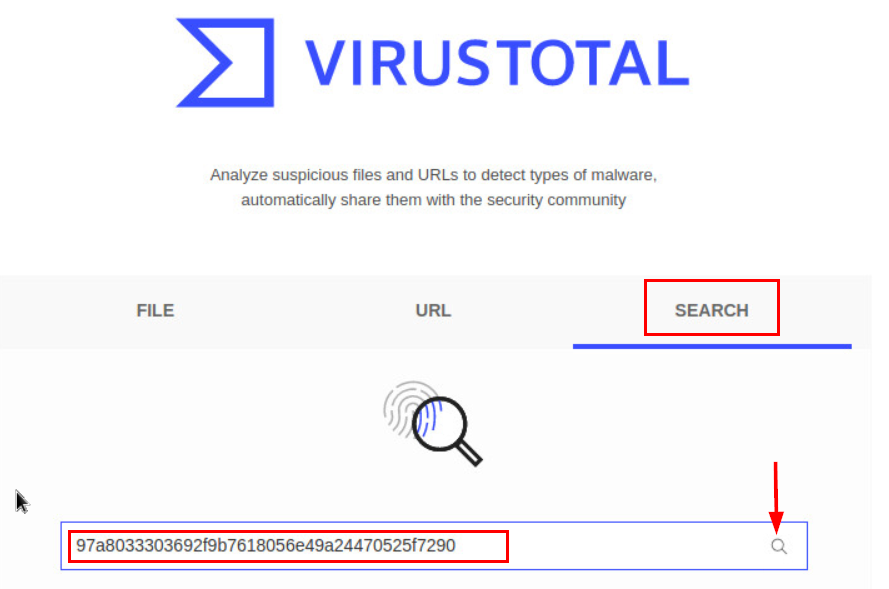
27.2.15 Lab – Investigating a Malware Exploit (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only.…
Browsing: CyberOps Associate Labs
1.0.6 Class Activity – Top Hacker Shows Us How It is Done (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears…
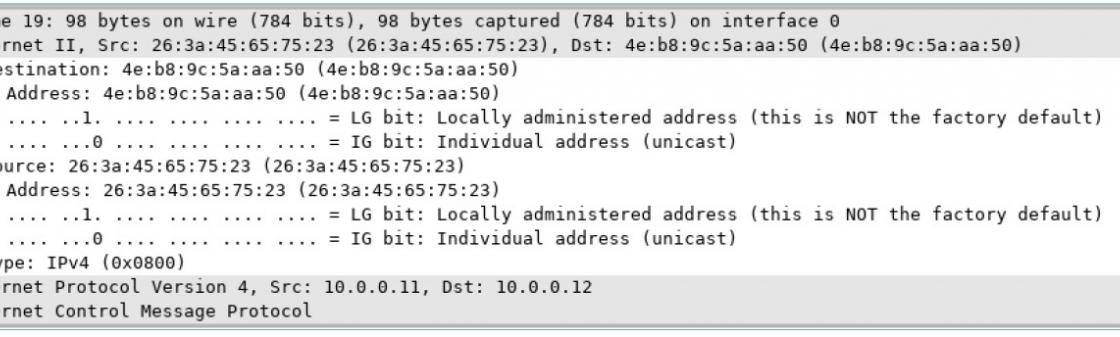
Mininet Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background /…
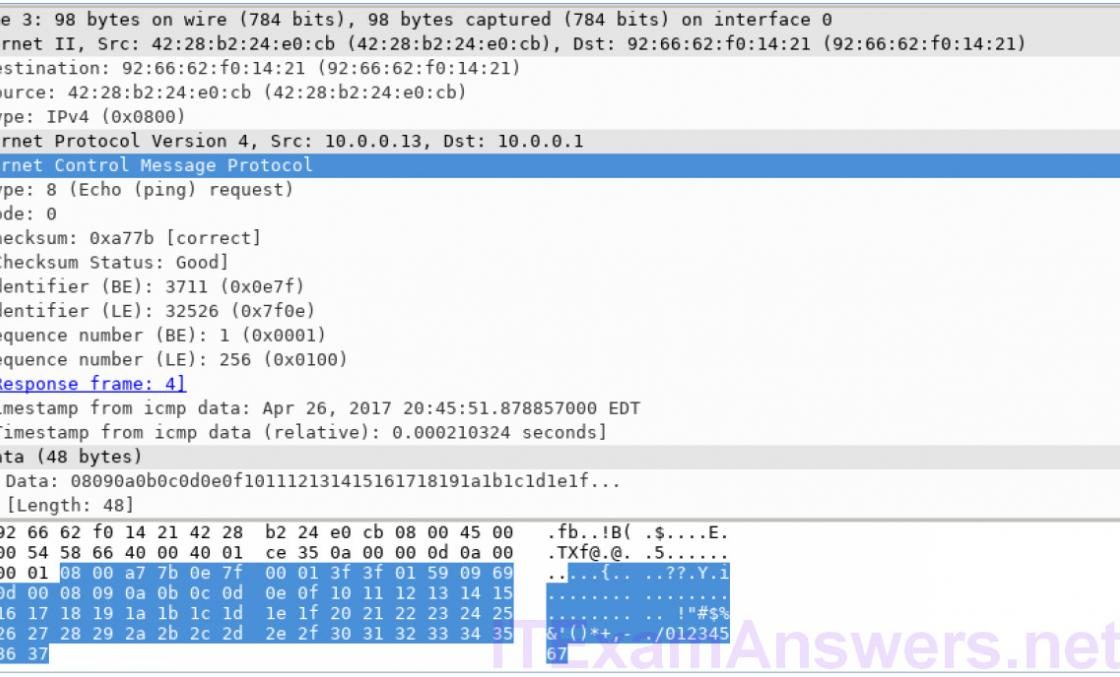
Mininet Topology Objectives Part 1: Install and Verify the Mininet Topology Part 2: Capture and Analyze ICMP Data in Wireshark Background / Scenario The CyberOps VM…
Objectives Part 1: Verifying Network Connectivity Using Ping Part 2: Tracing a Route to a Remote Server Using Traceroute Part 3: Trace a Route to a…
Objectives In this lab, you will use familiarize yourself with Linux filesystems. Required Resources CyberOps Workstation VM Part 1: Exploring Filesystems in Linux The Linux filesystem…
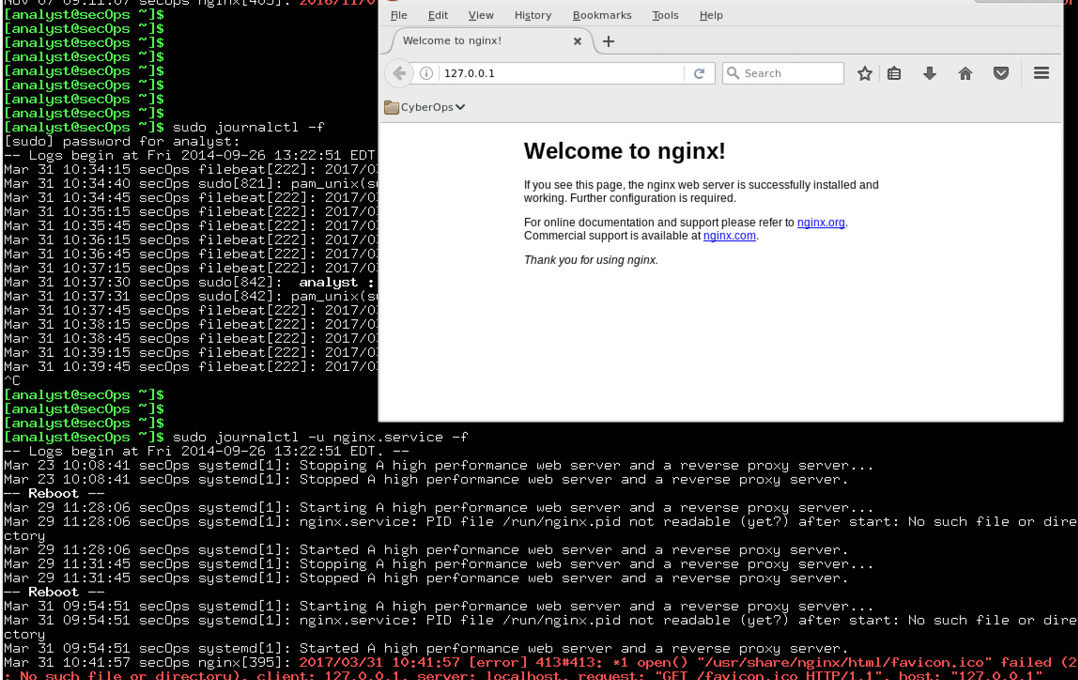
Introduction In this lab, you will get familiar with locating and manipulating Linux log files. Required Resources CyberOps Workstation Virtual Machine Part 1: Log File Overview…
Introduction In this lab, you will use the Linux command line to identify servers running on a given computer. Recommended Equipment CyberOps Workstation Virtual Machine Part…
Introduction In this lab, you will use the Linux command line to manage files and folders, and perform some basic administrative tasks. Recommended Equipment CyberOps Workstation…