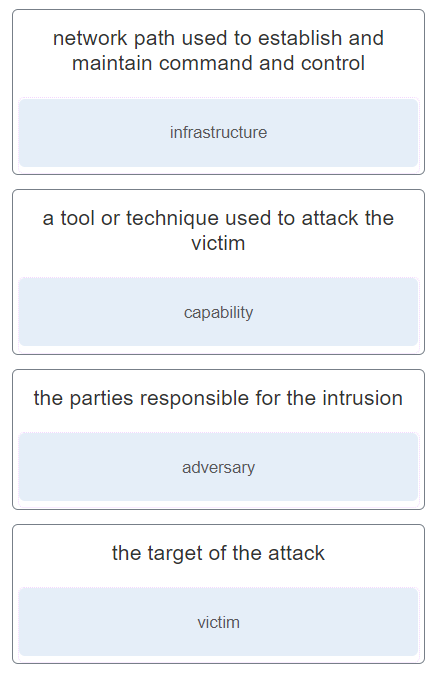
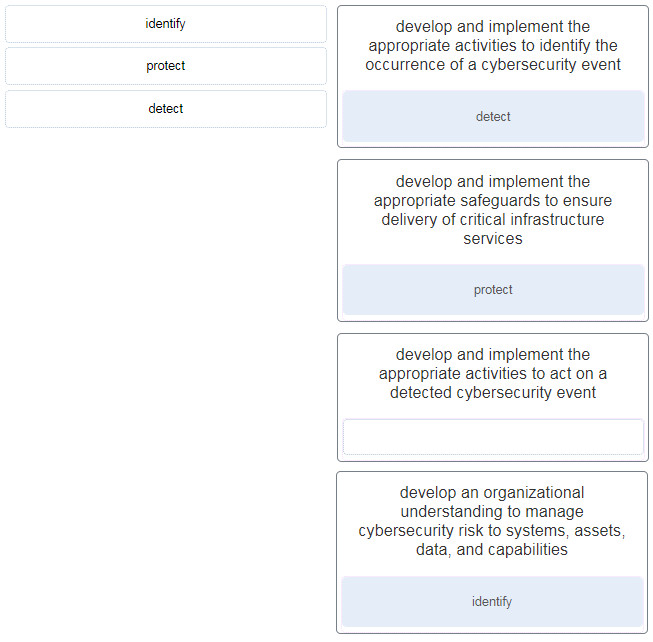
Objectives Research and analyze cyber security incidents Background / Scenario Governments, businesses, and individual users are increasingly the targets of cyberattacks and experts predict that these attacks are likely to increase in the future. Cybersecurity education is a top international priority as high-profile cyber-security related incidents raise the fear that attacks could threaten the global economy. The Center for Strategic and International Studies estimates that the cost of cybercrime to the global economy is more than $400 billion annually and in the United State alone as many as 3000 companies had their systems compromised in 2013. In this lab you…
Author: CCNA Security
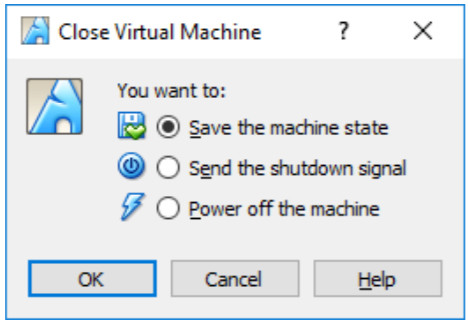
Objectives Part 1: Prepare a Personal Computer for Virtualization Part 2: Import a Virtual Machine into VirtualBox Inventory Background / Scenario Computing power and resources have increased tremendously over the last 10 years. A benefit of having multicore processors and large amounts of RAM is the ability to use virtualization. With virtualization, one or more virtual computers operate inside one physical computer. Virtual computers that run within physical computers are called virtual machines. Virtual machines are often called guests, and physical computers are often called hosts. Anyone with a modern computer and operating system can run virtual machines. A virtual…
CyberOps Associate (Version 1.0) – Modules 26 – 28: Analyzing Security Data Group Exam 1. When real-time reporting of security events from multiple sources is being received, which function in SIEM provides capturing and processing of data in a common format? normalization aggregation compliance log collection 2. What is the value of file hashes to network security investigations? They ensure data availability. They assure nonrepudiation. They can serve as malware signatures. They offer confidentiality. 3. Which technology is an open source SIEM system? StealthWatch Wireshark Splunk ELK 4. A threat actor has successfully breached the network firewall without being detected…
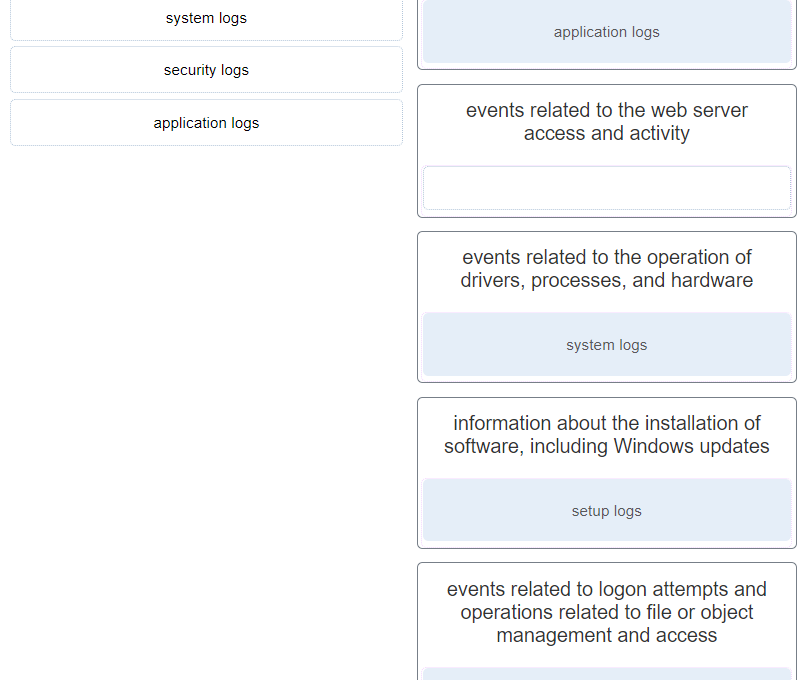
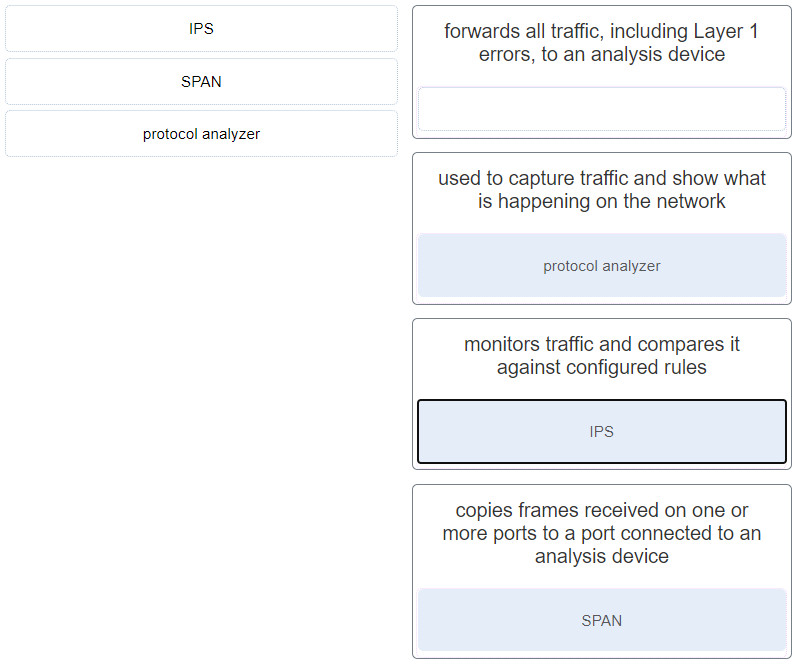
CyberOps Associate (Version 1.0) – Modules 24 – 25: Protocols and Log Files Group Exam 1. What is a feature of the tcpdump tool? It provides real-time reporting and long-term analysis of security events. It records metadata about packet flows. It uses agents to submit host logs to centralized management servers. It can display packet captures in real time or write them to a file. 2. Which Windows tool can be used to review host logs? Services Event Viewer Task Manager Device Manager 3. Which type of security data can be used to describe or predict network behavior? alert transaction…
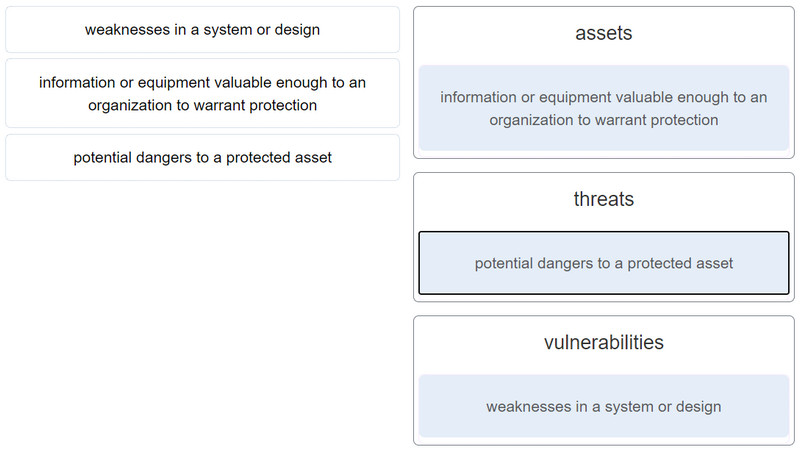
CyberOps Associate (Version 1.0) – Modules 21 – 23: Cryptography and Endpoint Protection Group Exam 1. Which technology might increase the security challenge to the implementation of IoT in an enterprise environment? network bandwidth cloud computing CPU processing speed data storage 2. Which statement describes the term attack surface? It is the total number of attacks toward an organization within a day. It is the group of hosts that experiences the same attack. It is the total sum of vulnerabilities in a system that is accessible to an attacker. It is the network interface where attacks originate. 3. Which HIDS…
CyberOps Associate (Version 1.0) – Modules 18 – 20: Network Defense Group Exam 1. How does BYOD change the way in which businesses implement networks? BYOD requires organizations to purchase laptops rather than desktops. BYOD provides flexibility in where and how users can access network resources. BYOD users are responsible for their own network security, thus reducing the need for organizational security policies. BYOD devices are more expensive than devices that are purchased by an organization. 2. Which type of business policy establishes the rules of conduct and the responsibilities of employees and employers? employee data company security 3. What…
CyberOps Associate (Version 1.0) – Modules 13 – 17: Threats and Attacks Group Exam 1. Which is an example of social engineering? an unidentified person claiming to be a technician collecting user information from employees the infection of a computer by a virus carried by a Trojan an anonymous programmer directing a DDoS attack on a data center a computer displaying unauthorized pop-ups and adware 2. What is a significant characteristic of virus malware? A virus is triggered by an event on the host system. Virus malware is only distributed over the Internet. A virus can execute independently of the…
CyberOps Associate (Version 1.0) – Modules 11 – 12: Network Infrastructure Security Group Exam 1. For which discovery mode will an AP generate the most traffic on a WLAN? passive mode mixed mode active mode open mode 2. Which parameter is commonly used to identify a wireless network name when a home wireless AP is being configured? ad hoc SSID BESS ESS 3. Which two protocols are considered distance vector routing protocols? (Choose two.) ISIS RIP BGP EIGRP OSPF 4. Which AAA component can be established using token cards? authentication accounting authorization auditing Explanation: The authentication component of AAA is…
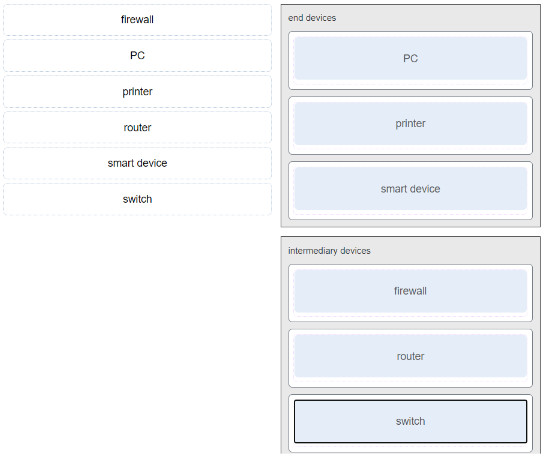
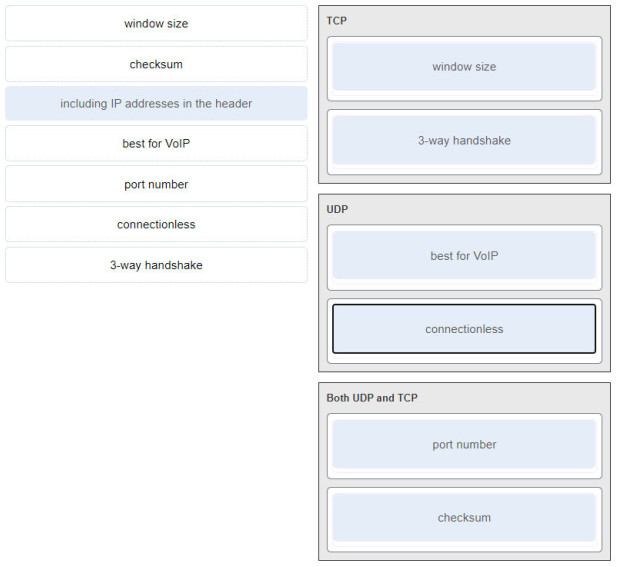
CyberOps Associate (Version 1.0) – Modules 5 – 10: Network Fundamentals Group Exam 1. A host is transmitting a broadcast. Which host or hosts will receive it? the closest neighbor on the same network all hosts in the same network all hosts on the Internet a specially defined group of hosts 2. Which statement describes a characteristic of cloud computing? Applications can be accessed over the Internet by individual users or businesses using any device, anywhere in the world. Devices can connect to the Internet through existing electrical wiring. Investment in new infrastructure is required in order to access the…