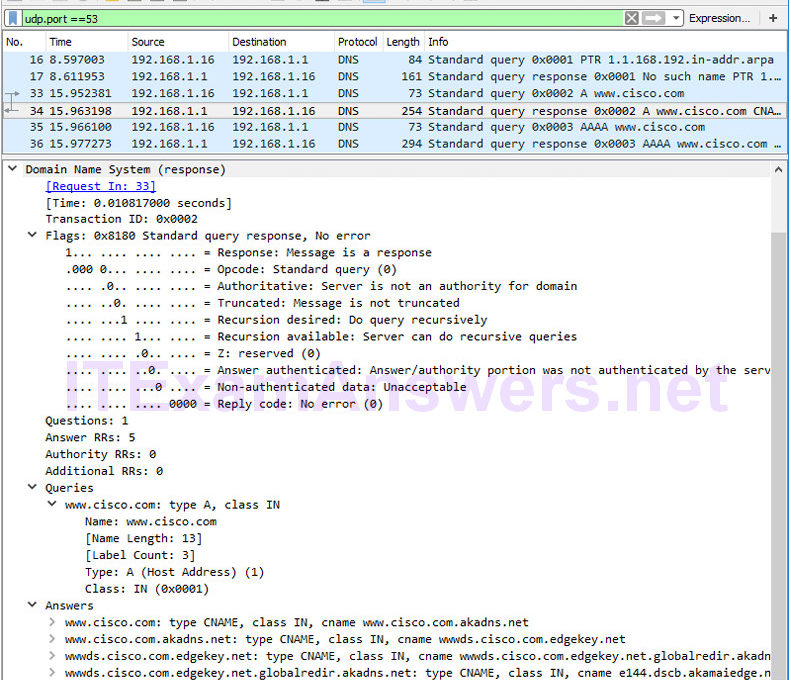
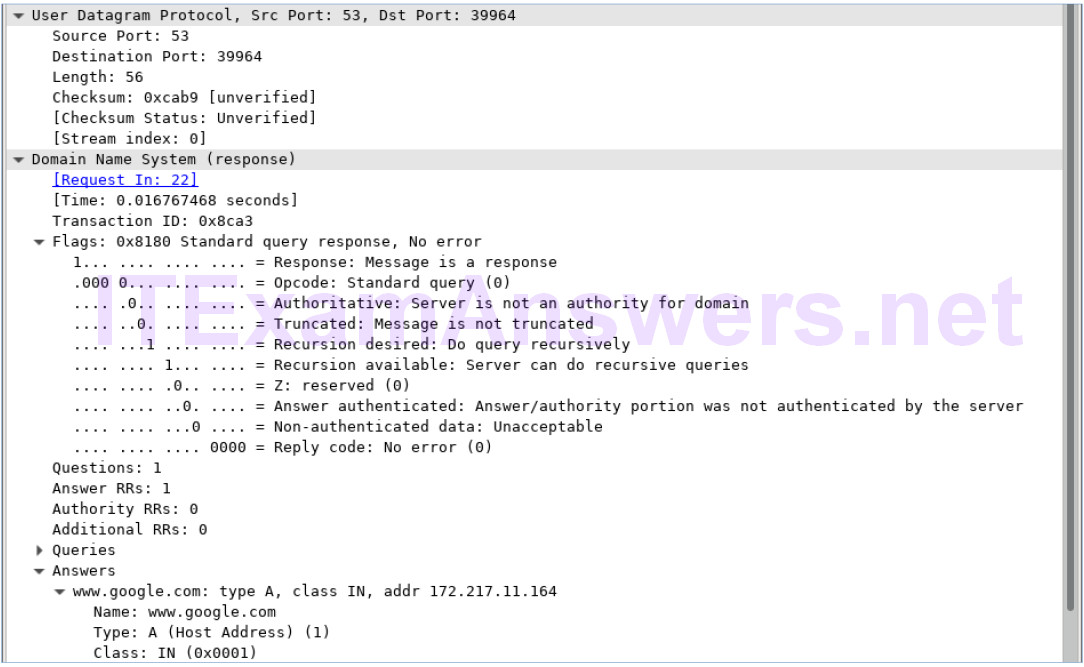
Objectives Part 1: Capture DNS Traffic Part 2: Explore DNS Query Traffic Part 3: Explore DNS Response Traffic Background / Scenario Wireshark is an open source…
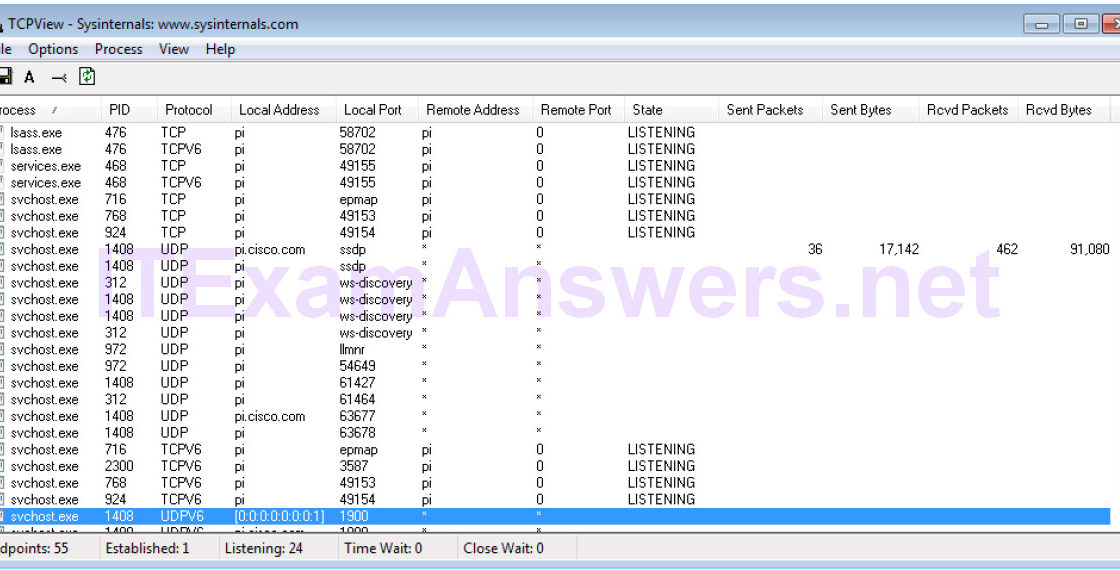
Objectives Identify the processes running on a computer, the protocol they are using, and their local and remote port addresses. Background / Scenario For a hacker…
Objectives Research and identify social engineering attacks Background / Scenario Social engineering is an attack with the goal of getting a victim to enter personal or…
Objectives Research and analyze malware Background / Scenario Malware, or malicious software, refers to a variety of malicious software programs that can be used to cause…
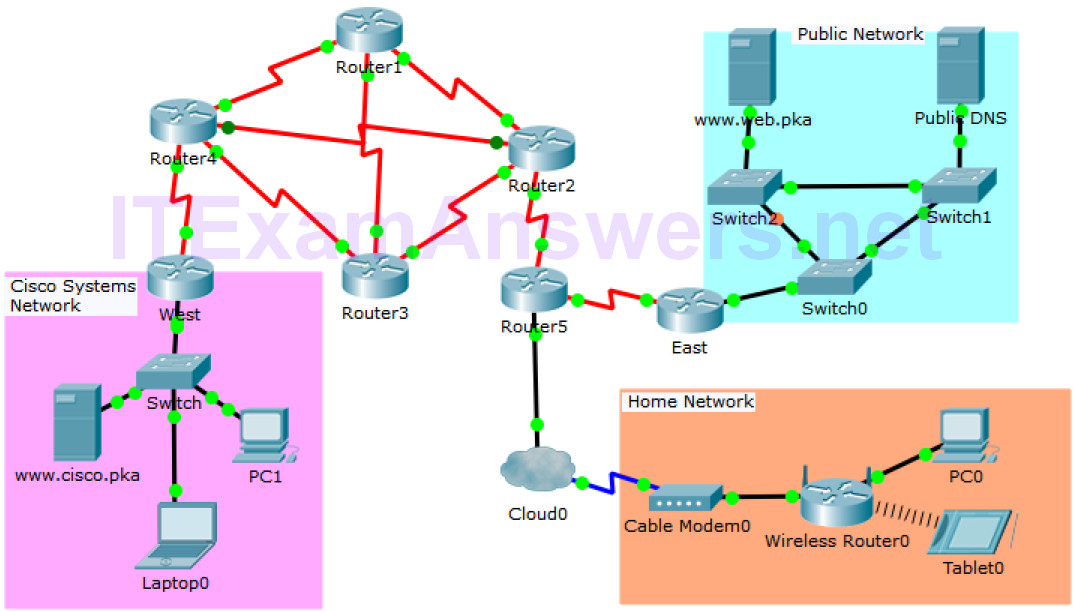
Topology Objectives In this activity, you will observe packet flow in a LAN and WAN topology. You will also observe how the packet flow path may…
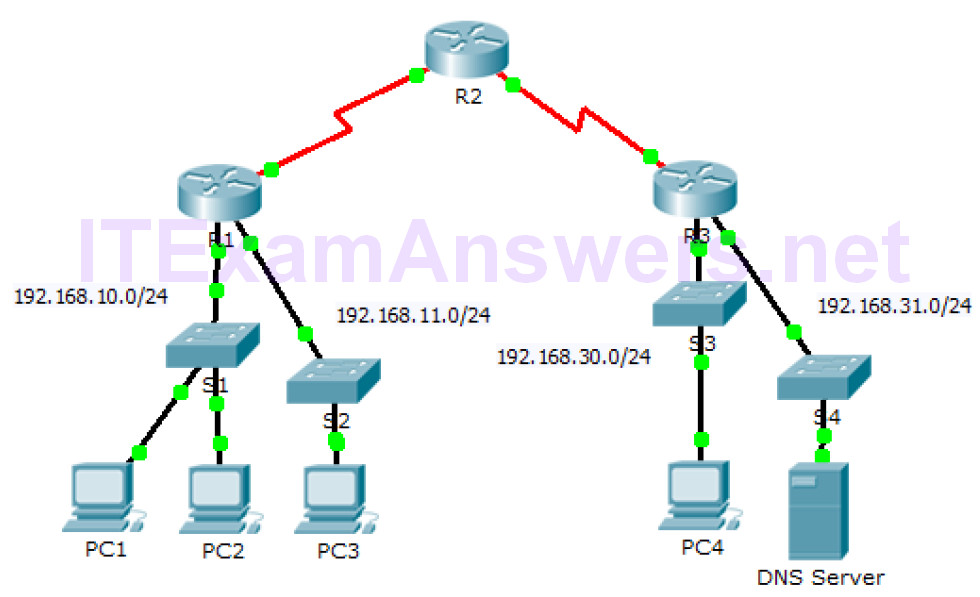
Topology Objectives Part 1: Verify Local Connectivity and Test Access Control List Part 2: Remove Access Control List and Repeat Test Background In this activity, you…
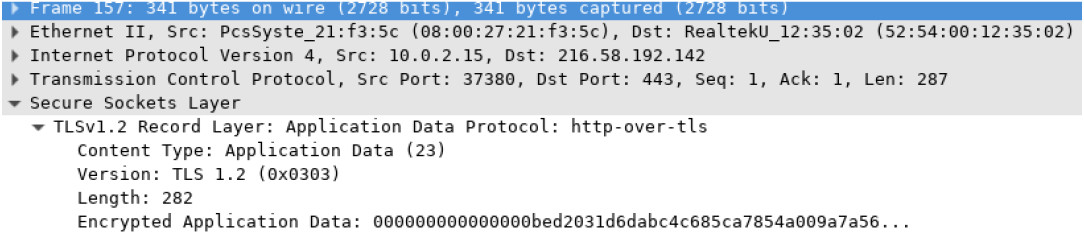
Objectives Part 1: Capture and view HTTP traffic Part 2: Capture and view HTTPS traffic Background / Scenario HyperText Transfer Protocol (HTTP) is an application layer…
Topology – Part 1 (FTP) Part 1 will highlight a TCP capture of an FTP session. This topology consists of the CyberOps Workstation VM with Internet…
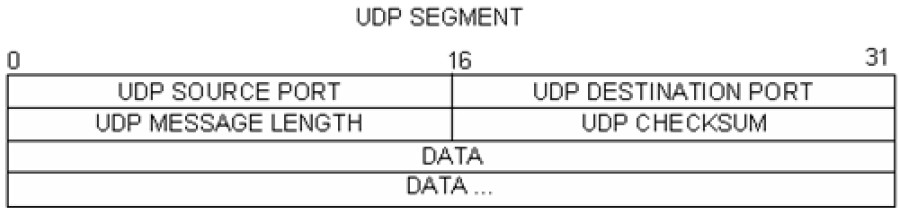
Topology Objectives Part 1: Record a PC’s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or…