM. This will allow you to simulate a variety of network protocols…