CyberOps Associate (Version 1.0) – Modules 24 – 25: Protocols and Log Files Group Exam
1. What is a feature of the tcpdump tool?
- It provides real-time reporting and long-term analysis of security events.
- It records metadata about packet flows.
- It uses agents to submit host logs to centralized management servers.
- It can display packet captures in real time or write them to a file.
2. Which Windows tool can be used to review host logs?
- Services
- Event Viewer
- Task Manager
- Device Manager
3. Which type of security data can be used to describe or predict network behavior?
- alert
- transaction
- session
- statistical
4. Which function is provided by the Sguil application?
- It reports conversations between hosts on the network.
- It makes Snort-generated alerts readable and searchable.
- It detects potential network intrusions.
- It prevents malware from attacking a host.
5. Which ICMP message type should be stopped inbound?
- source quench
- echo-reply
- echo
- unreachable
6. How can IMAP be a security threat to a company?
- Someone inadvertently clicks on a hidden iFrame.
- Encrypted data is decrypted.
- An email can be used to bring malware to a host.
- It can be used to encode stolen data and send to a threat actor.
7. Which two technologies are primarily used on peer-to-peer networks? (Choose two.)
- Bitcoin
- BitTorrent
- Wireshark
- Darknet
- Snort
8. Which protocol is exploited by cybercriminals who create malicious iFrames?
- HTTP
- ARP
- DHCP
- DNS
9. Which method is used by some malware to transfer files from infected hosts to a threat actor host?
- UDP infiltration
- ICMP tunneling
- HTTPS traffic encryption
- iFrame injection
10. Why does HTTPS technology add complexity to network security monitoring?
- HTTPS dynamically changes the port number on the web server.
- HTTPS uses tunneling technology for confidentiality.
- HTTPS hides the true source IP address using NAT/PAT.
- HTTPS conceals data traffic through end-to-end encryption.
11. Which approach is intended to prevent exploits that target syslog?
- Use a Linux-based server.
- Use syslog-ng.
- Create an ACL that permits only TCP traffic to the syslog server.
- Use a VPN between a syslog client and the syslog server.
12. Which type of attack is carried out by threat actors against a network to determine which IP addresses, protocols, and ports are allowed by ACLs?
- phishing
- denial of service
- reconnaissance
- social engineering
13. Which two application layer protocols manage the exchange of messages between a client with a web browser and a remote web server? (Choose two.)
- HTTP
- HTTPS
- DNS
- DHCP
- HTML
14. What is Tor?
- a rule created in order to match a signature of a known exploit
- a software platform and network of P2P hosts that function as Internet routers
- a way to share processors between network devices across the Internet
- a type of Instant Messaging (IM) software used on the darknet
15. Which Windows log contains information about installations of software, including Windows updates?
- system logs
- application logs
- setup logs
- security logs
16. Match the Windows host log to the messages contained in it. (Not all options are used.)
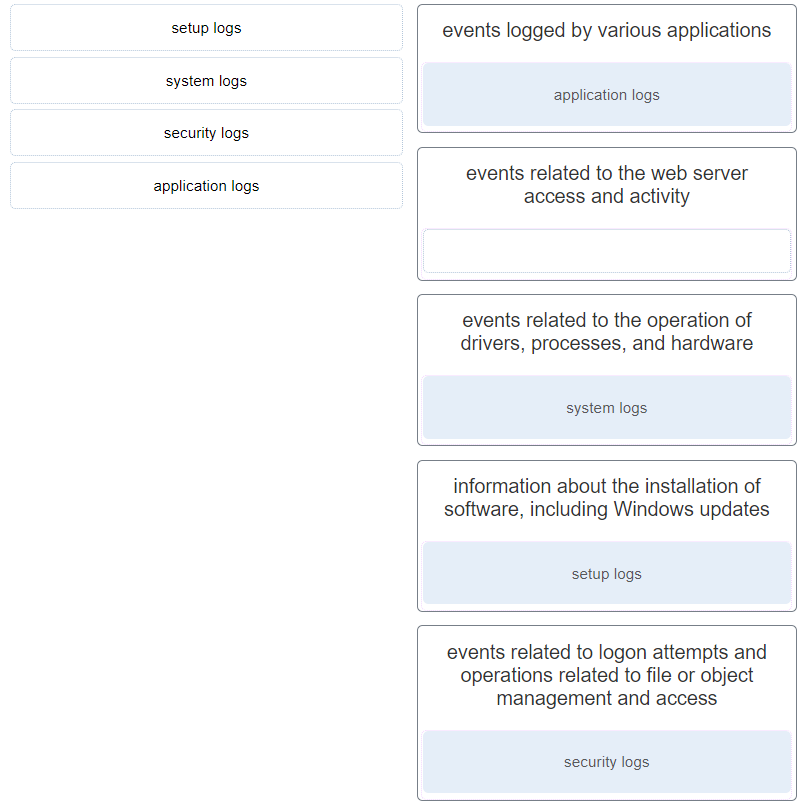
- events logged by various applications : application logs
- events related to the web server access and activity :
- events related to the operation of drivers, processes, and hardware : system logs
- information about the installation of software, including Windows updates : setup logs
- events related to logon attempts and operations related to file or object management and access : security logs
17. Which Cisco appliance can be used to filter network traffic contents to report and deny traffic based on the web server reputation?
- WSA
- AVC
- ASA
- ESA
18. Which technique would a threat actor use to disguise traces of an ongoing exploit?
- Create an invisible iFrame on a web page.
- Corrupt time information by attacking the NTP infrastructure.
- Encapsulate other protocols within DNS to evade security measures.
- Use SSL to encapsulate malware.
19. A system administrator runs a file scan utility on a Windows PC and notices a file lsass.exe in the Program Files directory. What should the administrator do?
- Delete the file because it is probably malware.
- Move it to Program Files (x86) because it is a 32bit application.
- Uninstall the lsass application because it is a legacy application and no longer required by Windows.
- Open the Task Manager, right-click on the lsass process and choose End Task .
20. Refer to the exhibit. A network administrator is viewing some output on the Netflow collector. What can be determined from the output of the traffic flow shown?
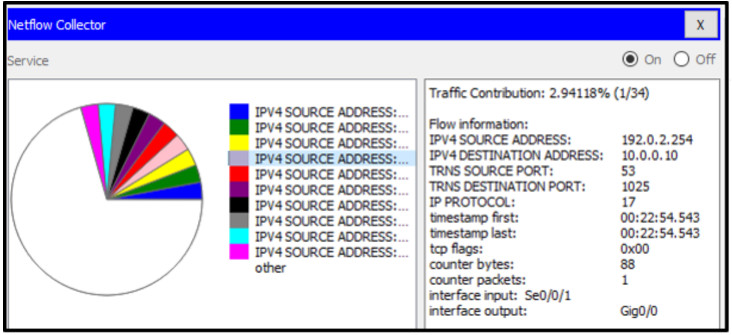
- This is a UDP DNS request to a DNS server.
- This is a UDP DNS response to a client machine.
- This is a TCP DNS request to a DNS server.
- This is a TCP DNS response to a client machine.
21 In a Cisco AVC system, in which module is NetFlow deployed?
- Management and Reporting
- Control
- Application Recognition
- Metrics Collection
22. What does it indicate if the timestamp in the HEADER section of a syslog message is preceded by a period or asterisk symbol?
- There is a problem associated with NTP.
- The timestamp represents the round trip duration value.
- The syslog message should be treated with high priority.
- The syslog message indicates the time an email is received.
23. Which protocol is a name resolution protocol often used by malware to communicate with command-and-control (CnC) servers?
- IMAP
- DNS
- HTTPS
- ICMP
24. Which technique is necessary to ensure a private transfer of data using a VPN?
- authorization
- scalability
- encryption
- virtualization
25. Which technology would be used to create the server logs generated by network devices and reviewed by an entry level network person who works the night shift at a data center?
- syslog
- NAT
- ACL
- VPN
26. Which statement describes a Cisco Web Security Appliance (WSA)?
- It protects a web server by preventing security threats from accessing the server.
- It provides high performance web services.
- It acts as an SSL-based VPN server for an enterprise.
- It functions as a web proxy.
27. Which statement describes statistical data in network security monitoring processes?
- It is created through an analysis of other forms of network data.
- It contains conversations between network hosts.
- It shows the results of network activities between network hosts.
- It lists each alert message along with statistical information.
28. Match the SIEM function with the description.
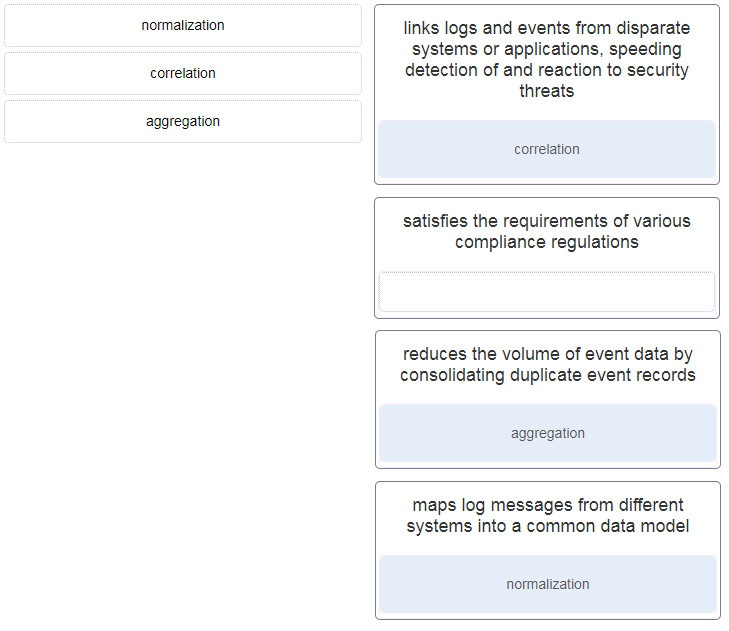
- links logs and events from disparate systems or applications, speeding detection of and reaction to security threats : correlation
- satisfies the requirements of various compliance regulations :
- reduces the volume of event data by consolidating duplicate event records : aggregation
- maps log messages from different systems into a common data model : normalization
29. Which two tools have a GUI interface and can be used to view and analyze full packet captures? (Choose two.)
- nfdump
- Wireshark
- Cisco Prime Network Analysis Module
- tcpdump
- Splunk
30. Which statement describes session data in security logs?
- It can be used to describe or predict network behavior.
- It shows the result of network sessions.
- It is a record of a conversation between network hosts.
- It reports detailed network activities between network hosts.
31. Which two options are network security monitoring approaches that use advanced analytic techniques to analyze network telemetry data? (Choose two.)
- NBAD
- Sguil
- NetFlow
- IPFIX
- Snorby
- NBA
32. How does a web proxy device provide data loss prevention (DLP) for an enterprise?
- by functioning as a firewall
- by inspecting incoming traffic for potential exploits
- by scanning and logging outgoing traffic
- by checking the reputation of external web servers
33. Which information can be provided by the Cisco NetFlow utility?
- security and user account restrictions
- IDS and IPS capabilities
- peak usage times and traffic routing
- source and destination UDP port mapping