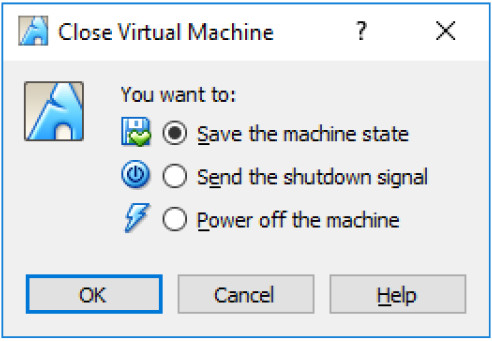
Topology Objectives In this lab, you will set up a virtual network environment by connecting multiple virtual machines in Virtualbox. Background / Scenario A virtual network security sandbox or multi-VM lab environment is useful for security analysis and testing. This multi-VM environment is a requirement for more advanced labs in this course. Required Resources The CyberOps Workstation VM (cyberops_workstation.ova). Internet Connection “The following .ova files for creating additional VMs: kali_linux.ova, metasploitable.ova, and security_onion.ova. Click each link to download the files. Host computer with at least 8 GB of RAM and 45 GB of free disk space. Note: If your computer…
Author: CCNA Security
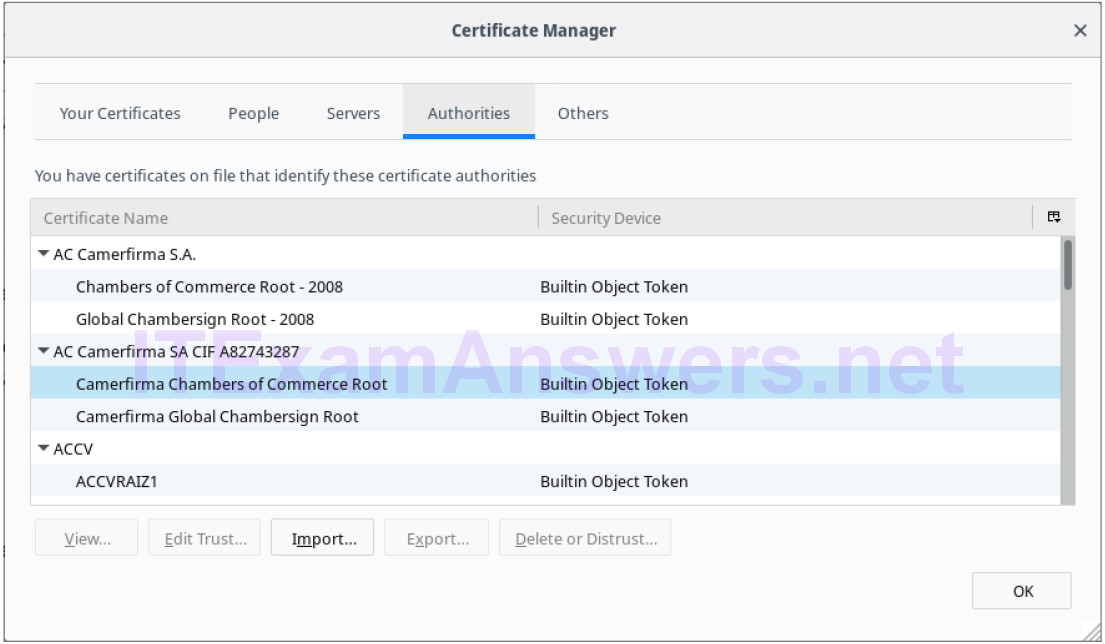
Objectives Part 1: Certificates Trusted by Your Browser Part 2: Checking for Man-In-Middle Background / Scenario As the web evolved, so did the need for security. HTTPS (where the ‘S’ stands for security) along with the concept of a Certificate Authority was introduced by Netscape back in 1994 and is still used today. In this lab, you will: List all the certificates trusted by your browser (completed on your computer) Use hashes to detect if your Internet connection is being intercepted (completed in the CyberOps VM) Required Resources CyberOps Workstation VM Internet access Part 1: Certificates Trusted by Your Browser…
Objectives Part 1: Creating Hashes with OpenSSL Part 2: Verifying Hashes Background / Scenario Hash functions are mathematical algorithms designed to take data as input and generate a fixed-size, unique string of characters, also known as the hash. Designed to be fast, hash functions are very hard to reverse; it is very hard to recover the data that created any given hash, based on the hash alone. Another important property of hash functions is that even the smallest change done to the input data yields a completely different hash. While OpenSSL can be used to generate and compare hashes, other…
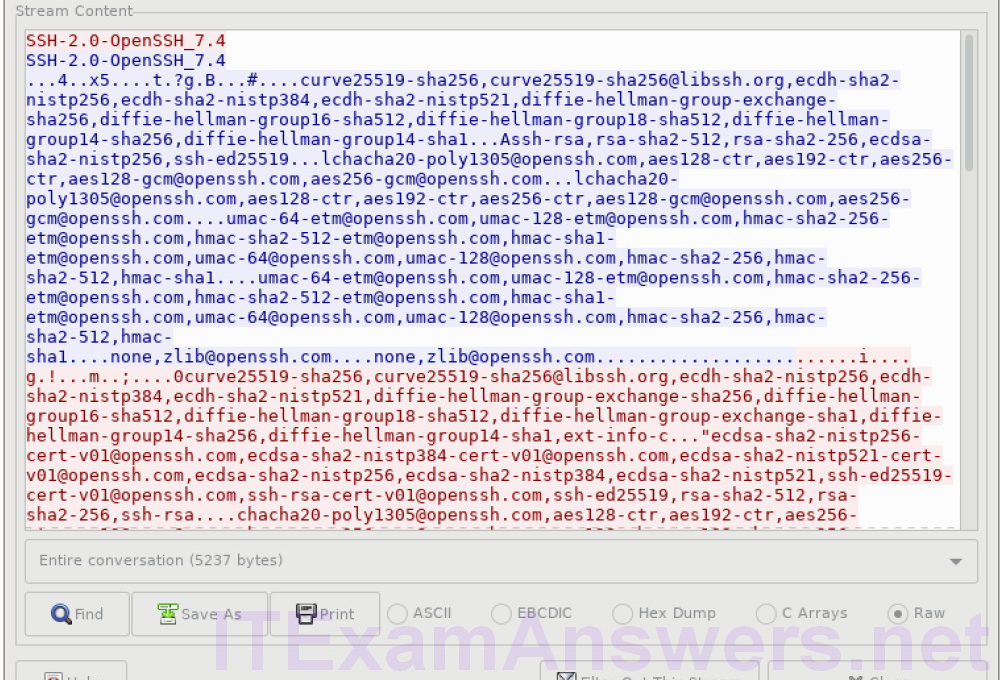
Objectives Part 1: Examine a Telnet Session with Wireshark Part 2: Examine an SSH Session with Wireshark Background / Scenario In this lab, you will configure a router to accept SSH connectivity and use Wireshark to capture and view Telnet and SSH sessions. This will demonstrate the importance of encryption with SSH. Required Resources CyberOps Workstation VM Part 1: Examining a Telnet Session with Wireshark You will use Wireshark to capture and view the transmitted data of a Telnet session. Step 1: Capture data. a. Start the CyberOps Workstation VM and log in with username analyst and password cyberops. b.…
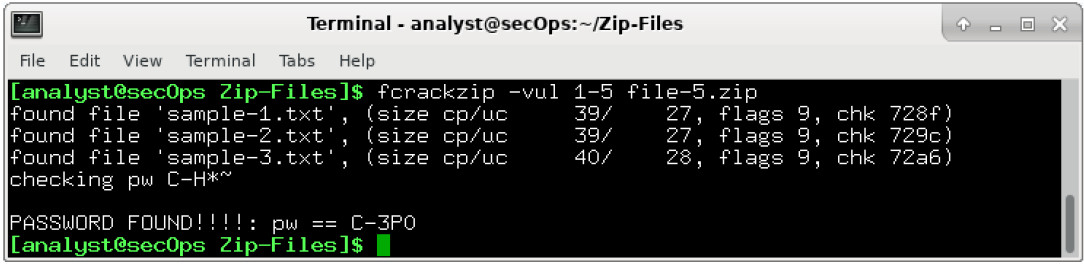
Objectives Part 1: Create and Encrypt Files Part 2: Recover Encrypted Zip File Passwords Background / Scenario What if you work for a large corporation that had a corporate policy regarding removable media? Specifically, it states that only encrypted zipped documents can be copied to portable USB flash drives. In this scenario, the Chief Financial Officer (CFO) is out-of-town on business and has contacted you in a panic with an emergency request for help. While out-of-town on business, he attempted to unzip important documents from an encrypted zip file on a USB drive. However, the password provided to open the…
Objectives Part 1: Encrypting Messages with OpenSSL Part 2: Decrypting Messages with OpenSSL Background / Scenario OpenSSL is an open source project that provides a robust, commercial-grade, and full-featured toolkit for the Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols. It is also a general-purpose cryptography library. In this lab, you will use OpenSSL to encrypt and decrypt text messages. Note: While OpenSSL is the de facto cryptography library today, the use presented in this lab is NOT recommended for robust protection. Below are two security problems with this lab: The method described in this lab uses a…
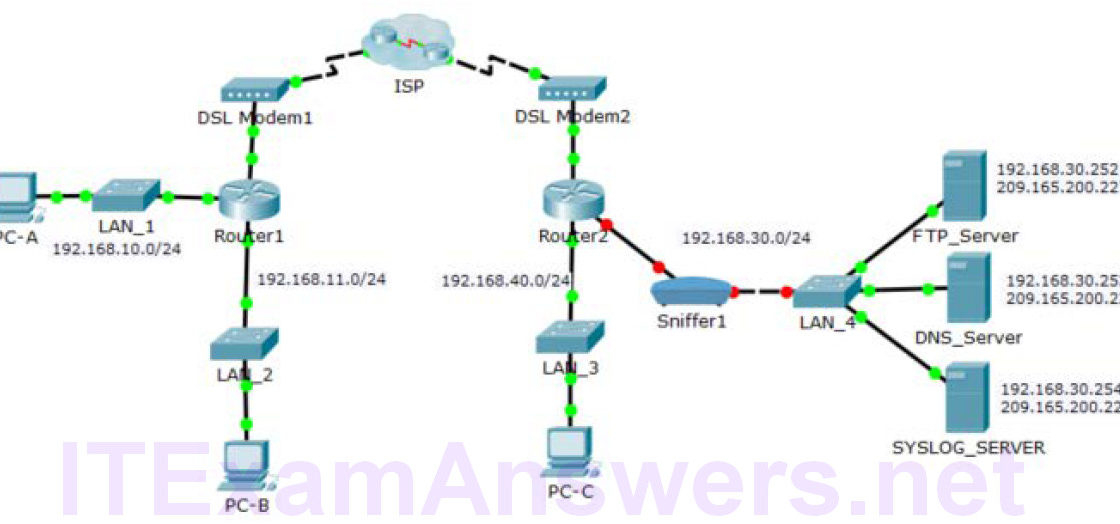
Topology Addressing Table Device Private IP Address Public IP Address FTP_Server 192.168.30.253 209.165.200.227 SYSLOG_SERVER 192.168.11.254 209.165.200.229 Router2 N/A 209.165.200.226 Objectives Part 1: Create FTP traffic. Part 2: Investigate the FTP Traffic Part 3: View Syslog Messages Background In this activity, you will use Packet Tracer to sniff and log network traffic. You will view a security vulnerability in one network application, and view logged ICMP traffic with syslog. Part 1: Create FTP traffic. Step 1: Activate the sniffing device. a. Click on sniffer device Sniffer1. b. Go to the Physical tab and turn on the power to the sniffer. c.…
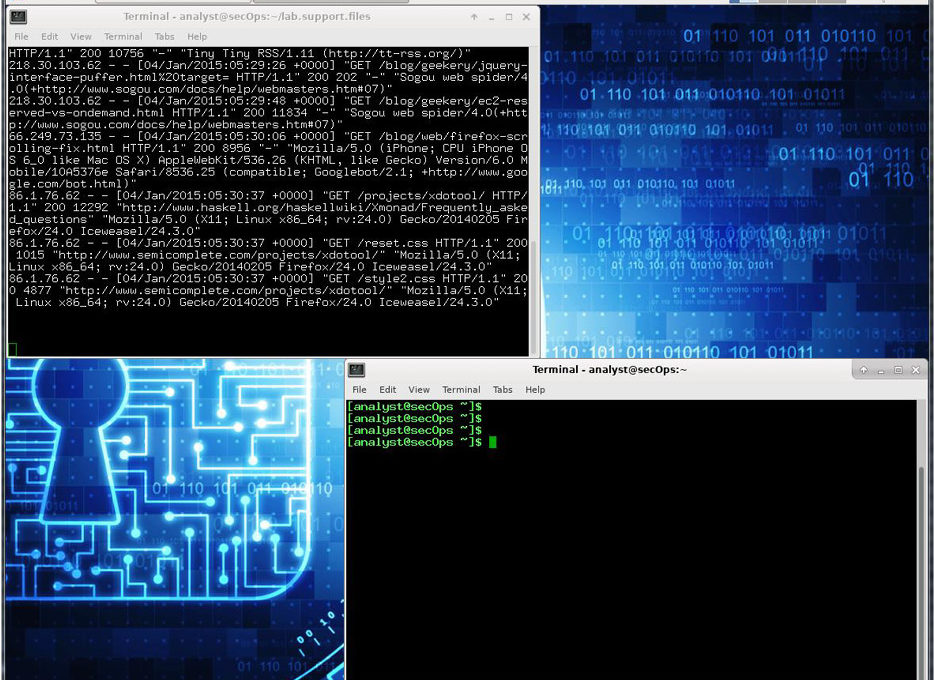
Objectives Part 1: Reading Log Files with Cat, More, and Less Part 2: Log Files and Syslog Part 3: Log Files and Journalctl Background / Scenario Log files are an important tool for troubleshooting and monitoring. Different application generates different log files, each one containing its own set of fields and information. While the field structure may change between log files, the tools used to read them are mostly the same. In this lab, you will learn about common tools used to read log file and practice using them. Required Resources CyberOps Workstation Virtual Machine Internet access Part 1: Reading…
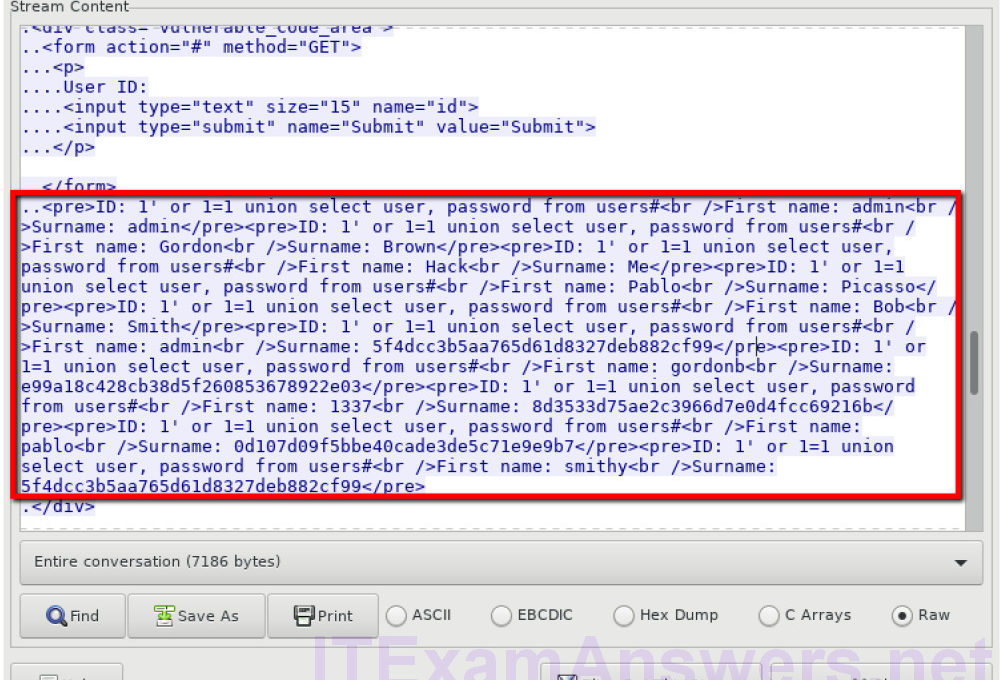
Objectives In this lab, you will view a PCAP file from a previous attack against a SQL database. Background / Scenario SQL injection attacks allow malicious hackers to type SQL statements in a web site and receive a response from the database. This allows attackers to tamper with current data in the database, spoof identities, and miscellaneous mischief. A PCAP file has been created for you to view a previous attack against a SQL database. In this lab, you will view the SQL database attacks and answer the questions. Required Resources CyberOps Workstation Virtual Machine Internet access Part 1: Open…