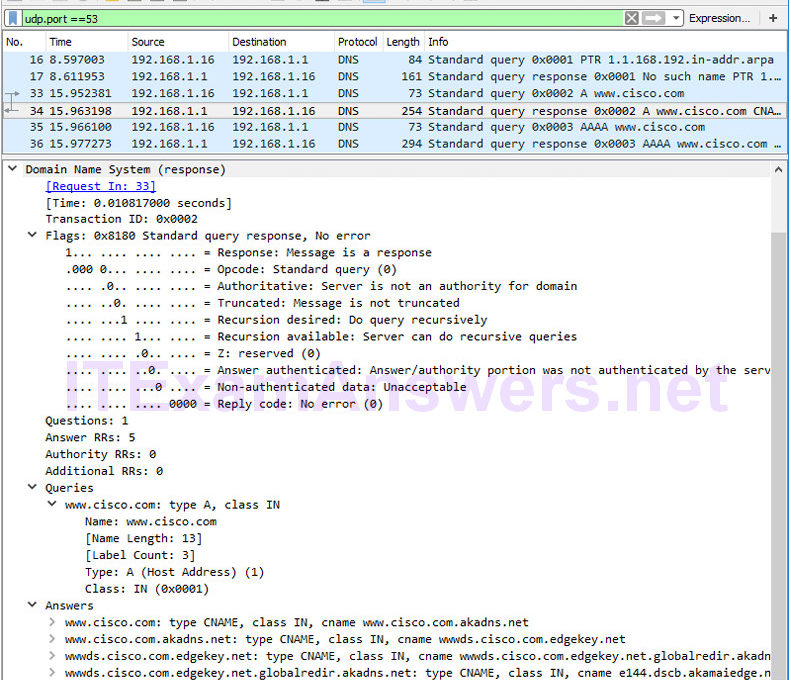
Objectives Part 1: Capture DNS Traffic Part 2: Explore DNS Query Traffic Part 3: Explore DNS Response Traffic Background / Scenario Wireshark is an open source packet capture and analysis tool. Wireshark gives a detailed breakdown of the network protocol stack. Wireshark allows you to filter traffic for network troubleshooting, investigate security issues, and analyze network protocols. Because Wireshark allows you to view the packet details, it can be used as a reconnaissance tool for an attacker. In this lab, you will install Wireshark on a Windows system and use Wireshark to filter for DNS packets and view the details…
Author: CCNA Security
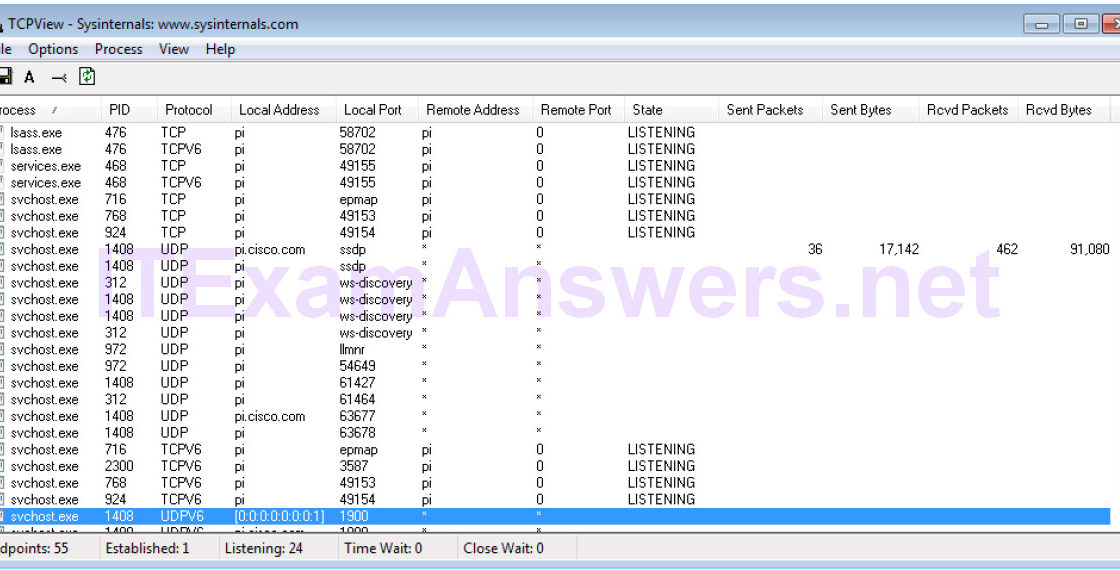
Objectives Identify the processes running on a computer, the protocol they are using, and their local and remote port addresses. Background / Scenario For a hacker to establish a connection to a remote computer, a port must be listening on that device. This may be due to infection by malware, or a vulnerability in a legitimate piece of software. A utility, such as TCPView, can be used to detect open ports, monitor them in real-time, and close active ports and processes using them. Required Resources PC with Internet access TCPView software Step 1: Download and install the TCPView software. a.…
Objectives Research and identify social engineering attacks Background / Scenario Social engineering is an attack with the goal of getting a victim to enter personal or sensitive information, this type of attack can be performed by an attacker utilizing a keylogger, phishing email, or an in-person method. This lab requires the research of social engineering and the identification of ways to recognize and prevent it. Required Resources PC or mobile device with Internet access Step 1: Read the following article. Navigate to the following website and read it thoroughly to answer the following questions in step 2. https://www.sans.org/reading-room/whitepapers/critical/methods-understanding-reducing-social-engineering-attacks-36972 Step 2:…
Objectives Research and analyze malware Background / Scenario Malware, or malicious software, refers to a variety of malicious software programs that can be used to cause harm to computer systems, steal data, and bypass security measures. Malware can also attack critical infrastructure, disable emergency services, cause assembly lines to make defective products, disable electric generators, and disrupt transportation services. Security experts estimate that more than one million new malware threats are released each day. A McAfee Labs report indicates almost 500 million known malware threats at the end of 2015. Note: You can use the web browser in virtual machine…
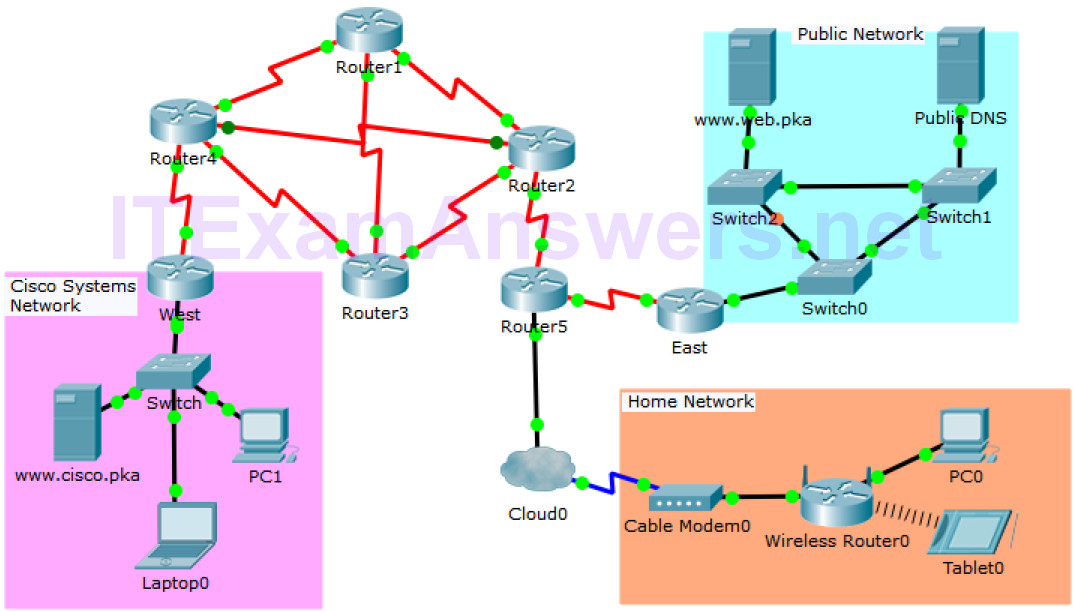
Topology Objectives In this activity, you will observe packet flow in a LAN and WAN topology. You will also observe how the packet flow path may change when there is a change in the network topology. Part 1: Verify Connectivity Part 2: Remote LAN Network Topology Part 3: WAN Network Topology Background / Scenario Packet Tracer allows the design and creation of a simulated networking topology. In this activity, you are presented with a simplified topology to observe packet flow. You will explore how packets travel through the network using the simulation mode in Packet Tracer. You will also observe…
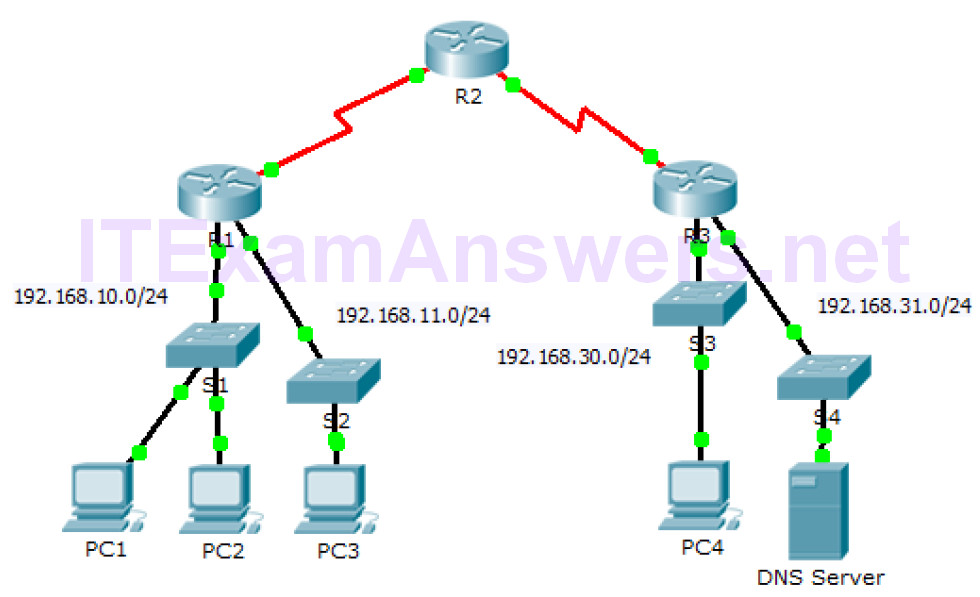
Topology Objectives Part 1: Verify Local Connectivity and Test Access Control List Part 2: Remove Access Control List and Repeat Test Background In this activity, you will observe how an access control list (ACL) can be used to prevent a ping from reaching hosts on remote networks. After removing the ACL from the configuration, the pings will be successful. Part 1: Verify Local Connectivity and Test Access Control List Step 1: Ping devices on the local network to verify connectivity. a. From the command prompt of PC1, ping PC2. b. From the command prompt of PC1, ping PC3. Why were…
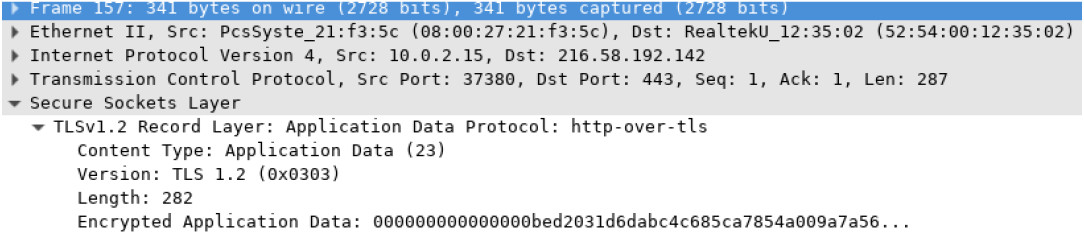
Objectives Part 1: Capture and view HTTP traffic Part 2: Capture and view HTTPS traffic Background / Scenario HyperText Transfer Protocol (HTTP) is an application layer protocol that presents data via a web browser. With HTTP, there is no safeguard for the exchanged data between two communicating devices. With HTTPS, encryption is used via a mathematical algorithm. This algorithm hides the true meaning of the data that is being exchanged. This is done through the use of certificates that can be viewed later in this lab. Regardless of HTTP or HTTPS, it is only recommended to exchange data with websites…
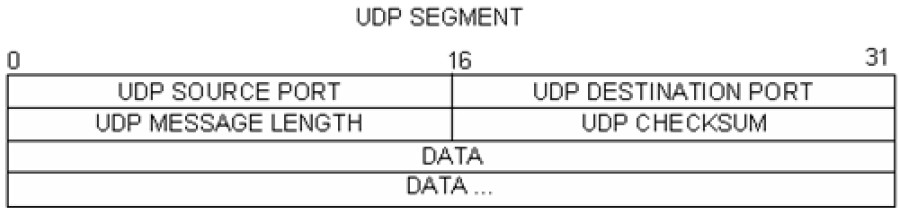
Topology – Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of the CyberOps Workstation VM with Internet access. Mininet Topology – Part 2 (TFTP) Part 2 will highlight a UDP capture of a TFTP session using the hosts in Mininet. Objectives Part 1: Identify TCP Header Fields and Operation Using a Wireshark FTP Session Capture Part 2: Identify UDP Header Fields and Operation Using a Wireshark TFTP Session Capture Background / Scenario Two protocols in the TCP/IP transport layer are TCP (defined in RFC 761) and UDP (defined in RFC 768).…
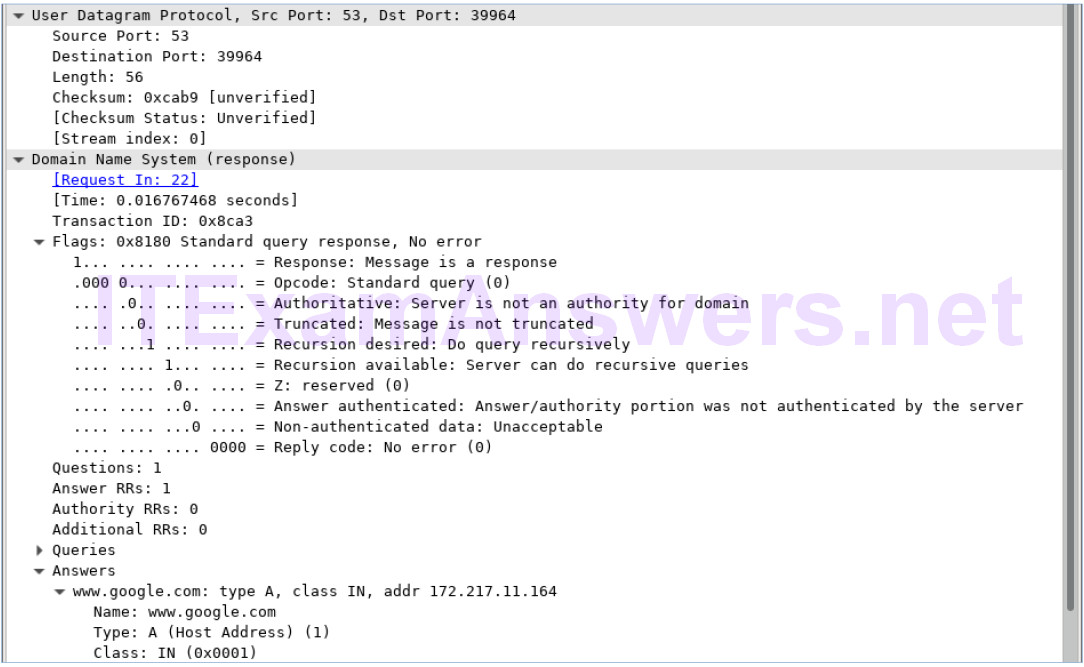
Topology Objectives Part 1: Record a PC’s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario When you use the Internet, you use the Domain Name System (DNS). DNS is a distributed network of servers that translates user-friendly domain names like www.google.com to an IP address. When you type a website URL into your browser, your PC performs a DNS query to the DNS server’s IP address. Your PC’s DNS query and the DNS server’s response make use of the User Datagram Protocol (UDP) as…