CyberOps Associate (Version 1.0) – Modules 26 – 28: Analyzing Security Data Group Exam
1. When real-time reporting of security events from multiple sources is being received, which function in SIEM provides capturing and processing of data in a common format?
- normalization
- aggregation
- compliance
- log collection
2. What is the value of file hashes to network security investigations?
- They ensure data availability.
- They assure nonrepudiation.
- They can serve as malware signatures.
- They offer confidentiality.
3. Which technology is an open source SIEM system?
- StealthWatch
- Wireshark
- Splunk
- ELK
4. A threat actor has successfully breached the network firewall without being detected by the IDS system. What condition describes the lack of alert?
- false negative
- true negative
- true positive
- false positive
5. What information is contained in the options section of a Snort rule?
- direction of traffic flow
- text describing the event
- action to be taken
- source and destination address
6. Match the intrusion event defined in the Diamond Model of intrusion to the description.
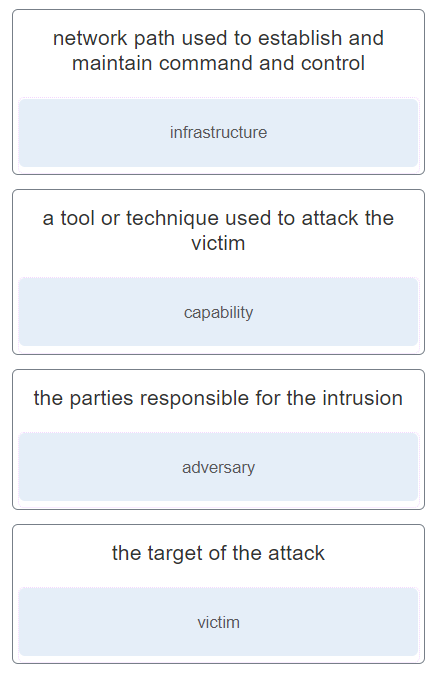
- network path used to establish and maintain command and control : infrastructure
- a tool or technique used to attack the victim : capability
- the parties responsible for the intrusion : adversary
- the target of the attack : victim
7. What two shared sources of information are included within the MITRE ATT&CK framework? (Choose two.)
- collection of digital evidence from most volatile evidence to least volatile
- attacker tactics, techniques, and procedures
- details about the handling of evidence including times, places, and personnel involved
- eyewitness evidence from someone who directly observed criminal behavior
- mapping the steps in an attack to a matrix of generalized tactics
8. What information is gathered by the CSIRT when determining the scope of a security incident?
- the networks, systems, and applications affected by an incident
- the amount of time and resources needed to handle an incident
- the strategies and procedures used for incident containment
- the processes used to preserve evidence
9. According to NIST standards, which incident response stakeholder is responsible for coordinating an incident response with other stakeholders to minimize the damage of an incident?
- human resources
- legal department
- management
- IT support
10. According to NIST, which step in the digital forensics process involves drawing conclusions from data?
- reporting
- collection
- examination
- analysis
11. A cybersecurity analyst has been called to a crime scene that contains several technology items including a computer. Which technique will be used so that the information found on the computer can be used in court?
- Tor
- rootkit
- unaltered disk image
- log collection
12. In which phase of the NIST incident response life cycle is evidence gathered that can assist subsequent investigations by authorities?
- postincident activities
- detection and analysis
- preparation
- containment, eradication, and recovery
13. When dealing with security threats and using the Cyber Kill Chain model, which two approaches can an organization use to block a potential back door creation? (Choose two.)
- Audit endpoints to discover abnormal file creations.
- Establish an incident response playbook.
- Consolidate the number of Internet points of presence.
- Conduct damage assessment.
- Use HIPS to alert or place a block on common installation paths.
14. What is defined in the SOP of a computer security incident response capability (CSIRC)?
- the details on how an incident is handled
- the procedures that are followed during an incident response
- the metrics for measuring incident response capabilities
- the roadmap for increasing incident response capabilities
15. How does an application program interact with the operating system?
- sending files
- accessing BIOS or UEFI
- making API calls
- using processes
16. Which tool included in the Security Onion provides a visual interface to NSM data?
- Curator
- Beats
- Squert
- OSSEC
17. Which tool included in the Security Onion includes the capability of designing custom dashboards?
- Sguil
- Kibana
- Squert
- OSSEC
18. How is the hash value of files useful in network security investigations?
- It is used to decode files.
- It helps identify malware signatures.
- It verifies confidentiality of files.
- It is used as a key for encryption.
19. Which technology is a major standard consisting of a pattern of symbols that describe data to be matched in a query?
- OSSEC
- POSIX
- Squert
- Sguil
20. Which tool is a Security Onion integrated host-based intrusion detection system?
- Snort
- OSSEC
- ELK
- Sguil
21. Which term is used to describe the process of converting log entries into a common format?
- classification
- systemization
- normalization
- standardization
22. What is the purpose for data normalization?
- to simplify searching for correlated events
- to reduce the amount of alert data
- to enhance the secure transmission of alert data
- to make the alert data transmission fast
23. Which personnel in a SOC is assigned the task of verifying whether an alert triggered by monitoring software represents a true security incident?
- SOC Manager
- Tier 3 personnel
- Tier 2 personnel
- Tier 1 personnel
24. Refer to the exhibit. A security analyst is reviewing an alert message generated by Snort. What does the number 2100498 in the message indicate?

- the id of the user that triggers the alert
- the message length in bits
- the Snort rule that is triggered
- the session number of the message
25. What are security event logs commonly based on when sourced by traditional firewalls?
- static filtering
- application analysis
- signatures
- 5-tuples
26. What is the purpose for data reduction as it relates to NSM?
- to make the alert data transmission fast
- to remove recurring data streams
- to enhance the secure transmission of alert data
- to diminish the quantity of NSM data to be handled
27. Why would threat actors prefer to use a zero-day attack in the Cyber Kill Chain weaponization phase?
- to avoid detection by the target
- to launch a DoS attack toward the target
- to get a free malware package
- to gain faster delivery of the attack on the target
28. What is the objective the threat actor in establishing a two-way communication channel between the target system and a CnC infrastructure?
- to allow the threat actor to issue commands to the software that is installed on the target
- to send user data stored on the target to the threat actor
- to steal network bandwidth from the network where the target is located
- to launch a buffer overflow attack
29. Which meta-feature element in the Diamond Model describes information gained by the adversary?
- methodology
- resources
- results
- direction
30. In which step of the NIST incident response process does the CSIRT perform an analysis to determine which networks, systems, or applications are affected; who or what originated the incident; and how the incident is occurring?
- incident notification
- attacker identification
- scoping
- detection
31. What is indicated by a Snort signature ID that is below 3464?
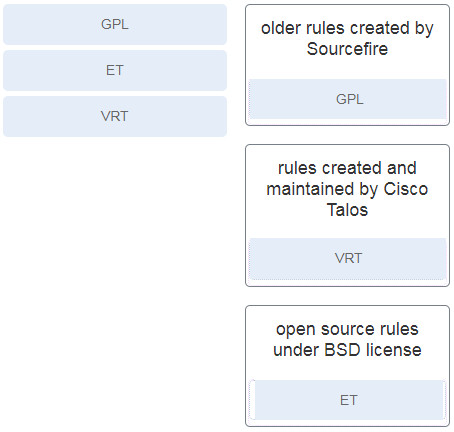
- The SID was created by Sourcefire and distributed under a GPL agreement.
- This is a custom signature developed by the organization to address locally observed rules.
- The SID was created by the Snort community and is maintained in Community Rules.
- The SID was created by members of EmergingThreats.
32. After a security monitoring tool identifies a malware attachment entering the network, what is the benefit of performing a retrospective analysis?
- A retrospective analysis can help in tracking the behavior of the malware from the identification point forward.
- It can identify how the malware originally entered the network.
- It can calculate the probability of a future incident.
- It can determine which network host was first affected.
33. Which classification indicates that an alert is verified as an actual security incident?
- false negative
- true positive
- false positive
- true negative
34. A network administrator is trying to download a valid file from an internal server. However, the process triggers an alert on a NMS tool. What condition describes this alert?
- false negative
- false positive
- true negative
- true positive
True Positive: The alert has been verified to be an actual security incident.
False Positive: The alert does not indicate an actual security incident. Benign activity that results in a false positive is sometimes referred to as a benign trigger.
An alternative situation is that an alert was not generated. The absence of an alert can be classified as:
True Negative: No security incident has occurred. The activity is benign.
False Negative: An undetected incident has occurred.
35. A threat actor collects information from web servers of an organization and searches for employee contact information. The information collected is further used to search personal information on the Internet. To which attack phase do these activities belong according to the Cyber Kill Chain model?
- action on objectives
- exploitation
- reconnaissance
- weaponization
36. Which HIDS is integrated into the Security Onion and uses rules to detect changes in host-based operating parameters caused by malware through system calls?
- OSSEC
- Bro
- Snort
- Suricata
37. Which type of events should be assigned to categories in Sguil?
- false positive
- true positive
- false negative
- true negative
38. A cybersecurity analyst is going to verify security alerts using the Security Onion. Which tool should the analyst visit first?
- Bro
- Sguil
- CapME
- ELK
39. Refer to the exhibit. Which field in the Sguil application window indicates the priority of an event or set of correlated events?
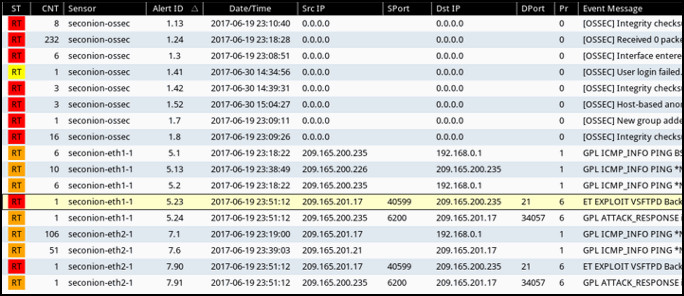
- ST
- AlertID
- Pr
- CNT
40. Match the Snort rule source to the description.