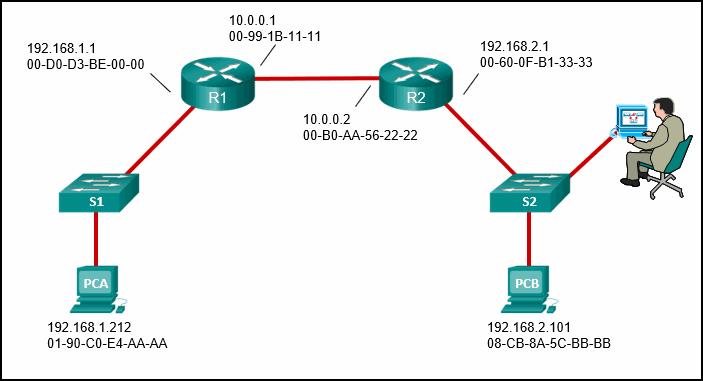
- In what type of attack is a cybercriminal attempting to prevent legitimate users from accessing network services?
- DoS *
- MITM
- Session hijacking
- Address spoofing
- Which network monitoring technology collects IP operational data on packets flowing through Cisco routers and multilayer switches?
- SNMP
- SIEM
- NetFlow *
- Wireshark
- What are two monitoring tools that capture network traffic and forward it to network monitoring devices? (Choose two.)
- SPAN
- network tap
- SNMP
- SIEM
- Wireshark
- Which technology is an open source SIEM system?
- Wireshark
- StealWatch
- Splunk
- ELK
- What network attack seeks to create a DoS for clients by preventing them from being able to obtain a DHCP lease?
- IP address spoofing
- DHCP starvation
- CAM table attack
- DHCP spoofing
- Which protocol would be the target of a cushioning attack?
- DHCP
- HTTP
- ARP
- DNS
- What is the result of a passive ARP poisoning attack?
- Confidential information is stolen.
- Network clients experience a denial of service
- Data is modified in transit or malicious data is inserted in transit.
- Multiple subdomains are created.
- Which term is used for bulk advertising emails flooded to as many end users as possible?
- spam
- adware
- brute force
- phishing
- Which capability is provided by the aggregation function in SIEM?
- reducing the volume of event data by consolidating duplicate event records
- searching logs and event records of multiple sources for more complete forensic analysis
- presenting correlated and aggregated event data in real-time monitoring
- increasing speed of detection and reaction to security threats by examining logs from many systems and applications
- Which protocol is attacked when a cybercriminal provides an invalid gateway in order to create a man-in-the-middle attack?
- HTTP or HTTPS
- ICMP
- DNS
- DHCP
- Which network monitoring capability is provided by using SPAN?
- Network analysts are able to access network device log files and to monitor network behavior.
- Statistics on packets flowing through Cisco routers and multilayer switches can be captured.
- Traffic exiting and entering a switch is copied to a network monitoring device.
- Real-time reporting and long-term analysis of security events are enabled.
- Which network monitoring tool is in the category of network protocol analyzers?
- SNMP
- SPAN
- Wireshark *
- SIEM
- Which SIEM function is associated with examining the logs and events of multiple systems to reduce the amount of time of detecting and reacting to security events?
- Retention
- Aggregation
- Correlation *
- Forensic analysis
- Which network technology uses a passive splitting device that forwards all traffic, including Layer 1 errors, to an analysis device?
- IDS
- SNMP
- NetFlow
- Network TAP *
- What technique is a security attack that depletes the pool of IP addresses available for legitimate hosts?
- DHCP spoofing
- DHCP snooping
- DHCP starvation *
- Reconnaissance attack
- Which type of DNS attack involves the cybercriminal compromising a parent domain and creating multiple subdomains to be used during the attacks?
- shadowing
- amplification and reflection
- tunneling
- cache poisoning
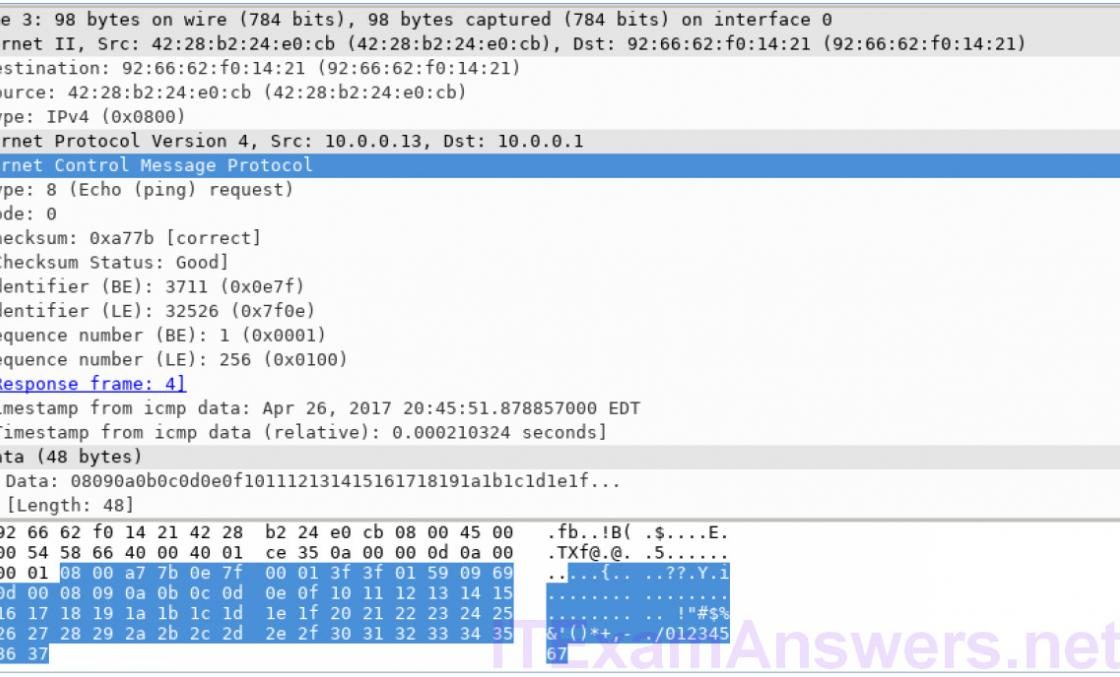
- Refer to the exhibit. What protocol would be used by the syslog server service to create this type of output for security purposes?
- NTP
- AAA
- ICMP
- SNMP
- Which network monitoring tool can provide a complete audit trail of basic information of all IP flows on a Cisco router and forward the data to a device?
- SPAN
- Wireshark
- NetFlow
- SIEM
- What are two methods used by cybercriminals to mask DNS attacks? (Choose two.)
- domain generation algorithms
- shadowing
- fast flux
- reflection
- tunneling
- In which type of attack is falsified information used to redirect users to malicious Internet sites?
- ARP cache poisoning
- DNS amplification and reflection
- DNS cache poisoning
- domain generation
- Refer to the exhibit. A junior network administrator is inspecting the traffic flow of a particular server in order to make security recommendations to the departmental supervisor. Which recommendation should be made?
- A more secure protocol should be used.
- The total length (TL) field indicates an unsecure Layer 4 protocol is being used.
- The person accessing the server should never access it from a device using a private IP address.
- The person accessing the server should use the private IP address of the server.
- Which network monitoring tool saves captured packets in a PCAP file?
- Wireshark
- SIEM
- SNMP
- NetFlow
- Which cyber attack involves a coordinated attack from a botnet of zombie computers?
- ICMP redirect
- MITM
- DDoS
- address spoofing
- How is optional network layer information carried by IPv6 packets?
- inside an options field that is part of the IPv6 packet header
- inside the Flow Label field
- inside the payload carried by the IPv6 packet
- inside an extension header attached to the main IPv6 packet header
- Which protocol is exploited by cybercriminals who create malicious iFrames?
- HTTP
- ARP
- DNS
- DHCP
- Which SIEM function is associated with speeding up detection of security threats by examining logs and events from different systems?
- forensic analysis
- retention
- correlation
- aggregation
- In which TCP attack is the cybercriminal attempting to overwhelm a target host with half-open TCP connections?
- reset attack
- session hijacking attack
- port scan attack
- SYN flood attack
- What type of attack targets an SQL database using the input field of a user?
- Cross-site scripting
- SQL injection
- buffer overflow
- XML injection
- What network monitoring technology enables a switch to copy and forward traffic sent and received on multiple interfaces out another interface toward a network analysis device?
- port mirroring
- NetFlow
- SNMP
- network tap
Subscribe
Login
0 Comments
Oldest