Objectives Apply your knowledge of security incident handling procedures to formulate questions about given incident scenarios. Background / Scenario Computer security incident response has become a…
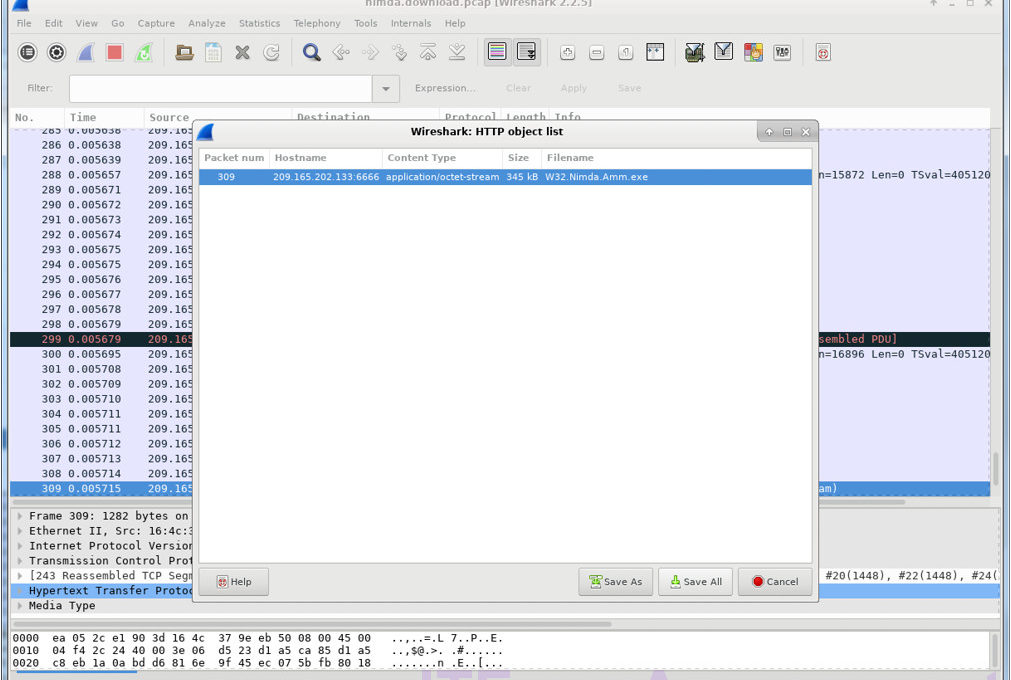
Topology Objectives In this lab, you will review logs during an exploitation of a documented vulnerability to determine the compromised hosts and file. Part 1: Prepare…
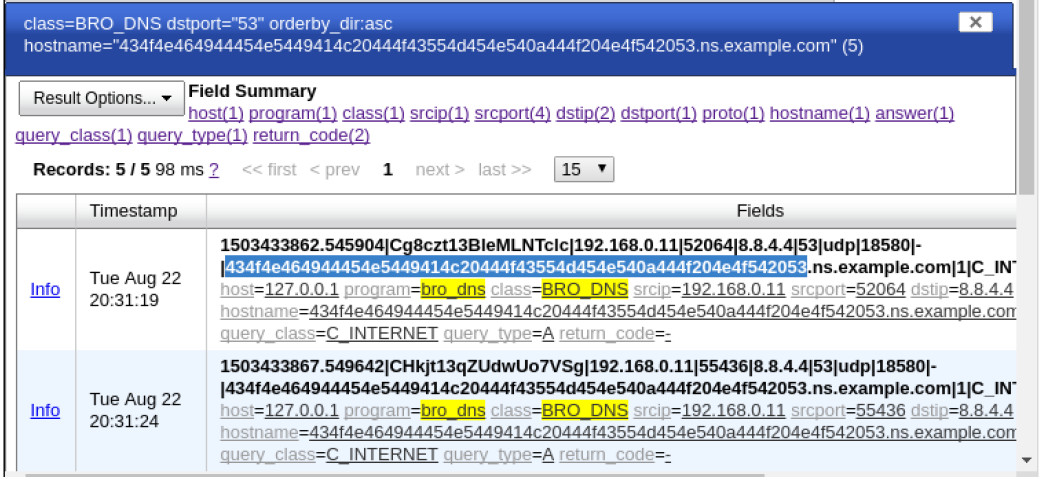
Topology Objectives In this lab, you will review logs during an exploitation of documented HTTP and DNS vulnerabilities. Part 1: Prepare the Virtual Environment Part 2:…
Objectives Part 1: Prepare the Virtual Environment Part 2: Analyze Pre-Captured Logs and Traffic Captures Background / Scenario Looking at logs is very important but it…
Objectives In this lab, you will learn how to use regular expressions to search for desired strings of information. Background / Scenario A regular expression (regex)…
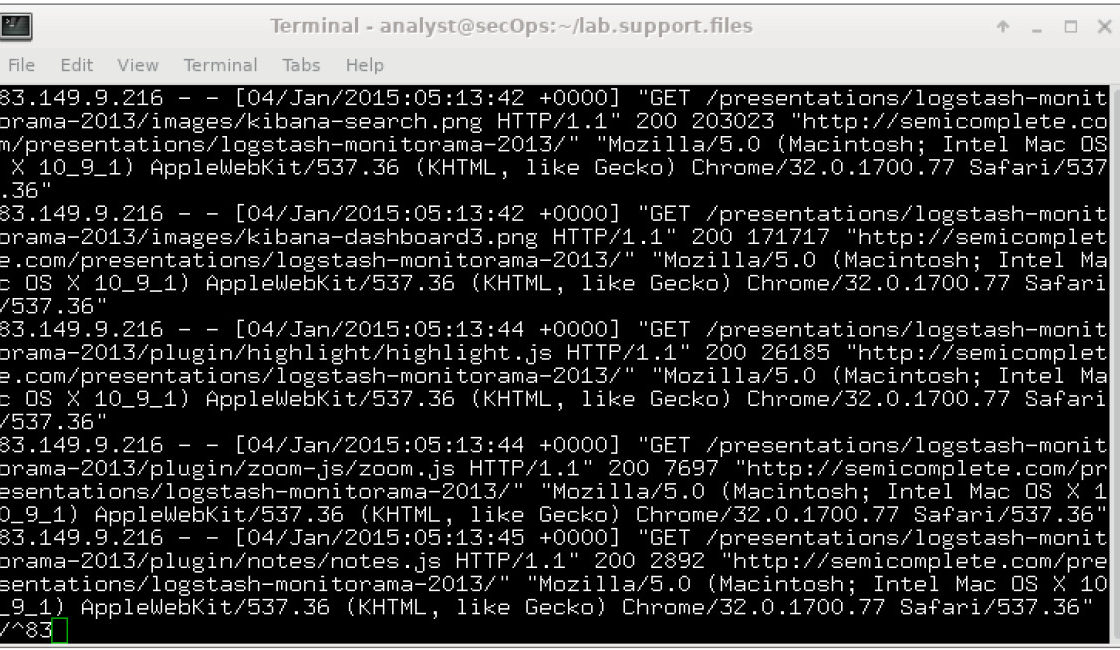
Objectives Part 1: Normalize Timestamps in a Log File Part 2: Normalize Timestamps in an Apache Log File Part 3: Log File Preparation in Security Onion…
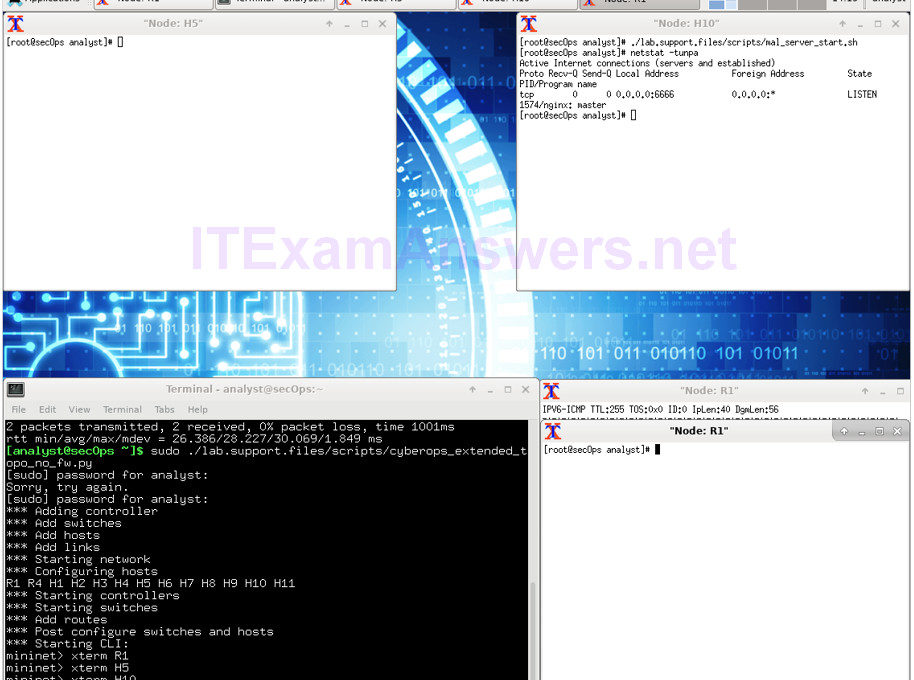
Topology Objectives Part 1: Preparing the Virtual Environment Part 2: Firewall and IDS Logs Part 3: Terminate and Clear Mininet Process Background / Scenario In a…
Topology Objectives Part 1: Use syslog to capture log files from multiple network devices Part 2: Observe AAA user access logging Part 3: Observe NetFlow information…
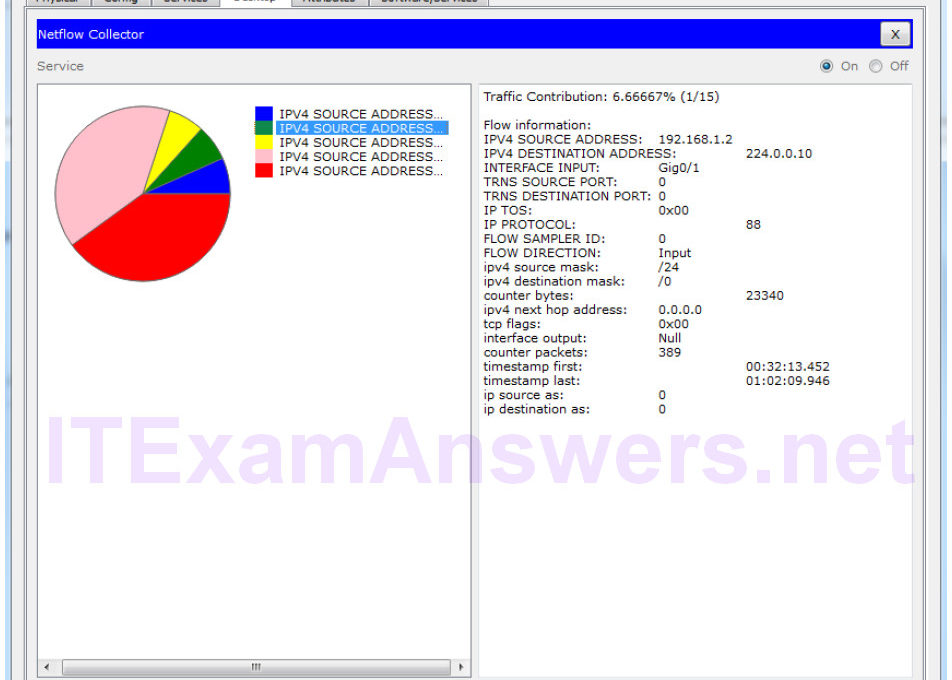
Topology Objectives Part 1: Observe NetFlow Flow Records – One Direction Part 2: Observe NetFlow Records for a Session that Enters and Leaves the Collector Background…