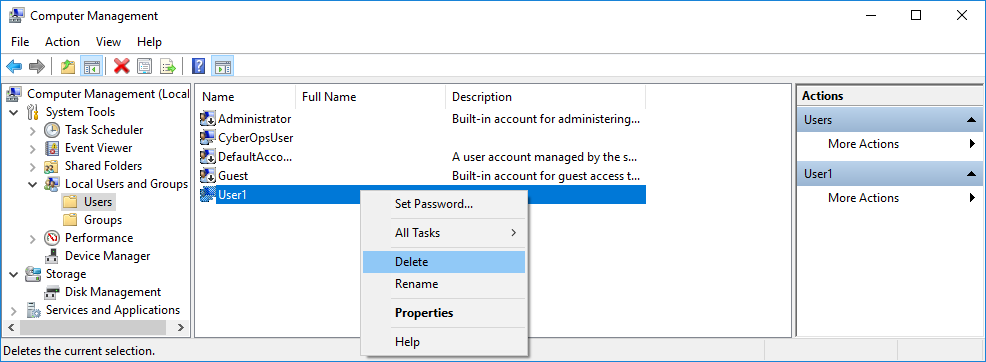
3.3.10 Lab – Create User Accounts (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Introduction In this lab, you will create and modify user accounts in Windows. Part 1: Creating a New Local User Account Part 2: Reviewing User Account Properties Part 3: Modifying Local User Accounts Required Resources • A Windows PC Instructor Note: Provide students with a user account name and password to be created in this lab. Instructions Part 1: Creating a New Local User Account Step 1: Open the User Account Tool. a. Log on…
Author: CCNA Security
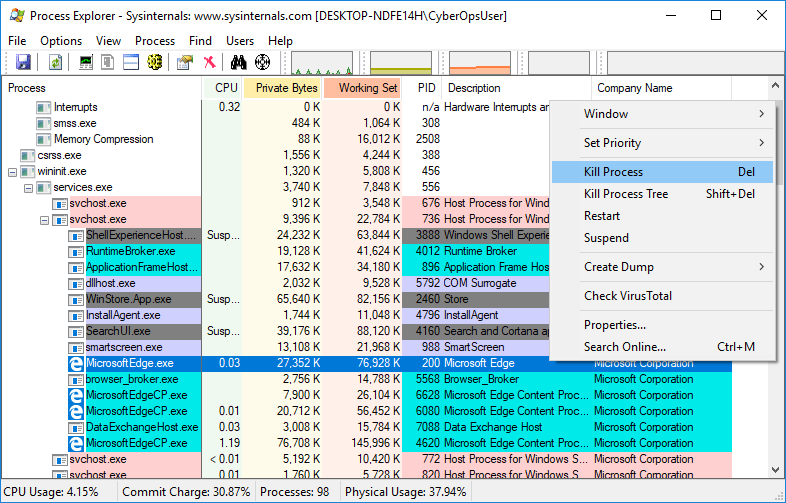
3.2.11 Lab – Exploring Processes, Threads, Handles, and Windows Registry (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives In this lab, you will explore the processes, threads, and handles using Process Explorer in the SysInternals Suite. You will also use the Windows Registry to change a setting. Part 1: Exploring Processes Part 2: Exploring Threads and Handles Part 3: Exploring Windows Registry Required Resources 1 Windows PC with internet access Instructions Part 1: Exploring Processes In this part, you will explore processes. Processes are programs or applications in…
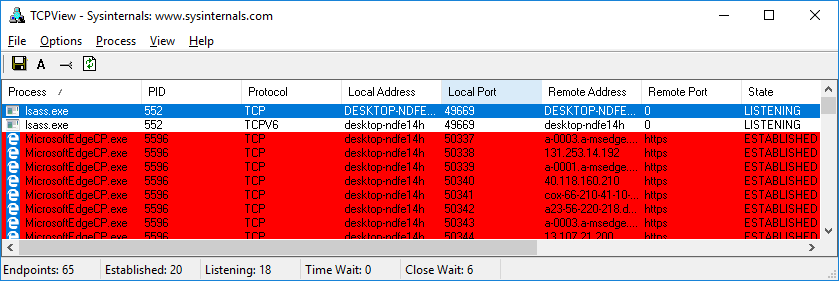
3.0.3 Class Activity – Identify Running Processes (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives In this lab, you will use TCP/UDP Endpoint Viewer, a tool in Sysinternals Suite, to identify any running processes on your computer. Part 1: Download Windows Sysinternals Suite. Part 2: Start TCP/UDP Endpoint Viewer. Part 3: Explore the running processes. Part 4: Explore a user-started process. Background / Scenario In this lab, you will explore processes. Processes are programs or applications in execution. You will explore the processes using Process Explorer in the…
2.2.5 Lab – Becoming a Defender (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Research and analyze what it takes to become a network defender. Part 1: Conduct search of Certifications. Part 2: Investigate positions available within cybersecurity Background / Scenario In our technology-centric world, as the world gets more connected, it also gets less safe. Cybersecurity is one of the fastest growing and most in-demand professions. Individuals in this field perform a wide variety of jobs including, but not limited to, consultation, investigation, and program management services…
1.3.4 Lab – Visualizing the Black Hats (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Research and analyze cyber security incidents. Background / Scenario The FBI has estimated that cybercrime cost individuals and companies over 3.5 billion dollars in 2019. Governments, businesses, and individual users are increasingly the targets of cyberattacks and cybersecurity incidents are becoming more common. In this lab, you will create three hypothetical cyber attackers, each with an organization, an attack, a motive. In addition, suggest a method by which an organization could prevent or…
1.1.6 Lab – Cybersecurity Case Studies (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Research and analyze cyber security incidents. Part 1: Conduct search of high profile cyberattacks. Part 2: Write an analysis of a cyberattack. Background / Scenario Governments, businesses, and individual users are increasingly the targets of cyberattacks and experts predict that these attacks are likely to increase in the future. Cybersecurity education is a top international priority as high-profile cyber-security related incidents raise the fear that attacks could threaten the global economy. The Center for…
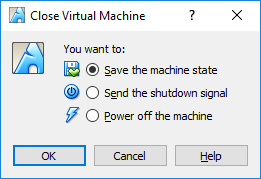
1.1.5 Lab – Installing the Virtual Machines (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Prepare a Personal Computer for Virtualization Part 2: Import a Virtual Machine into VirtualBox Inventory Background / Scenario Computing power and resources have increased tremendously over the last 10 years. A benefit of having multicore processors and large amounts of RAM is the ability to use virtualization. With virtualization, one or more virtual computers operate inside one physical computer. Virtual computers that run within physical computers are called virtual machines. Virtual…
1.0.6 Class Activity – Top Hacker Shows Us How It is Done (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Understand vulnerabilities of wireless and other common technologies Part 1: View the TEDx Video “Top Hacker Shows Us How It’s Done; Pablos Holman at TEDxMidwests” Part 2: Answer the following questions Background / Scenario Nearly every “secure” system that is used today can be vulnerable to some type of cyberattack. Required Resources PC or mobile device with internet access Instructions Part 1: View the TEDx Video “Top Hacker…
1.2.3 Lab – Learning the Details of Attacks (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Research and analyze IoT application vulnerabilities. Part 1: Conduct a Search of IoT Application Vulnerabilities Background / Scenario The Internet of Things (IoT) consists of digitally connected devices that are connecting every aspect of our lives, including our homes, offices, cars, and even our bodies to the internet. With the accelerating adoption of IPv6 and the near universal deployment of Wi-Fi networks, the IoT is growing at an exponential pace. According to…