More Questions: Network Security ( Version 1) – Network Security 1.0 Final Exam 1. In the video that describes the anatomy of an attack, a threat…
Browsing: Uncategorized
More Questions: Modules 1 – 4: Securing Networks Group Exam Answers 1. Which two statements describe access attacks? (Choose two.) Password attacks can be implemented by…
27.2.16 Lab – Investigating an Attack on a Windows Host (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the…
28.4.13 Lab – Incident Handling (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Objectives Apply…
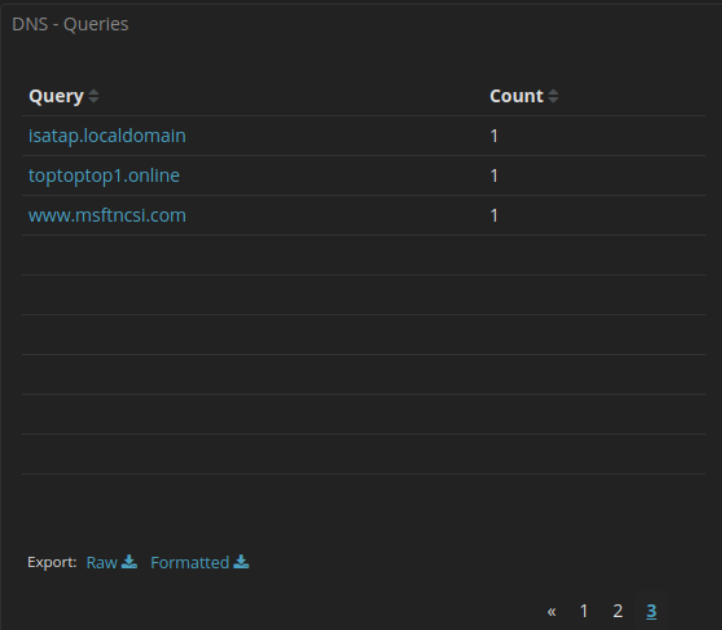
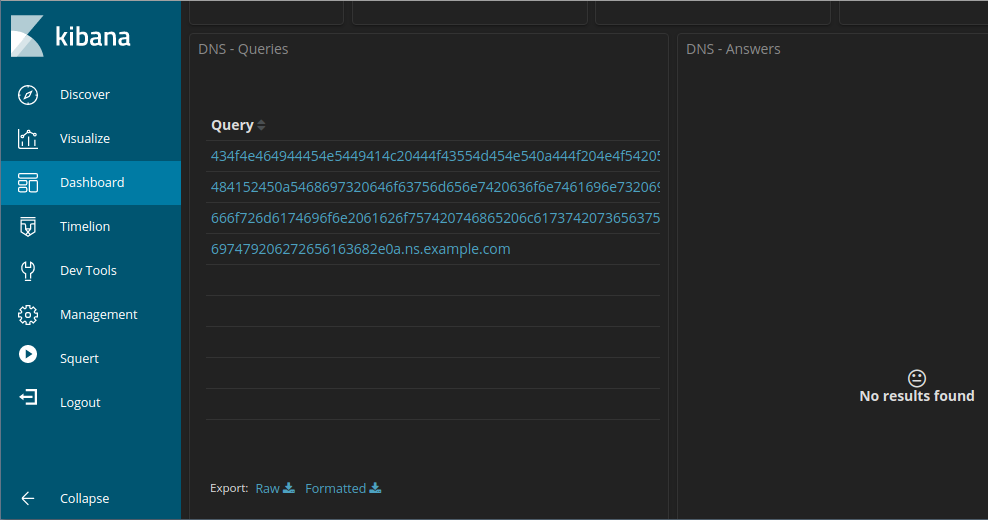
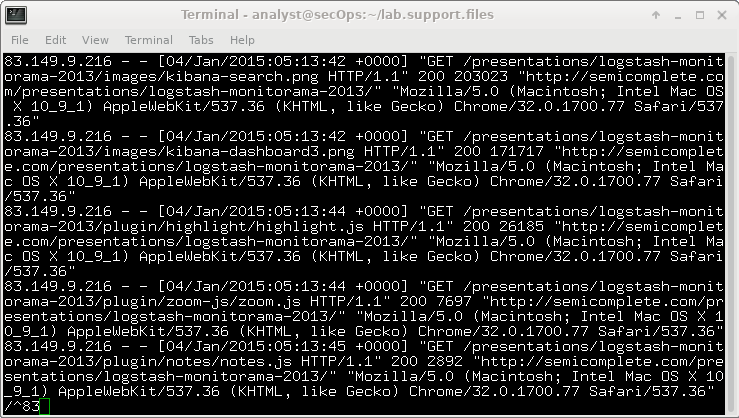
27.2.12 Lab – Interpret HTTP and DNS Data to Isolate Threat Actor (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears…
27.1.5 Lab – Convert Data into a Universal Format (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor…
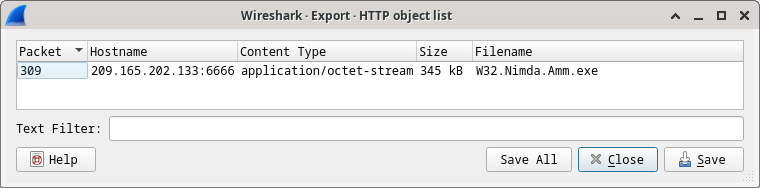
27.2.10 Lab – Extract an Executable from a PCAP (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor…
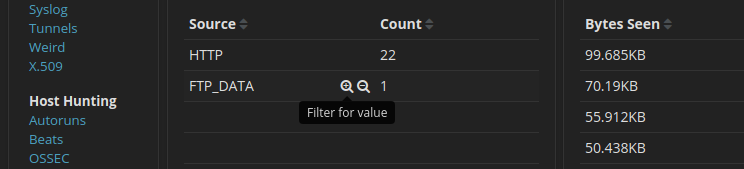
27.2.14 Lab – Isolate Compromised Host Using 5-Tuple (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy…
27.2.9 Lab – Regular Expression Tutorial (Instructor Version) Objectives In this lab, you will learn how to use regular expressions to search for desired strings of…