Objectives Apply your knowledge of security incident handling procedures to formulate questions about given incident scenarios. Background / Scenario Computer security incident response has become a vital part of any organization. The process for handling a security incident can be complicated and involve many different groups. An organization must have standards for responding to incidents in the form of policies, procedures, and checklists. To properly respond to a security incident, the security analyst must be trained to understand what to do, and must also follow all of the guidelines outlined by the organization. There are many resources available to help…
Author: CCNA Security
Topology Objectives In this lab, you will review logs during an exploitation of a documented vulnerability to determine the compromised hosts and file. Part 1: Prepare the Virtual Environment Part 2: Reconnaissance Part 3: Exploitation Part 4: Infiltration Part 5: Review the Logs Background / Scenario The 5-tuple is used by IT administrators to identify requirements for creating an operational and secure network environment. The components of the 5-tuple include a source IP address and port number, destination IP address and port number, and the protocol in use. In this lab, you will exploit a vulnerable server using known exploits.…
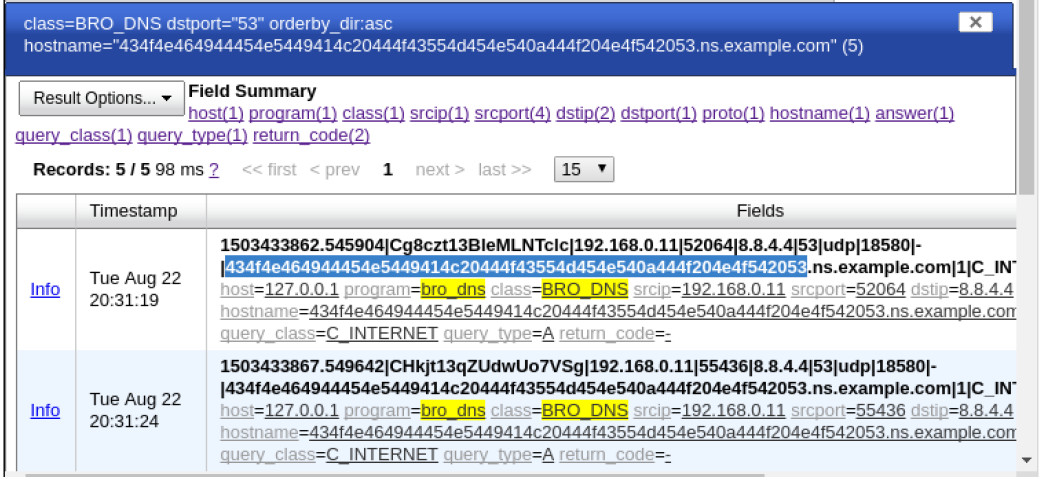
Topology Objectives In this lab, you will review logs during an exploitation of documented HTTP and DNS vulnerabilities. Part 1: Prepare the Virtual Environment Part 2: Investigate an SQL Injection Attack Part 3: Data Exfiltration Using DNS Background / Scenario MySQL is a popular database used by numerous web applications. Unfortunately, SQL injection is a common web hacking technique. It is a code injection technique where an attacker executes malicious SQL statements to control a web application’s database server. Domain name servers (DNS) are directories of domain names, and they translate the domain names into IP addresses. This service can…
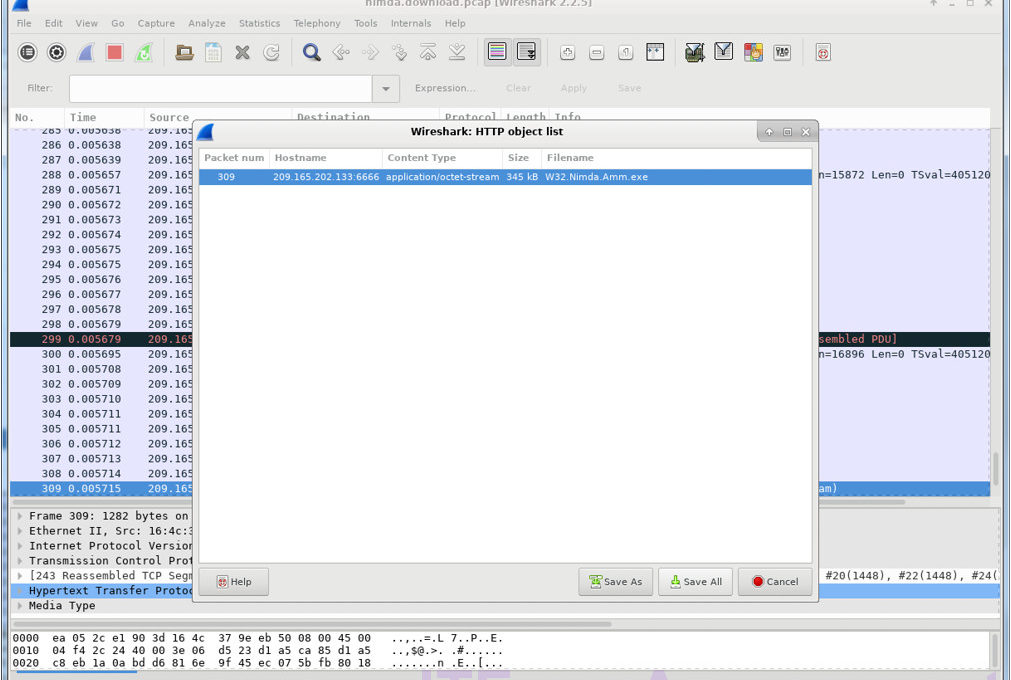
Objectives Part 1: Prepare the Virtual Environment Part 2: Analyze Pre-Captured Logs and Traffic Captures Background / Scenario Looking at logs is very important but it is also important to understand how network transactions happen at the packet level. In this lab, you will analyze the traffic in a previously captured pcap file and extract an executable from the file. Required Resources CyberOps Workstation VM Internet connection Part 1: Prepare the Virtual Environment a. Launch Oracle VirtualBox. Right-click CyberOps Workstion > Settings > Network. Besides Attached To, select Bridged Adapter, if necessary, and click OK. b. Log in to the…
Objectives In this lab, you will learn how to use regular expressions to search for desired strings of information. Background / Scenario A regular expression (regex) is a pattern of symbols that describes data to be matched in a query or other operation. Regular expressions are constructed similarly to arithmetic expressions, by using various operators to combine smaller expressions. There are two major standards of regular expression, POSIX and Perl. In this lab, you will use an online tutorial to explore regular expressions. You will also describe the information that matches given regular expressions. Required Resources CyberOps Workstation VM Internet…
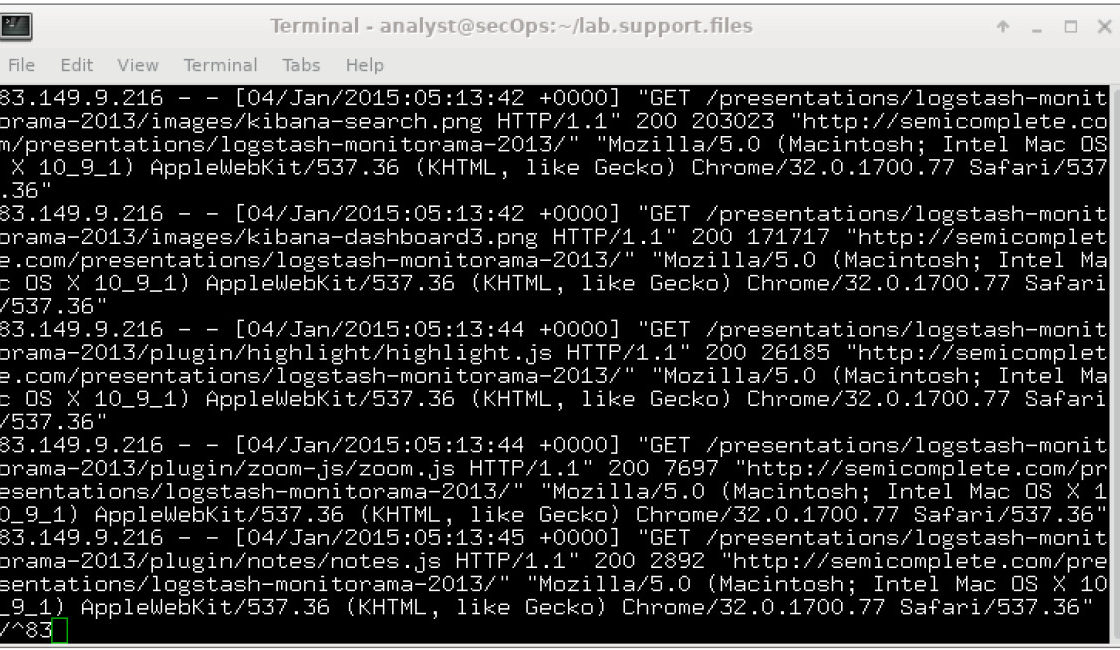
Objectives Part 1: Normalize Timestamps in a Log File Part 2: Normalize Timestamps in an Apache Log File Part 3: Log File Preparation in Security Onion Background / Scenario This lab will prepare students to learn where log files are located and how to manipulate and view log files. Log entries are generated by network devices, operating systems, applications, and various types of programmable devices. A file containing a time-sequenced stream of log entries is called a log file. By nature, log files record events that are relevant to the source. The syntax and format of data within log messages…
Topology Objectives Part 1: Preparing the Virtual Environment Part 2: Firewall and IDS Logs Part 3: Terminate and Clear Mininet Process Background / Scenario In a secure production network, network alerts are generated by various types of devices such as security appliances, firewalls, IPS devices, routers, switches, servers, and more. The problem is that not all alerts are created equally. For example, alerts generated by a server and alerts generated by a firewall will be different and vary in content and format. In this lab, to get familiar with firewall rules and IDS signatures you will: Perform live-monitoring of IDS…
Topology Objectives Part 1: Use syslog to capture log files from multiple network devices Part 2: Observe AAA user access logging Part 3: Observe NetFlow information Background / Scenario In this activity, you will use Packet Tracer to view network data generated by syslog, AAA, and NetFlow. Part 1: View Log Entries with Syslog Step 1: The syslog Server Syslog is a messaging system designed to support remote logging. Syslog clients send log entries to a syslog server. The syslog server concentrates and stores log entries. Packet Tracer supports basic syslog operations and can be used for demonstration. The network…
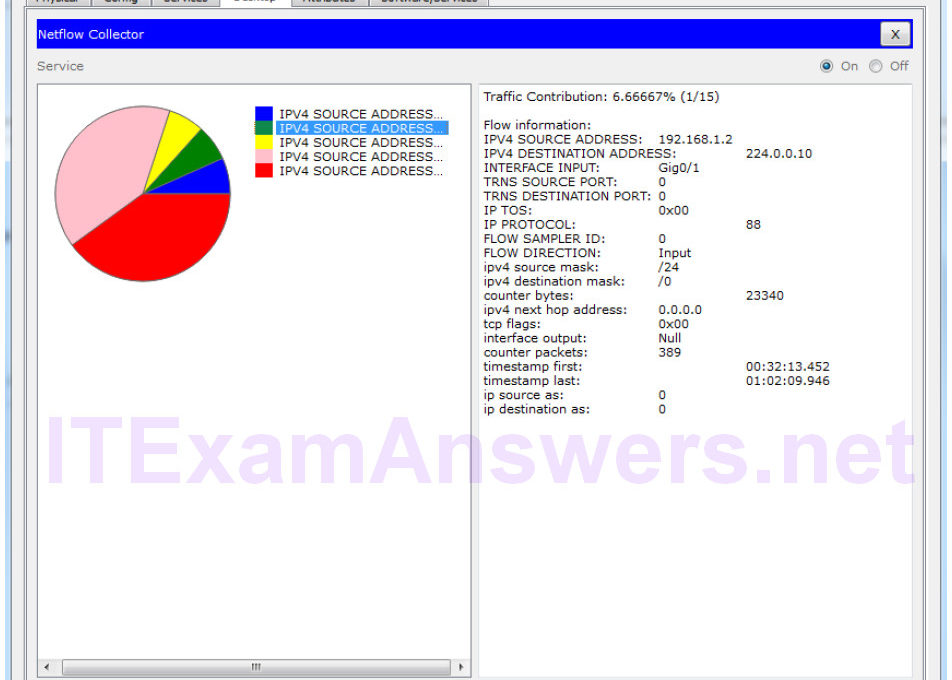
Topology Objectives Part 1: Observe NetFlow Flow Records – One Direction Part 2: Observe NetFlow Records for a Session that Enters and Leaves the Collector Background In this activity, you will use Packet Tracer to create network traffic and observe the corresponding NetFlow flow records in a NetFlow collector. Packet Tracer offers a basic simulation of NetFlow functionality. It is not a replacement for learning NetFlow on physical equipment. Some differences may exist between NetFlow flow records generated by Packet Tracer and by records created by full-featured network equipment. Part 1: Observe NetFlow Flow Records – One Direction Step 1:…