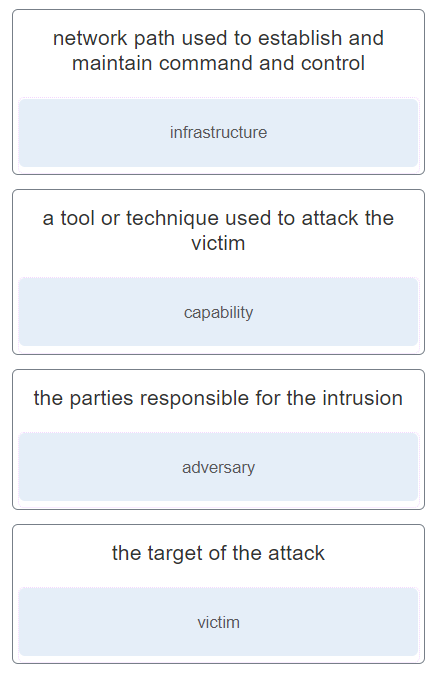
Objectives Research and analyze cyber security incidents Background / Scenario Governments, businesses, and individual users are increasingly the targets of cyberattacks and experts predict that these…
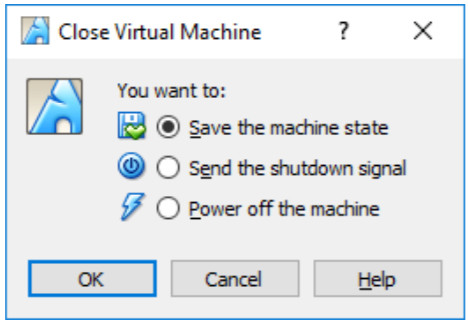
Objectives Part 1: Prepare a Personal Computer for Virtualization Part 2: Import a Virtual Machine into VirtualBox Inventory Background / Scenario Computing power and resources have…
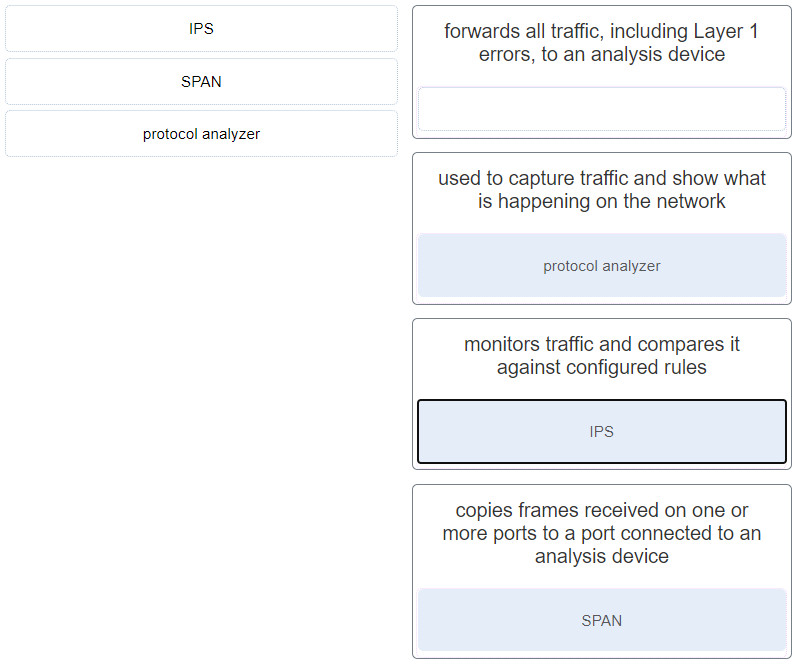
CyberOps Associate (Version 1.0) – Modules 26 – 28: Analyzing Security Data Group Exam 1. When real-time reporting of security events from multiple sources is being…
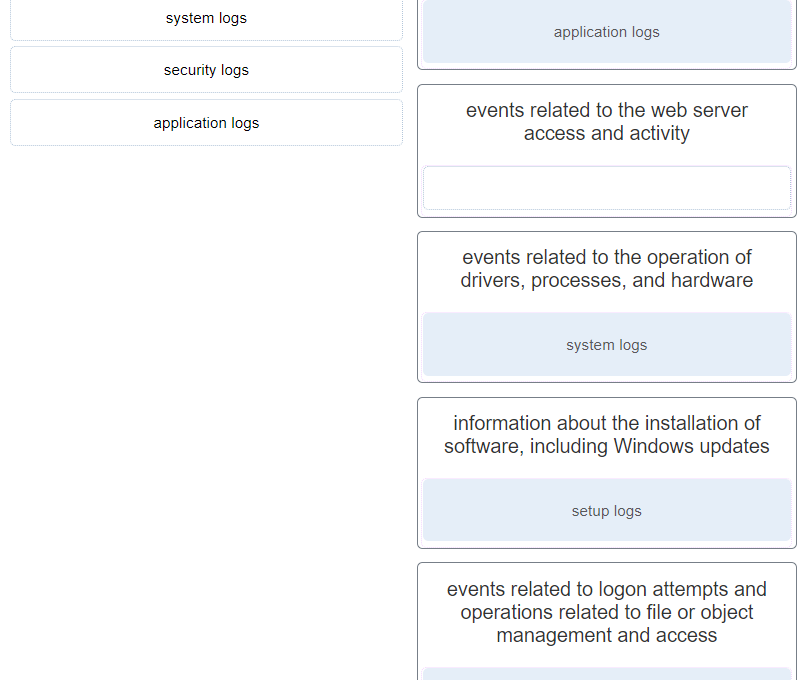
CyberOps Associate (Version 1.0) – Modules 24 – 25: Protocols and Log Files Group Exam 1. What is a feature of the tcpdump tool? It provides…
CyberOps Associate (Version 1.0) – Modules 21 – 23: Cryptography and Endpoint Protection Group Exam 1. Which technology might increase the security challenge to the implementation…
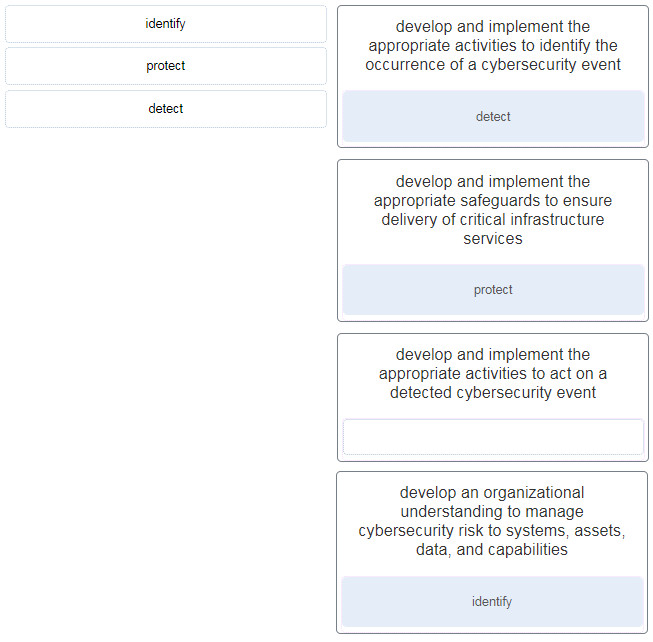
CyberOps Associate (Version 1.0) – Modules 18 – 20: Network Defense Group Exam 1. How does BYOD change the way in which businesses implement networks? BYOD…
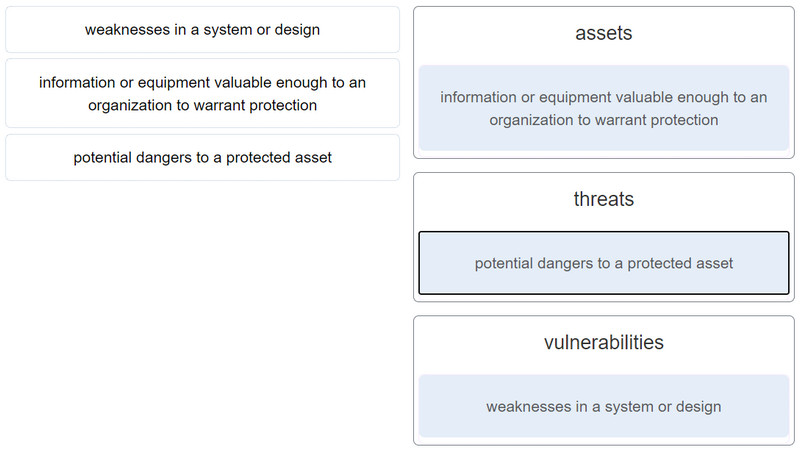
CyberOps Associate (Version 1.0) – Modules 13 – 17: Threats and Attacks Group Exam 1. Which is an example of social engineering? an unidentified person claiming…
CyberOps Associate (Version 1.0) – Modules 11 – 12: Network Infrastructure Security Group Exam 1. For which discovery mode will an AP generate the most traffic…
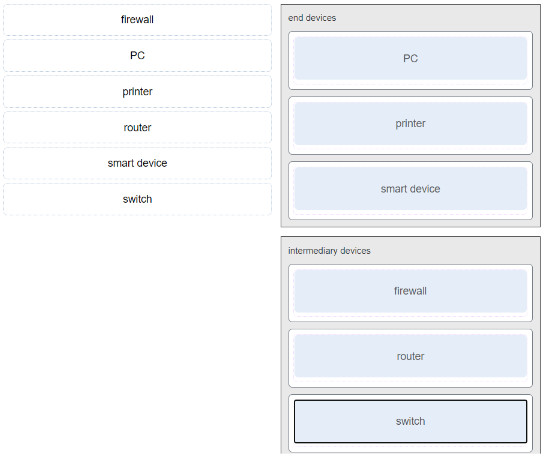
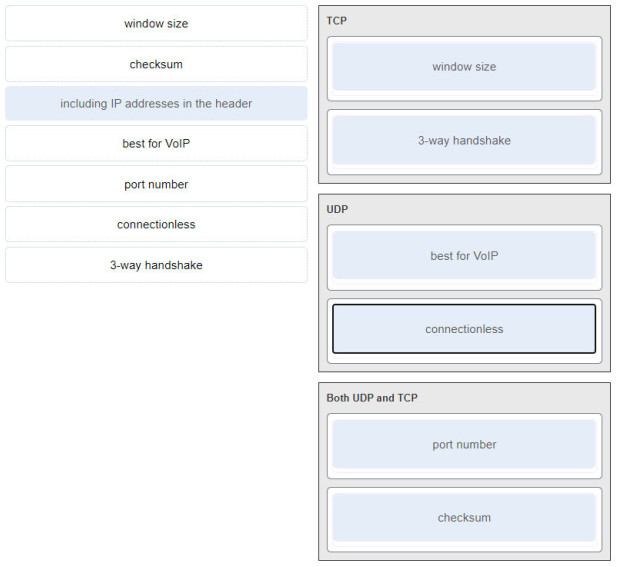
CyberOps Associate (Version 1.0) – Modules 5 – 10: Network Fundamentals Group Exam 1. A host is transmitting a broadcast. Which host or hosts will receive…