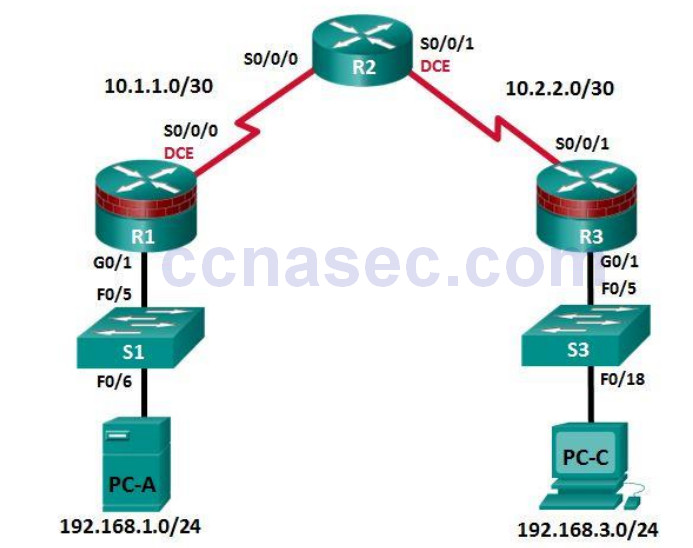
Lab – Configure an Intrusion Prevention System (IPS) (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology IP Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 G0/1 192.168.1.1 255.255.255.0 N/A S1 F0/5 S0/0/0 (DCE) 10.1.1.1 255.255.255.252 N/A N/A R2 S0/0/0 10.1.1.2 255.255.255.252 N/A N/A S0/0/1 (DCE) 10.2.2.2 255.255.255.252 N/A N/A R3 G0/1 192.168.3.1 255.255.255.0 N/A S3 F0/5 S0/0/1 10.2.2.1 255.255.255.252 N/A N/A PC-A NIC 192.168.1.3 255.255.255.0 192.168.1.1 S1 F0/6 PC-C NIC 192.168.3.3 255.255.255.0 192.168.3.1 S3 F0/18 Objectives Part 1: Configure Basic Router Settings ♦ …
Author: CCNA Security
CCNA Security Certification Practice Answers What type of algorithms require sender and receiver to exchange a secret key that is used to ensure the confidentiality of messages? symmetric algorithms* public key algorithms hashing algorithms asymmetric algorithms Symmetric algorithms use the same key, a secret key, to encrypt and decrypt data. This key must be pre-shared before communication can occur. Asymmetric algorithms require more processing power and overhead on the communicating devices because these keys can be long in order to avoid being hacked. A network administrator is configuring an AAA server to manage TACACS+ authentication. What are two attributes…
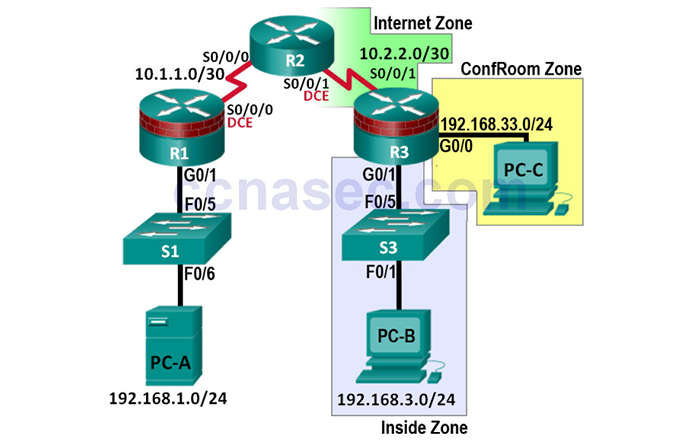
Lab – Configuring Zone-Based Policy Firewalls (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Note: ISR G1 devices have Fast Ethernet interfaces instead of Gigabit Ethernet Interfaces. NETLAB+ Note: PC-B is actually connected to port F0/18 on Switch 2. Switch 2 and S3 are connected using F0/3 and F0/1, respectively. All interfaces on Switch 2 should be Administratvily disabled except F0/1 and F0/18. IP Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 G0/1 192.168.1.1 255.255.255.0 N/A S1 F0/5 S0/0/0 (DCE) 10.1.1.1 255.255.255.252 N/A…
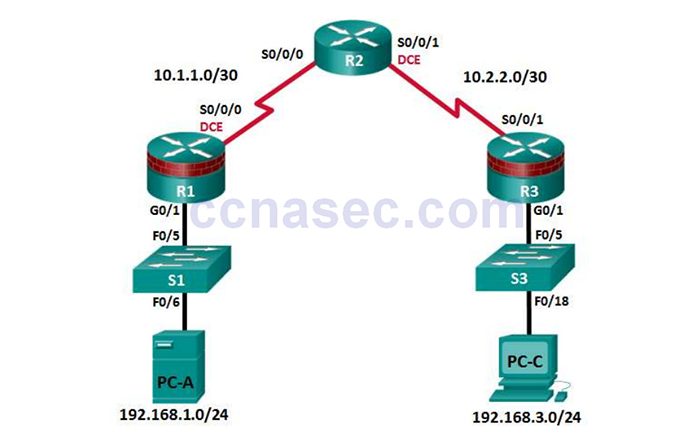
Lab – Securing Administrative Access Using AAA and RADIUS (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 G0/1 192.168.1.1 255.255.255.0 N/A S1 F0/5 S0/0/0 (DCE) 10.1.1.1 255.255.255.252 N/A N/A R2 S0/0/0 10.1.1.2 255.255.255.252 N/A N/A S0/0/1 (DCE) 10.2.2.2 255.255.255.252 N/A N/A R3 G0/1 192.168.3.1 255.255.255.0 N/A S3 F0/5 S0/0/1 10.2.2.1 255.255.255.252 N/A N/A PC-A NIC 192.168.1.3 255.255.255.0 192.168.1.1 S1 F0/6 PC-C NIC 192.168.3.3 255.255.255.0…
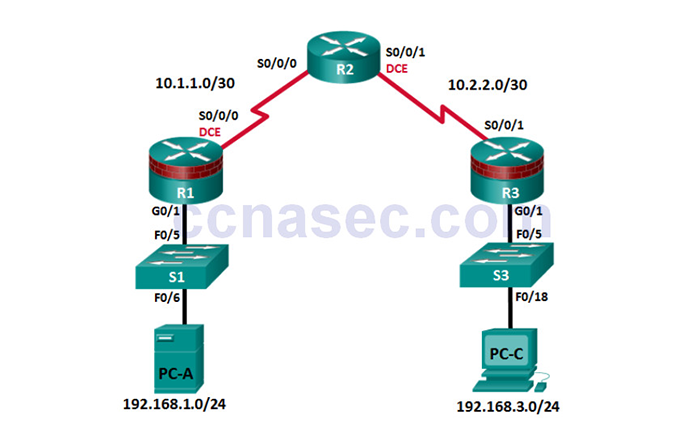
Lab – Securing the Router for Administrative Access (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. IP Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 G0/1 192.168.1.1 255.255.255.0 N/A S1 F0/5 S0/0/0 (DCE) 10.1.1.1 255.255.255.252 N/A N/A R2 S0/0/0 10.1.1.2 255.255.255.252 N/A N/A S0/0/1 (DCE) 10.2.2.2 255.255.255.252 N/A N/A R3 G0/1 192.168.3.1 255.255.255.0 N/A S3 F0/5 S0/0/1 10.2.2.1 255.255.255.252 N/A N/A PC-A NIC 192.168.1.3 255.255.255.0 192.168.1.1 S1 F0/6 PC-C NIC 192.168.3.3 255.255.255.0…
Lab – Researching Network Attacks and Security Audit Tools/Attack Tools (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Objectives Part 1: Researching Network Attacks Research network attacks that have occurred. Select a network attack and develop a report for presentation to the class. Part 2: Researching Network Security Audit Tools and Attack Tools Research network security audit tools. Select a tool and develop a report for presentation to the class. Background / Scenario Attackers have developed many tools over the years to attack and compromise networks. These attacks take…
Lab – Social Engineering (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Objective In this lab, you will research examples of social engineering and identify ways to recognize and prevent it. Resources Computer with Internet Access Step 1: Research Social Engineering Examples Social engineering, as it relates to information security, is used to describe the techniques used by a person (or persons) who manipulate people in order to access or compromise information about an organization or its computer systems. A social engineer is usually difficult to identify and may…
Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. IP Addressing Table Device Interface IP Address Subnet Mask Default Gateway Switch Port R1 G0/0 209.165.200.225 255.255.255.248 N/A ASA E0/0 S0/0/0 (DCE) 10.1.1.1 255.255.255.252 N/A N/A R2 S0/0/0 10.1.1.2 255.255.255.252 N/A N/A S0/0/1 (DCE) 10.2.2.2 255.255.255.252 N/A N/A R3 G0/1 172.16.3.1 255.255.255.0 N/A S3 F0/5 S0/0/1 10.2.2.1 255.255.255.252 N/A N/A ASA VLAN 1 (E0/1) 192.168.1.1 255.255.255.0 N/A S2 F0/24 VLAN 2 (E0/0) 209.165.200.226 255.255.255.248 N/A R1 G0/0 VLAN 3 (E0/2) 192.168.2.1 255.255.255.0 N/A S1 F0/24 PC-A NIC 192.168.2.3 255.255.255.0 192.168.2.1 S1 F0/6 PC-B NIC 192.168.1.3 255.255.255.0 192.168.1.1 S2…
CCNA Security Practice Skills Assesement Part 2 CCNA Security PT Practice SA – Part 2 A few things to keep in mind while completing this activity: Do not use the browser Back button or close or reload any Exam windows during the exam. Do not close Packet Tracer when you are done. It will close automatically. Click the Submit Assessment button to submit your work. Introduction In this practice Packet Tracer Skills Based Assessment, you will: Configure basic ASA device hardening and secure network management Configure DHCP and NAT on the ASA device Configure the ASA firewall to implement security…